Swatbox










Don't get caught off guard by emerging threats
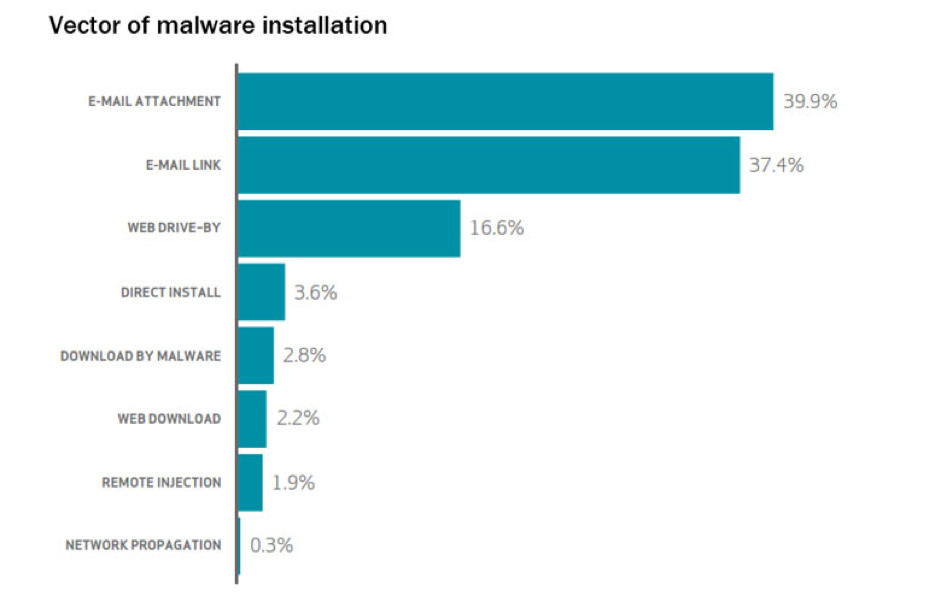
Traditional malware sandboxing and simulation solutions may fall short of detecting emerging threats because they often rely on static analysis and pre-defined rules to detect malware.
This can make it difficult for these solutions to detect new and unknown threats, as they are not able to adapt to the constantly evolving threat landscape. Emerging threats, such as evasive malware and fileless attacks, can bypass these static analysis methods and evade detection.
"EDR bypasses? Just another game for attackers"
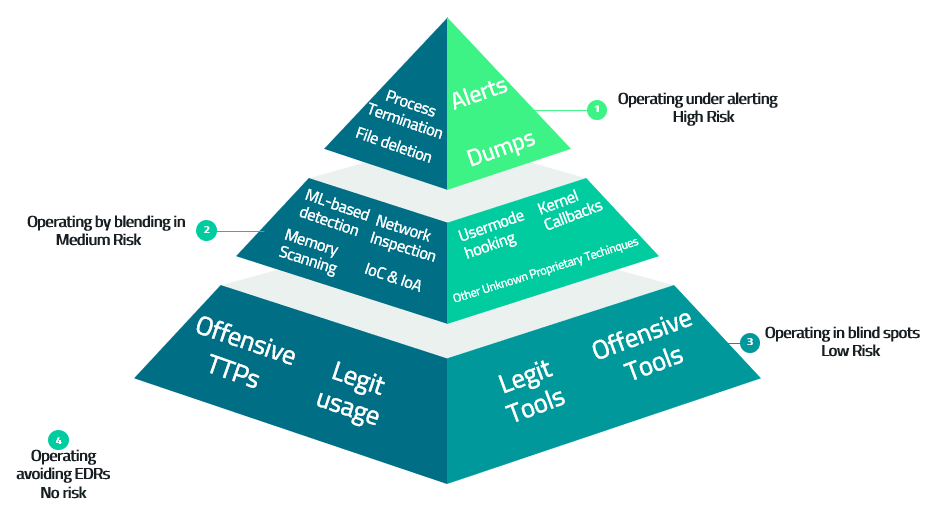
Bypasses have become a common tactic used by attackers to evade detection and gain access to sensitive information. These types of attacks are designed to exploit the limitations of traditional security solutions making it easy for attackers to bypass these solutions and gain access to an organization’s network undetected and stay persistent.
Some common techniques include :
- Use of scripting languages – Security solutions typically rely on system calls and other low-level activity to detect malicious activity. Some attackers will use scripting languages or other higher-level tools to perform malicious activities, which may not generate the same system calls that an EDR solution is looking for, allowing them to evade detection.
- Legitimate tools – Use of legitimate tools: Attackers often use legitimate tools, such as PowerShell, to perform malicious activities, which can evade detection by EDR solutions that are not configured to detect malicious use of these tools.
- Event Manipulation – Manipulation of security events: Some attackers may try to manipulate the data that an EDR solution receives, by altering system logs or other data sources, in order to evade detection.
- Vulnerable Drivers (BYOD) – Vulnerable device drivers can be exploited by attackers to gain access to the kernel level of a system , by exploiting vulnerabilities in device drivers, attackers can run malicious code with kernel level privileges, giving them complete control over a system and potentially evading detection from EDR.
Simulate real-world threats ? Not really !
While simulation using decoy malware can be a powerful technique for assessing an organization’s security posture and identifying new and unknown threats, it is not enough by itself to protect against advanced and evasive threats. Decoy malware can only simulate a specific environment, and can’t replicate all possible scenarios. Attackers are constantly developing new techniques and ways of evading detection, and relying solely on decoy malware can lead to a false sense of security.
- Simulation using decoy malware can only simulate specific scenarios, advanced attackers can use different techniques to evade it.
- It does not guarantee that an attacker will interact with the decoy, and can provide a false sense of security.
