Traditional sandboxes just waste time
Existing sandboxes are often slow and ineffective, failing to provide adequate protection against advanced threats. They consume significant amounts of time and resources, which can cause delays in identifying and mitigating security risks. Additionally, as attackers continue to develop new and sophisticated techniques, traditional sandboxes struggle to keep up with the evolving threat landscape. As a result, businesses need to look for more advanced and efficient solutions to protect against modern cyber threats.
In today’s evolving threat landscape, traditional sandboxes fall short in detecting advanced threats, wasting time, and resources:
- Slow and Inefficient: – Traditional sandboxes can take hours or even days to analyze a single file, causing significant delays in identifying and responding to security threats.
- Limited Visibility: – Traditional sandboxes only analyze files in isolation, which limits their ability to detect complex attacks that involve multiple files or network traffic.
- Easily Bypassed: – Attackers can easily bypass traditional sandboxes by using techniques such as code obfuscation, anti-virtualization, and sandbox detection, rendering them ineffective.
- Costly: – Traditional sandboxes can be expensive to implement and maintain, requiring significant investments in hardware, software, and personnel
- False Positives: – Traditional sandboxes can generate false positives, leading to unnecessary alerts and wasted time investigating benign files.
- Lack of Context: – Traditional sandboxes lack the context of the organization's unique environment, making it challenging to determine the relevance and severity of the analyzed files.

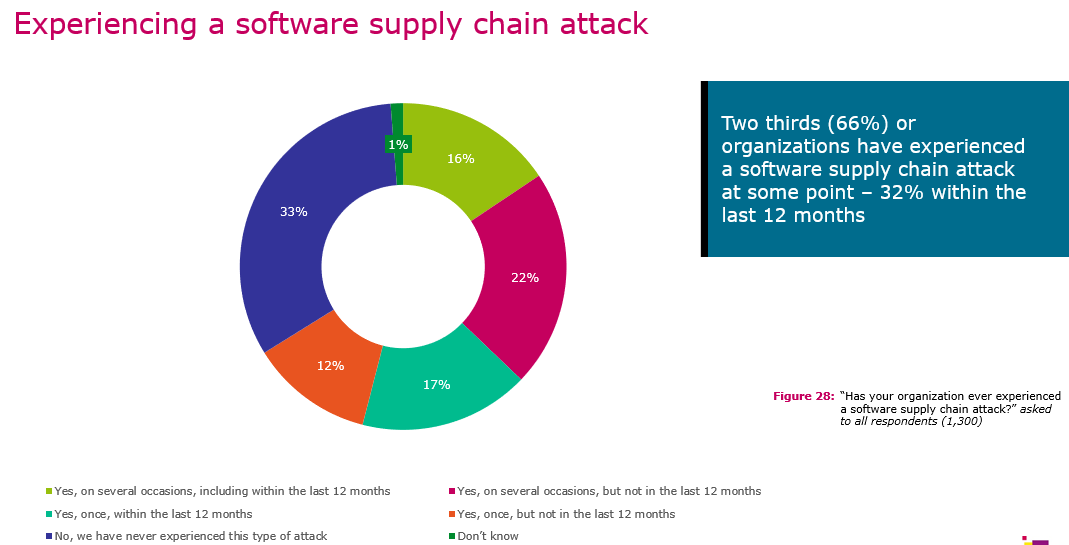
Supply chain compromise is on the rise
With the rise of cyber attacks and supply-chain attacks, businesses are increasingly investing in advanced protection to safeguard against malware and other advanced threats. . Thus, investing in advanced protection solutions is critical for businesses to enhance their overall protection capabilities.
Traditional cybersecurity solutions often fail to detect supply chain attacks because they focus on protecting the perimeter of the network and endpoints from external threats. However, supply chain attacks are initiated by compromising trusted vendors, suppliers, or partners, which allows attackers to bypass traditional security measures. These types of attacks are often difficult to detect as they occur within trusted networks, making it challenging for traditional solutions to identify and prevent them. Additionally, supply chain attacks can remain undetected for extended periods, allowing attackers to move laterally within a network and exfiltrate sensitive data unnoticed.
