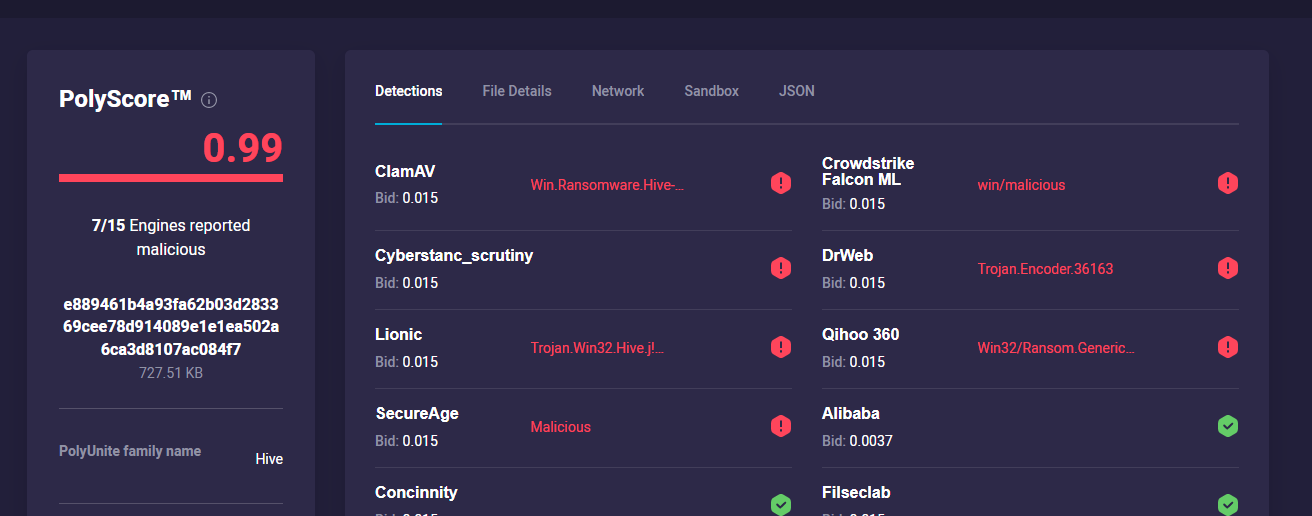
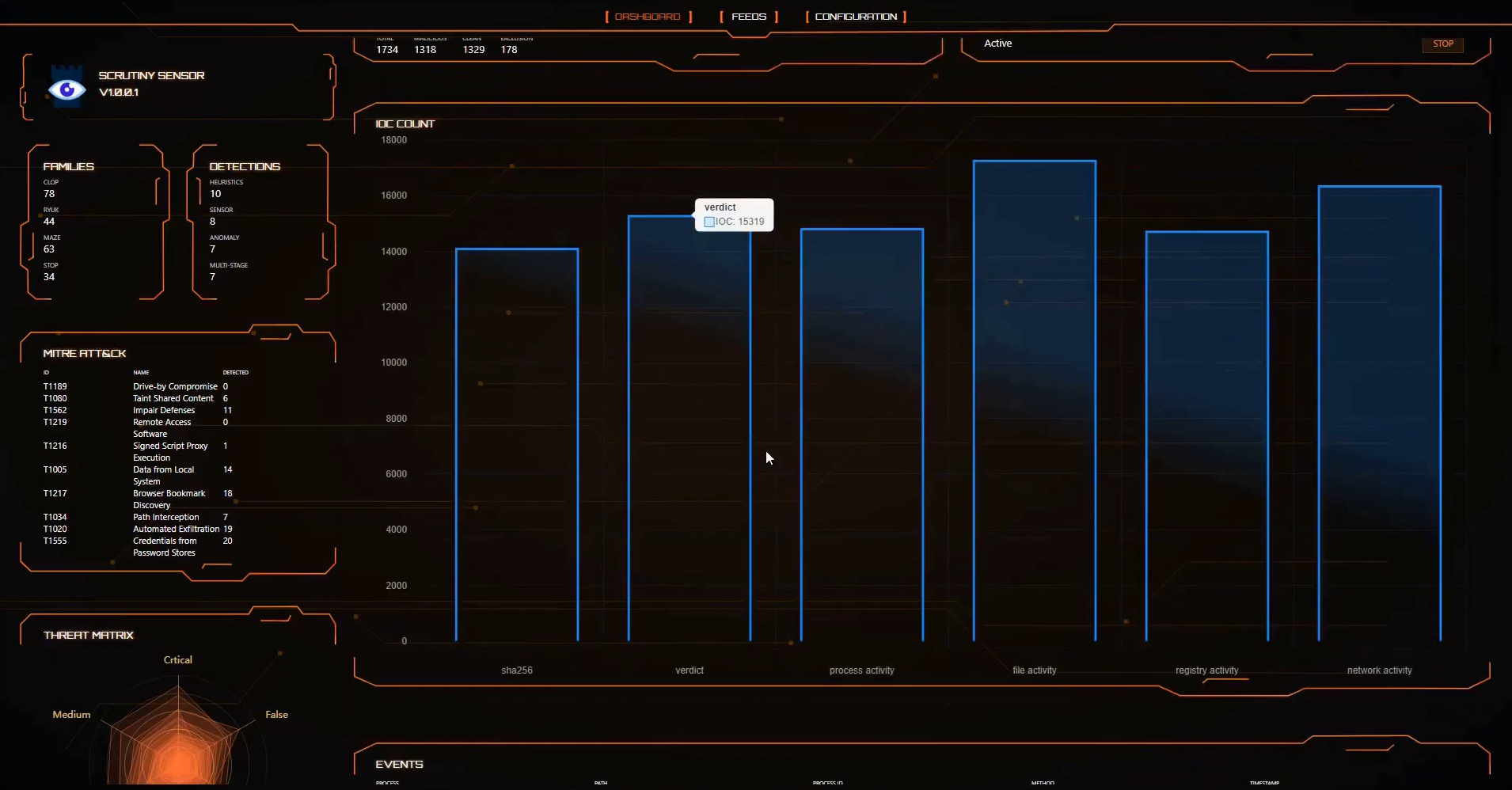
Scrutiny Engine










