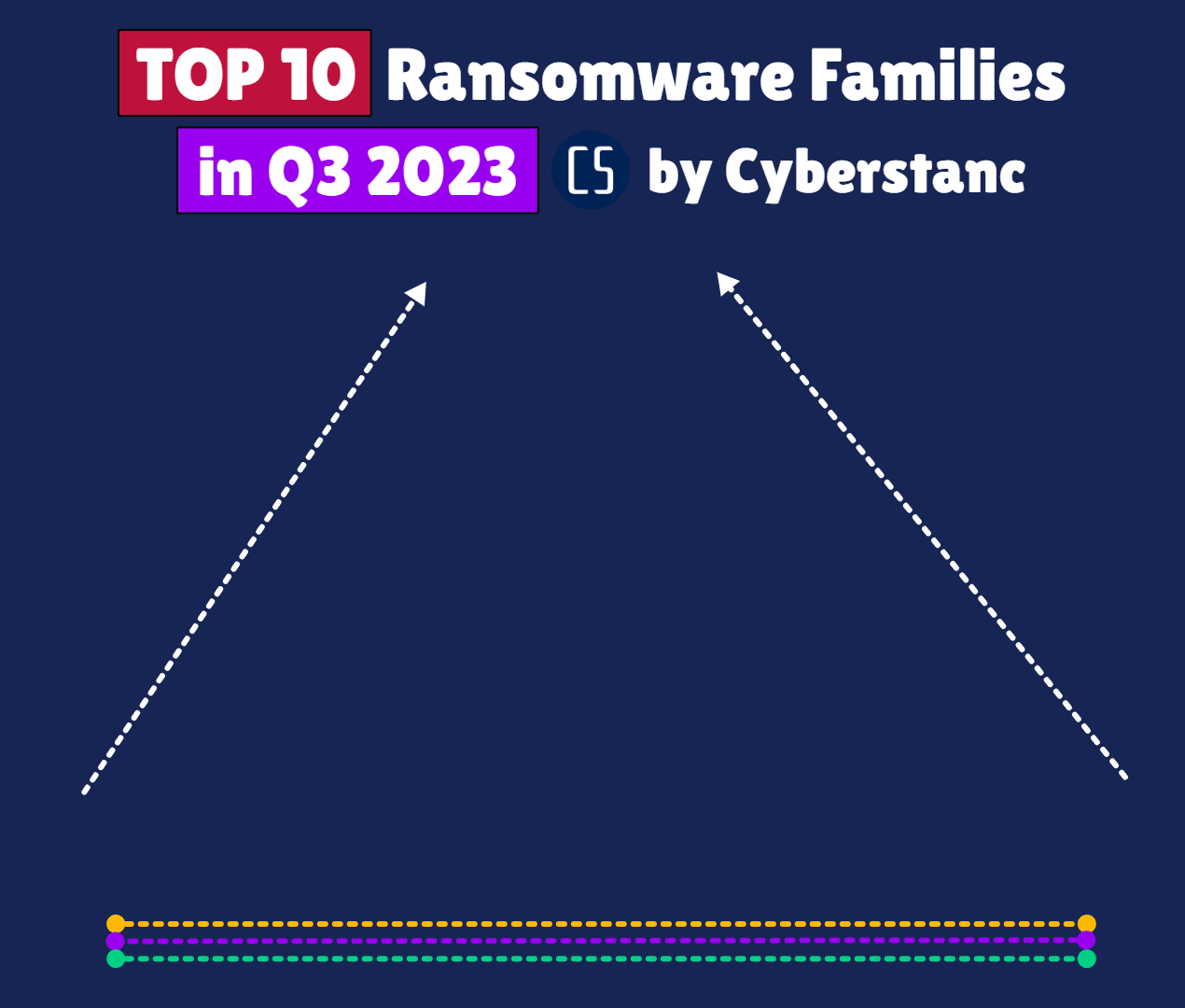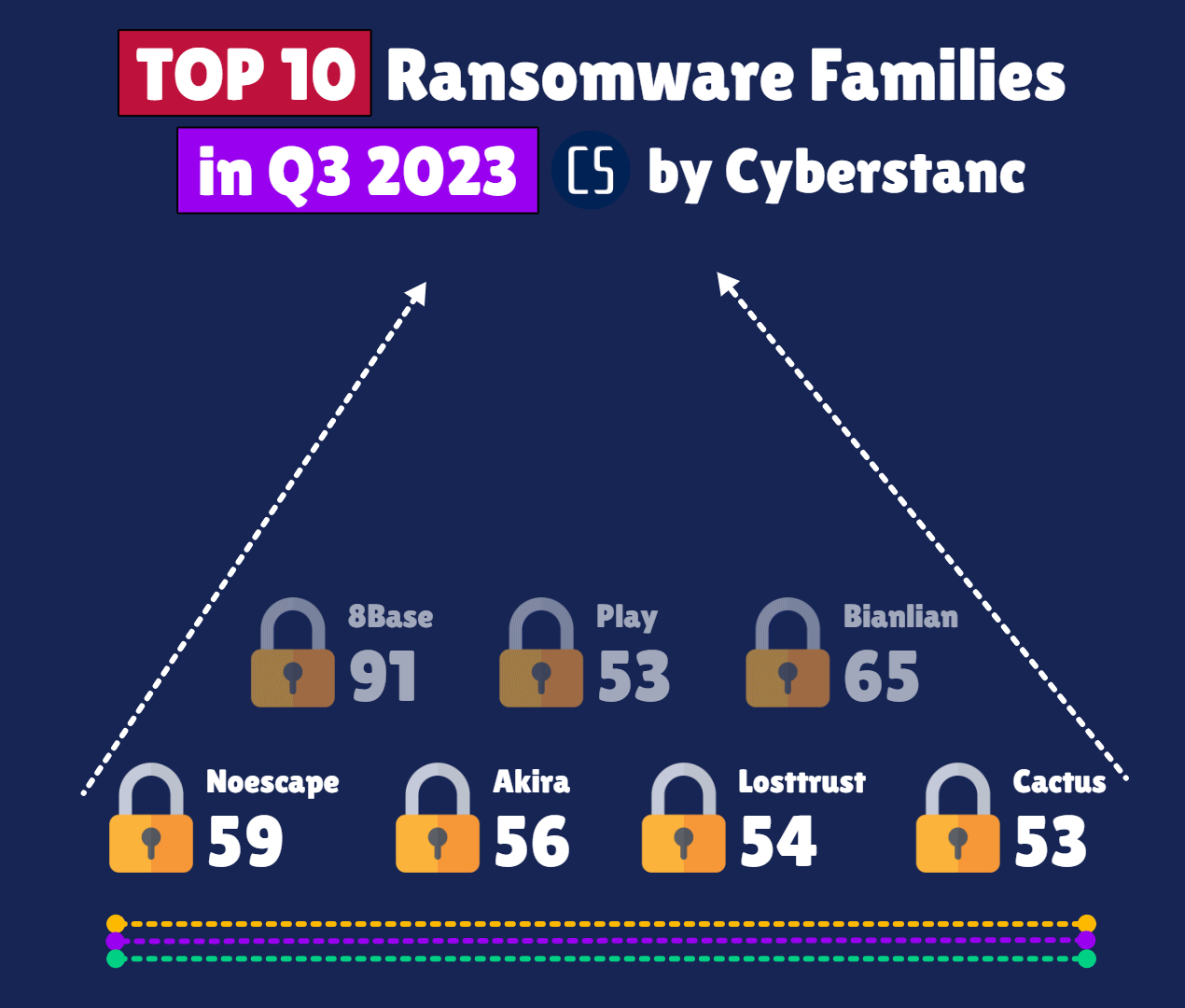