Supply chain compromise is on the rise
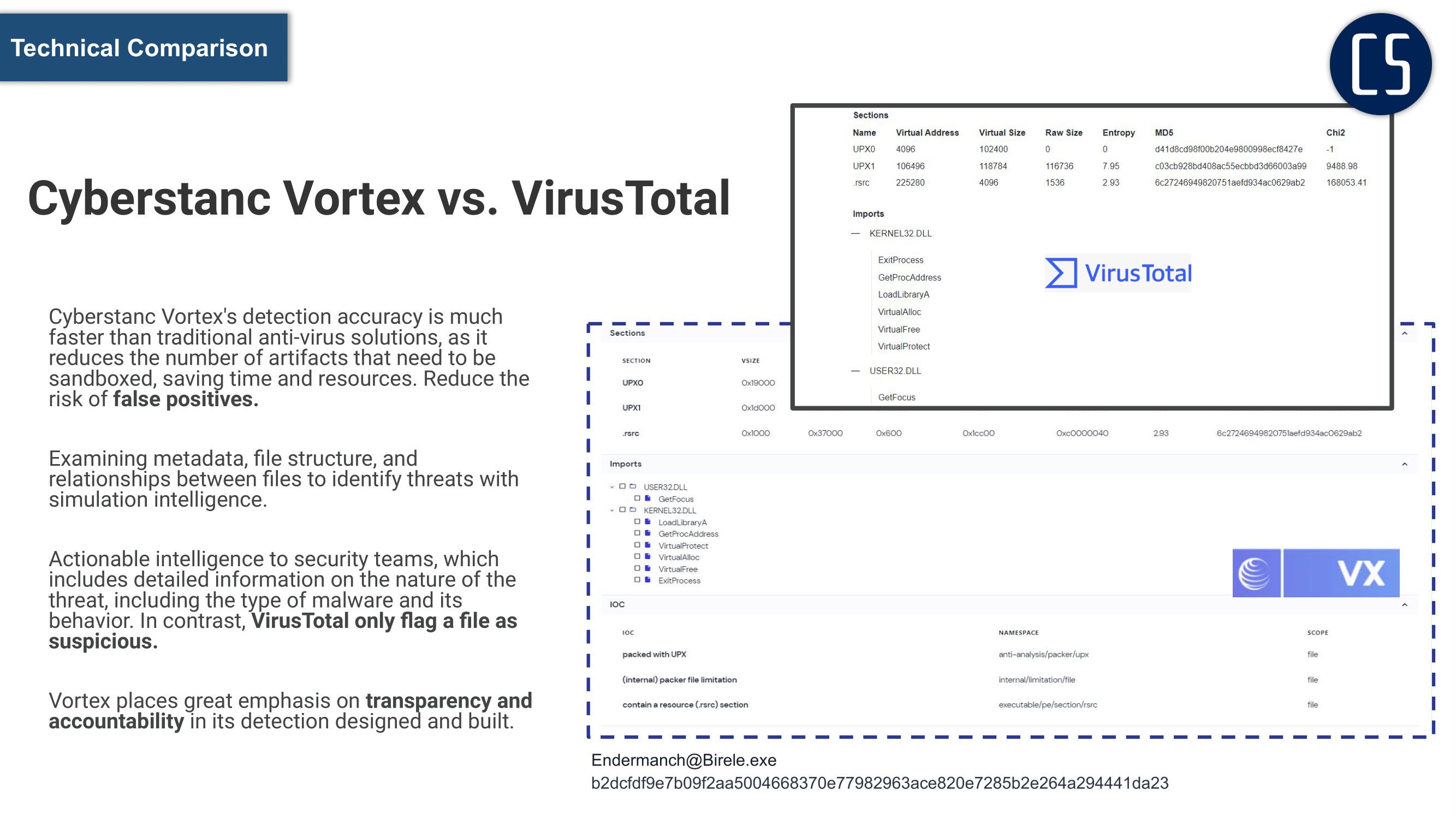
Simulate malware detection with cross validation
Traditional malware detection solutions often rely on static signatures or behavioral analysis to identify malicious files. However, with the increasing sophistication of cyber threats, these methods have proven to be inadequate in detecting advanced malware.