Disrupting the infection lifecycle, one threat at a time.
Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR) solutions are powerful tools that can help organizations detect and respond to cyber threats. However, it's important to understand that no single solution can provide 100% protection against all threats. Existing security solutions focus on identifying and stopping known and emerging threats on endpoints and other devices, but they can't cover every attack surface within an organization.
Additionally, cyber threats are constantly evolving and attackers are becoming more sophisticated, so even the best EDR/MDR solutions may not be able to detect every threat.
Malware attacks are increasing rapidly
Don't fall victim to the rising tide of malware
In recent years, there has been an increase in the number of malware attacks. This is due to a variety of reasons, including the proliferation of connected devices and the growing complexity of cyber threats.
No organization is immune to the growing threat of malware attacks.
The increasing volume of malware attacks is a growing concern as it is causing harm to organizations of all sizes and types, regardless of their location and industry. With the advancing tactics and technologies used by attackers, it becomes harder to stop all the malicious traffic.
Be proactive, not reactive
The indiscriminate nature of malware attacks means that any organization can be a target, regardless of its size or the industry it operates in. It is essential for organizations to have a proactive approach to security to protect themselves from these attacks, and be prepared with incident response plan and advanced threat detection solution like Scrutiny to detect and respond to the attacks effectively.
Fall short of protection ?
Traditional security solutions, while useful, have limitations in their ability to provide complete protection against all types of cyber threats. When these solutions fail, it can result in a number of negative consequences for an organization

Data breaches
if a threat is able to bypass traditional security solutions, it can result in sensitive data being compromised or stolen.

Business disruption
Cyber attacks can disrupt business operations
According to a study by Datto, a leading provider of data backup and disaster recovery solutions, in 2022 of all businesses that experienced a ransomware attack were forced to shut down permanently.

Damage to reputation
A data breach or cyber attack can damage an organization's reputation and trust with customers, partners, and stakeholders.