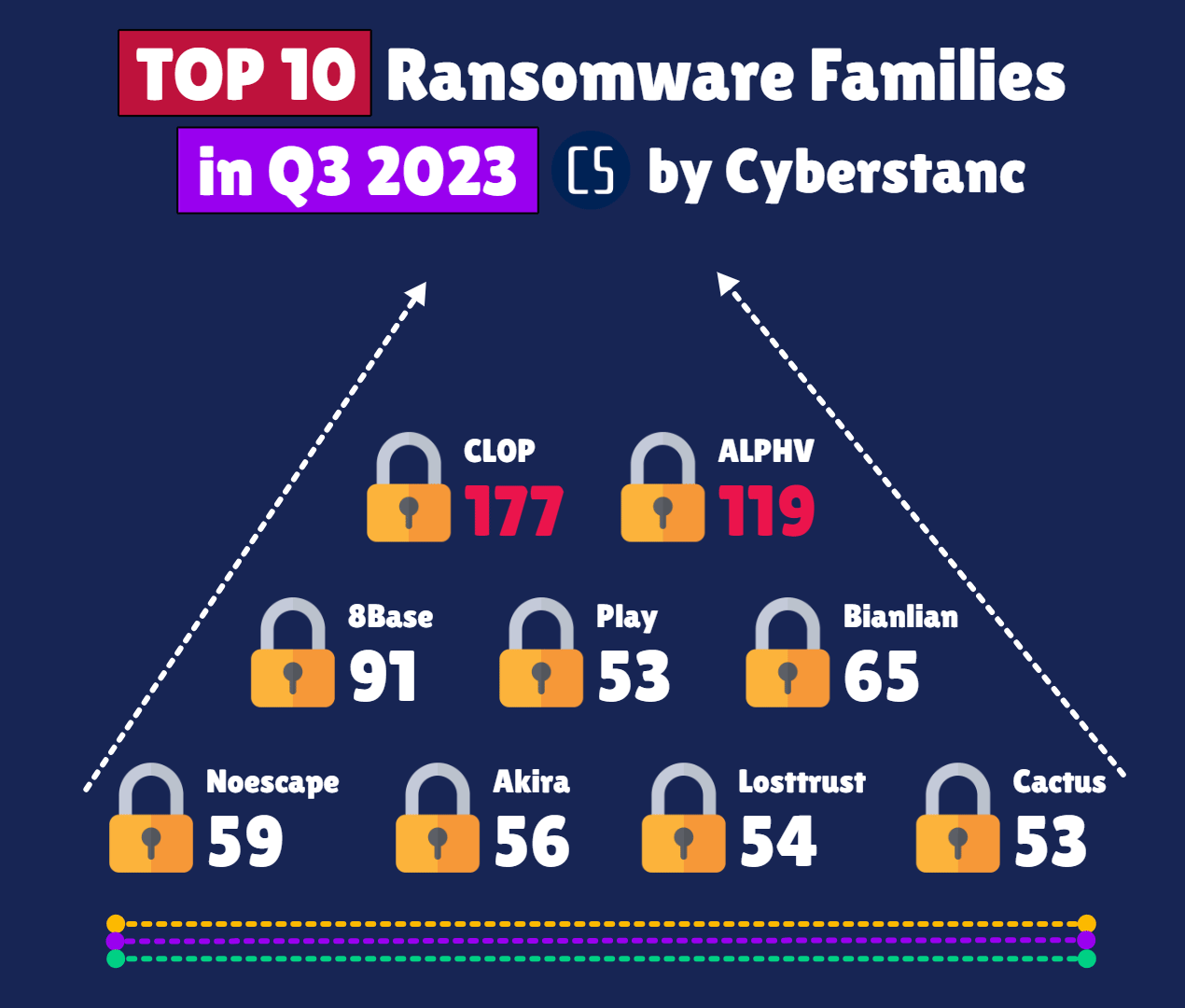