In-depth cross-simulation, on the other hand, is a new approach to malware detection that involves the repeated simulation of malware samples in a controlled environment. By simulating the behavior of malware in different scenarios, this method can identify patterns and characteristics that are unique to malicious code, making it possible to detect even the most advanced threats.
Unlike traditional solutions, which rely on pre-defined signatures or known behaviors, in-depth cross-simulation can identify new and unknown malware. Moreover, by simulating malware in different scenarios, such as in a virtualized environment or on different operating systems, this method can provide a more comprehensive understanding of the behavior and capabilities of malware.
Overall, in-depth cross-simulation represents a significant advancement in malware detection, providing a more effective and efficient way to identify and mitigate cyber threats.
- Increased Detection Accuracy: In-depth cross-simulation can identify new and unknown malware that traditional methods may miss, resulting in a higher detection accuracy.
- Reduced False Positives: By simulating malware in various scenarios, in-depth cross-simulation can provide a more comprehensive understanding of malware behavior, reducing false positives.
- Enhanced Threat Intelligence: In-depth cross-simulation can provide valuable insights into the behavior and capabilities of malware, which can inform threat intelligence and provide a more proactive defense against future threats.
- Future-Proofing: In-depth cross-simulation is a proactive approach to malware detection that can identify threats before they become widespread, future-proofing organizations against emerging threats.