Financial Losses
Malware attacks can cause significant financial losses for organizations. According to a study by Cybersecurity Ventures, the cost of cyber crime is projected to reach $6 trillion annually by 2021. In addition, a study by Accenture found that the average cost of a data breach for a company is $3.86 million.
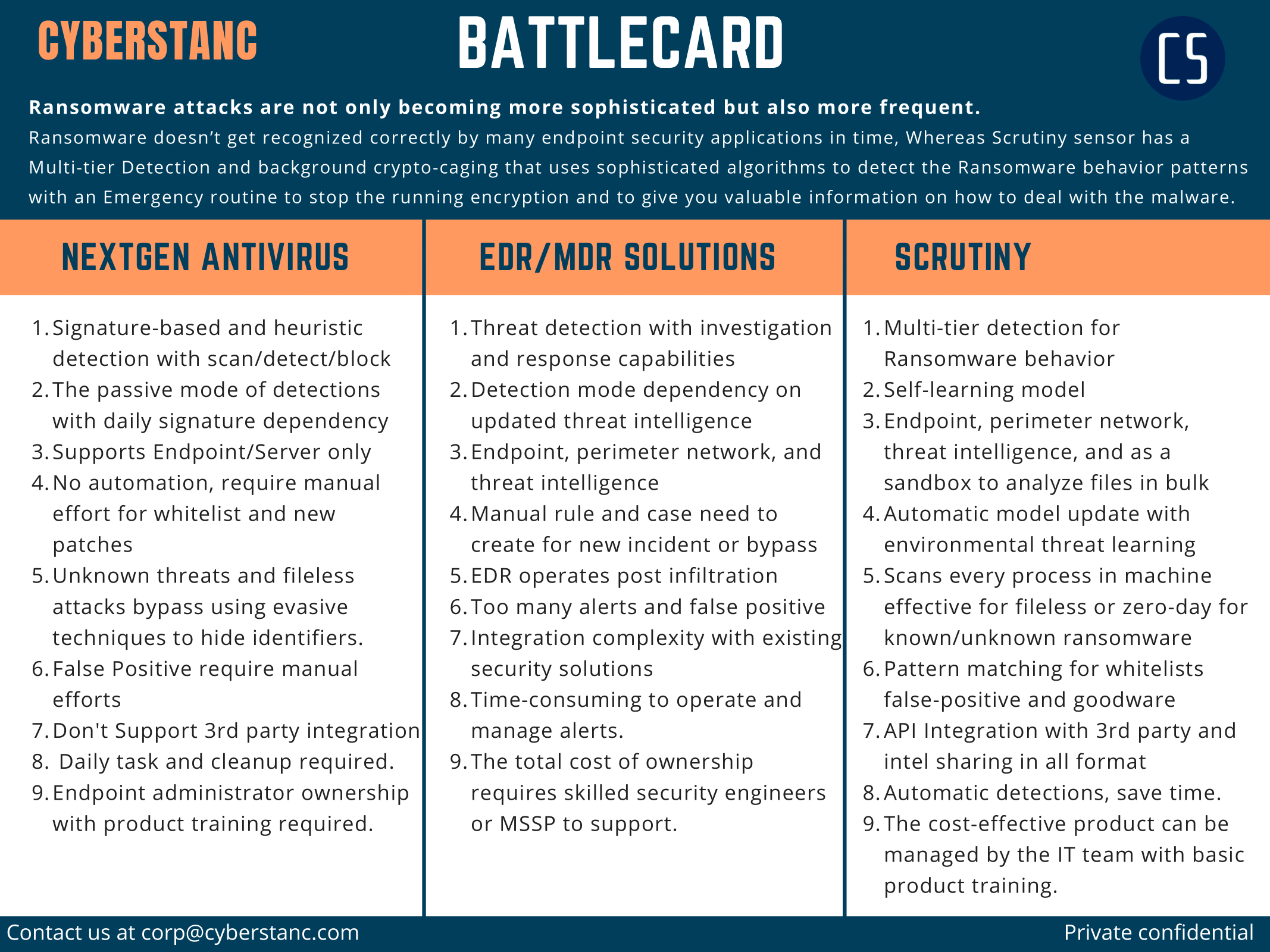
Proactively safeguarding your organization with Scrutiny
Scrutiny is designed to fill the gaps in protection left by traditional security solutions. By utilizing cutting-edge self-learning algorithms, Scrutiny can provide continuous, real-time detection and mitigation of known and advanced persistent threats, ensuring your organization's security posture stays ahead of the ever-evolving threat landscape. Its unique feature set and architecture is able to detect and block even the most advanced threats, including those that target EDR/MDR solutions.
Additionally, Scrutiny offers features such as proactive threat hunting, incident response and forensic capability to allow organization to get full picture of the attack and take necessary actions. This way, organizations can have peace of mind that their assets are well-protected and their security operations team can focus on taking action rather than searching for the needle in the haystack.
- Self Learning
- EDR/XDR/MDR Augmentation
- Hybid Deployment
- Lightweight Solution