- Organizations need to complement the decoy approach with other techniques such as EDR, XDR, MDR and threat intelligence for a comprehensive view of potential risks.
- Organizations need to have incident response and incident management processes in place in order to quickly contain and remediate an attack when it occurs.
- Decoy malware is not a standalone solution, it is just one element in a multi-layered defense strategy.
Introducing Swatbox
Elevate your security posture with SWATBOX: the ultimate malware simulation and threat hunting platform
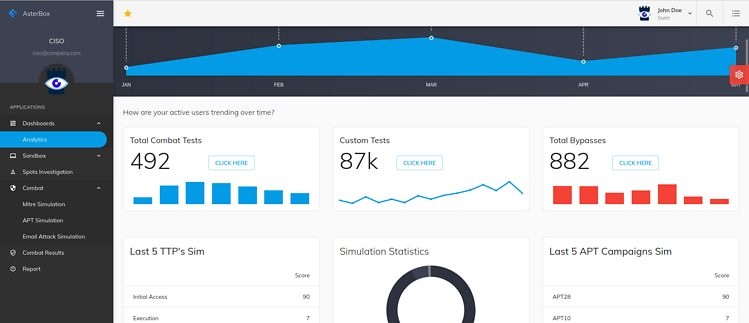
Eliminate blind spots with SWATBOX
SWATBOX is an advanced malware simulation and sandboxing platform that utilizes simulated intelligence technology to detect and respond to emerging threats in real-time. It is designed to emulate a wide range of realistic attack scenarios, allowing organizations to assess the effectiveness of their existing security solutions and identify any potential vulnerabilities.
Swatbox at a glance
SWATBOX utilizes a combination of dynamic analysis, behavioral analysis, and machine learning to detect and analyze malware samples in a controlled environment. It uses real life malware from the wild, which involves creating a sandboxed environment that simulates a real-world target and seeding it with decoy data, to lure attackers into a controlled environment where they can be monitored and their behavior studied.
The platform also integrates with other security solutions such as SOAR and SIEM, providing a comprehensive view of the security posture and visibility into the attack chain. It also integrates with threat intelligence platforms to use curated intelligence for proactive defense and incident response.
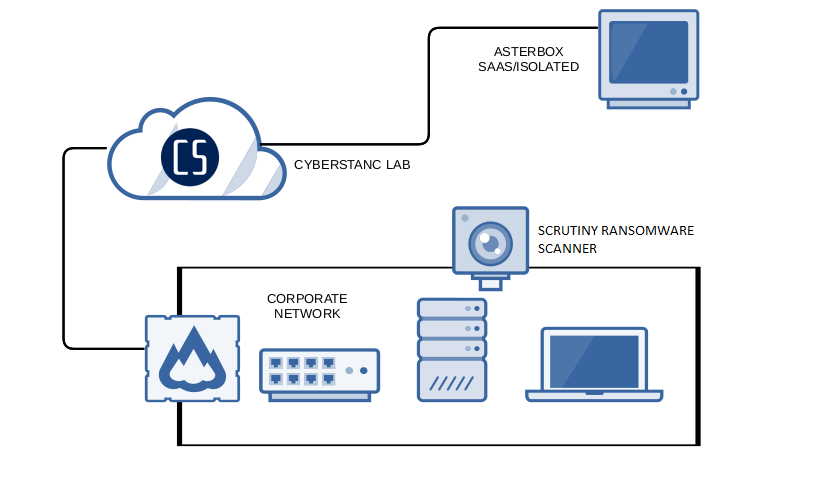
Core Features
Unlock the full potential of your security defenses with SWATBOX's advanced simulation and sandboxing capabilities

Simulation
SWATBOX uses simulated intelligence to detect and respond to emerging threats in real-time, by emulating a wide range of realistic attack scenarios.

Malware Sandboxing
Utilizes a combination of dynamic analysis, behavioral analysis, and machine learning to detect and analyze malware samples in a controlled environment.

Threat hunting
Allows organizations to identify unknown or undiscovered threats and understand the attack chain providing curated intelligence for proactive defense and incident response.

Integration
Integrates with other security solutions such as EDR and SIEM, providing a comprehensive view of the security posture and visibility into the attack chain.

Complliance
Designed to be cost-effective and lightweight, it does not significantly impact system performance, and fully compliant with standard regulations.

Shared Intelligence
A full-featured API is provided that can be easily integrated into other security platforms enabling threat intelligence sharing amongst customers and partners.