- Improved Incident Response: By providing a more accurate and comprehensive understanding of malware, in-depth cross-simulation can improve incident response times and reduce the impact of cyber attacks.
Introducing Vortex
All in one platform with file simulation, AI-powered threat prevention and file sanitization
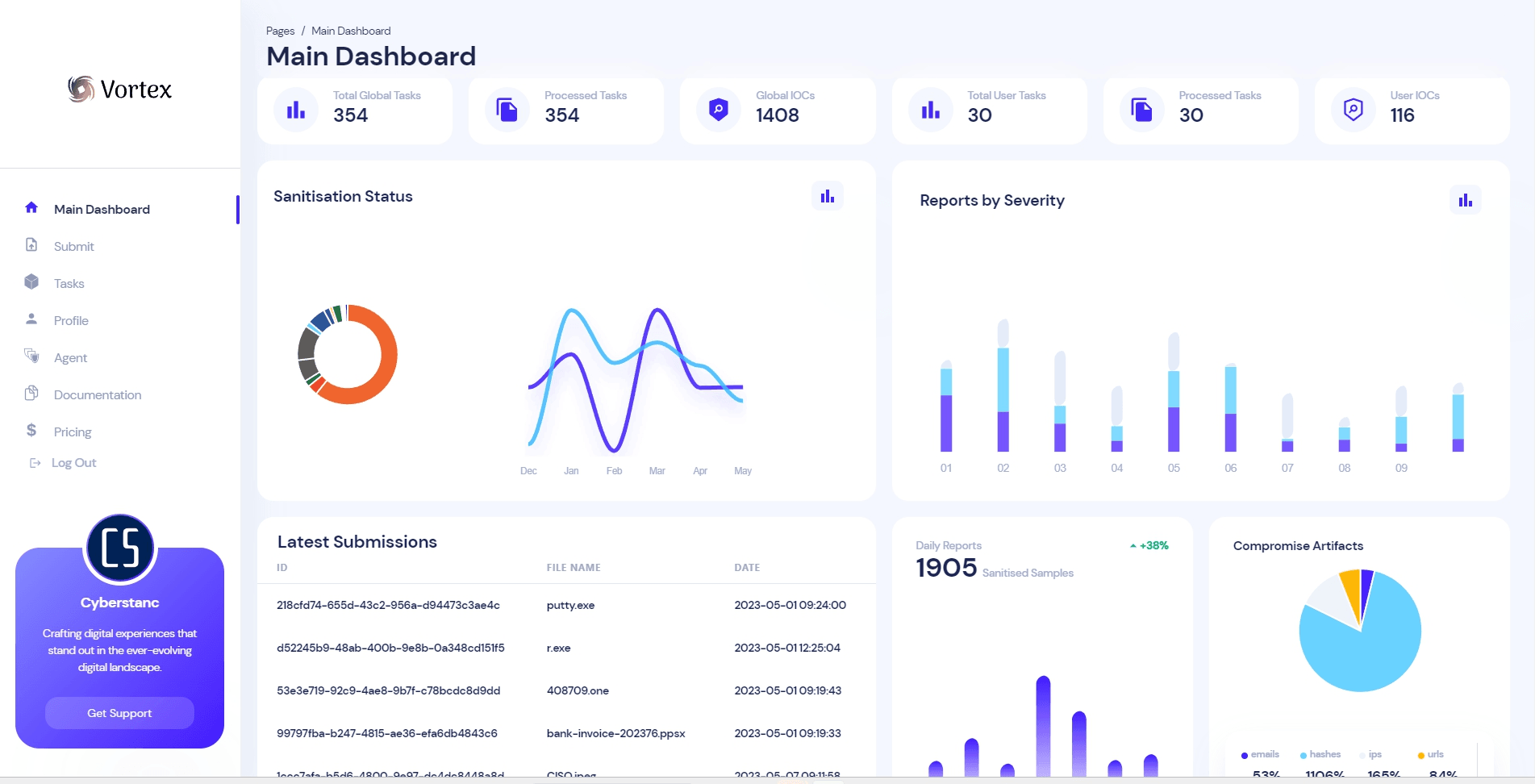
Break through the limitations of traditional security with Vortex
Cyberstanc Vortex is designed to enhance the existing frameworks, tools, and techniques for secure data transfer between secure networks. By utilizing Simulation Intelligence and Signature-less detection capabilities, it aims to bridge the gaps and overcome limitations present in current solutions. With its unique “Report, Remove, and Sanitize” feature, Cyberstanc Vortex provides comprehensive protection and ensures the secure transfer of data.
State of the art detection
The Cyberstanc Vortex platform offers a technical demo showcasing its easy API integration and agent-based use cases for endpoint, network, email, and storage protection. Its state-of-the-art threat detection system covers most of the grey areas that attackers target or plan to exploit in the future.
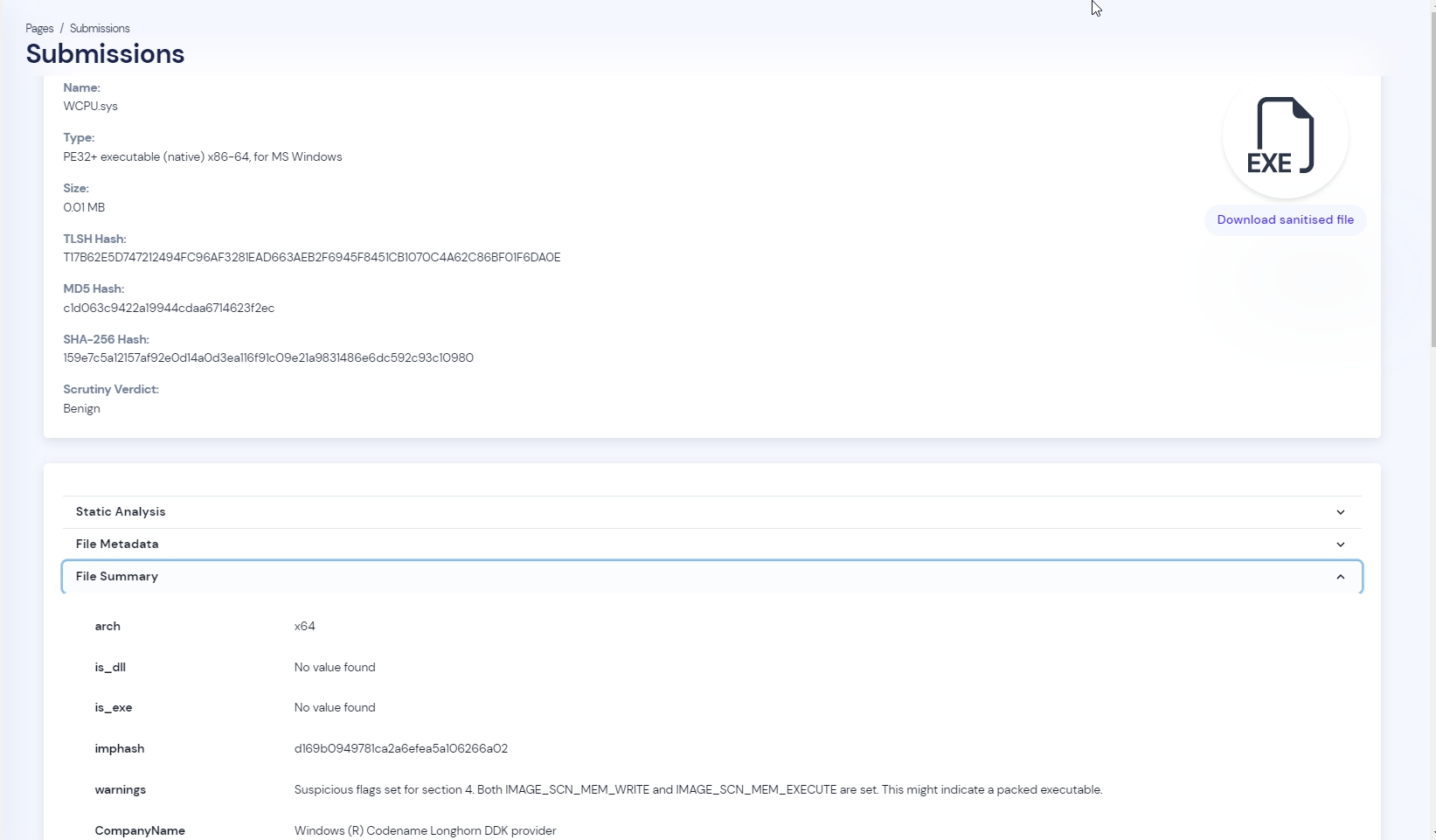
Scrutiny engine
Cyberstanc Vortex integrates Scruitiny's engine and custom co-build agent to detect a wide variety of files, such as executables, documents, scripts, and common file-types. This comprehensive approach ensures thorough protection for all your data.
Simulation Intelligence
Simulation Intelligence of highly obfuscated and real-word malware techniques including macro malware, VBA, VBS, PowerShell, DOCx, Calender files, One-Note, Jscript, MSHTA, XSL, and WSF.etc andc counting
File types