01
Layered detection
Our approach uses multiple layers of detection and response to provide comprehensive protection against known and unknown malware. By constantly learning from new threats and updating its defense mechanisms, this approach can adapt and evolve to protect against the latest malware attacks.

02
Integrated threat intelligence
Scrutiny is designed to easily integrate with existing threat intelligence solutions, making it an effective addition to an organization's security strategy. The platform can consume and leverage a variety of threat intelligence feeds, allowing it to continuously learn about new and emerging threats providing proactive defense against known and emerging cyber threats, and support incident response efforts by providing detailed context and the necessary information.

03
Cost-effective and lightweight protection
Scrutiny is a cost-effective and lightweight solution for advanced malware detection and response. Its unique architecture and feature set is designed to provide comprehensive protection against cyber threats while requiring minimal resources.
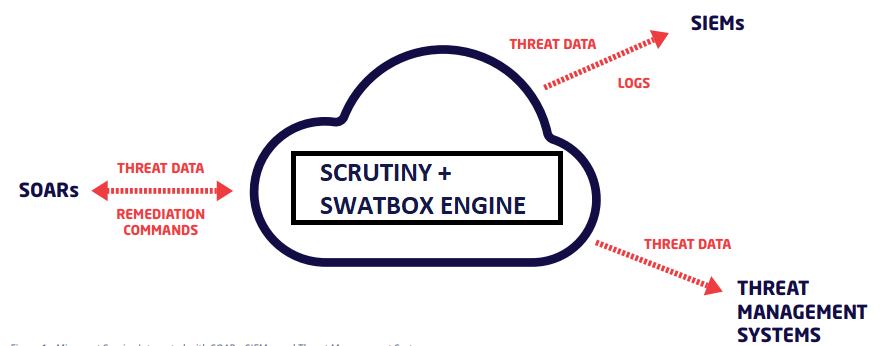
Unlock the full power of Scrutiny with its advanced scanner API
Scrutiny's scanner API is a powerful tool that enables organizations to integrate the platform's advanced threat detection and response capabilities into their existing systems. The API allows organizations to scan files, URLs, and other artifacts for malware and other malicious content in a seamless and automated manner.
Additionally, the API provides the ability to retrieve the scanning results, allowing organizations to take appropriate actions based on the outcome of the scan. The API is designed to be flexible and easily integrated into various environments, including SIEMs, incident response platforms, and other security tools. With Scrutiny's scanner API, organizations can enhance their existing security systems and gain an additional layer of protection against cyber threats.
Trusted by leading platforms.
Easily integrate Scrutiny's advanced threat detection into your existing systems with its API, trusted by leading platforms

Opswat Metadefender Enterprise
Scrutiny being integrated in Opswat’s MetaDefender platform allows organizations to leverage the advanced threat detection capabilities of Scrutiny in conjunction with the powerful data sanitization and threat intelligence capabilities of MetaDefender. This integration enables organizations to have a multi-layered defense against cyber threats, including malware and advanced persistent threats, at various stages of the security infrastructure.
Polyswarm Network
By leveraging the power of blockchain technology, Polyswarm network provides a marketplace for experts and security companies to share their knowledge and expertise in identifying and mitigating cyber threats. The integration of Scrutiny into this network can provide organizations with access to a wider range of threat intelligence, and more advanced threat detection capabilities,