Vortex, supports a wide range of file types to ensure comprehensive protection for all your data. This includes popular file types such as Microsoft Office documents, PDFs, image files, audio and video files, almost 150+ file types.
Cost effective
Vortex provides both rapid and thorough file analysis at scale, and offers a REST API for easy integration. It can be deployed on-premises or in the cloud, making it a flexible and cost-effective solution for organizations of all sizes.
Use Cases
Unleash the full potential of your data with Vortex the ultimate solution for secure and streamlined file sharing, collaboration, and storage

Simulated intelligence
SWATBOX uses simulated intelligence to detect and respond to emerging threats in real-time, by emulating a wide range of realistic attack scenarios.

Malware Sandboxing
Utilizes a combination of dynamic analysis, behavioral analysis, and machine learning to detect and analyze malware samples in a controlled environment.

Threat hunting
Allows organizations to identify unknown or undiscovered threats and understand the attack chain providing curated intelligence for proactive defense and incident response.

Integration
Integrates with other security solutions such as EDR and SIEM, providing a comprehensive view of the security posture and visibility into the attack chain.

Complliance
Designed to be cost-effective and lightweight, it does not significantly impact system performance, and fully compliant with standard regulations capable of supporting 100k+ file scans per day, making it an ideal solution for organizations with large-scale security operations.

SOC Empowerment
Vortex can help SOC teams and analysts with day-to-day hunting by providing a comprehensive platform for storing and sharing files, advanced threat detection, centralized visibility, collaboration and workflow management, and integration with other security tools.