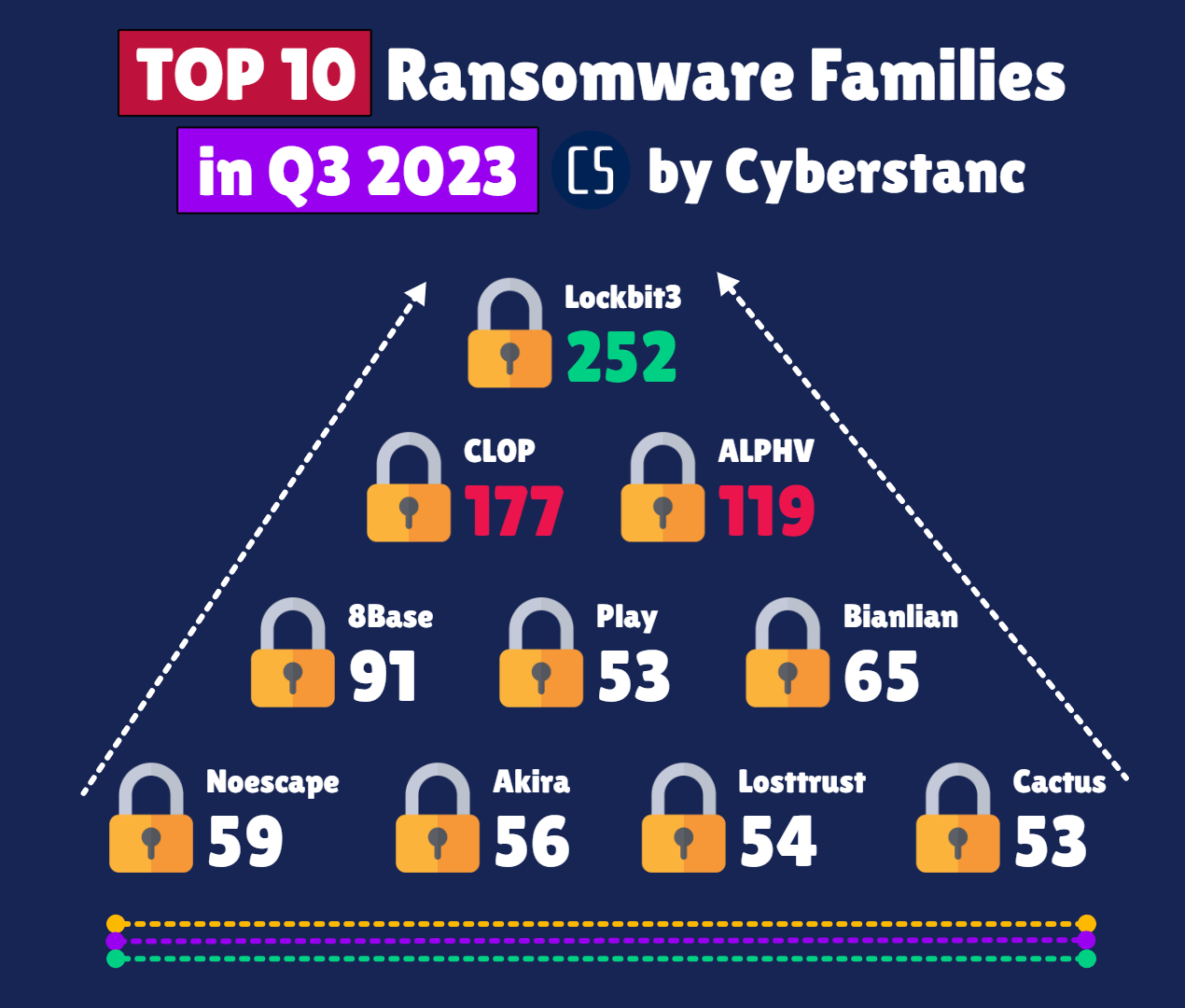
Defend, Detect, Deter: Enter RIPx for Ransomware!
Understanding the Ransomware Threat
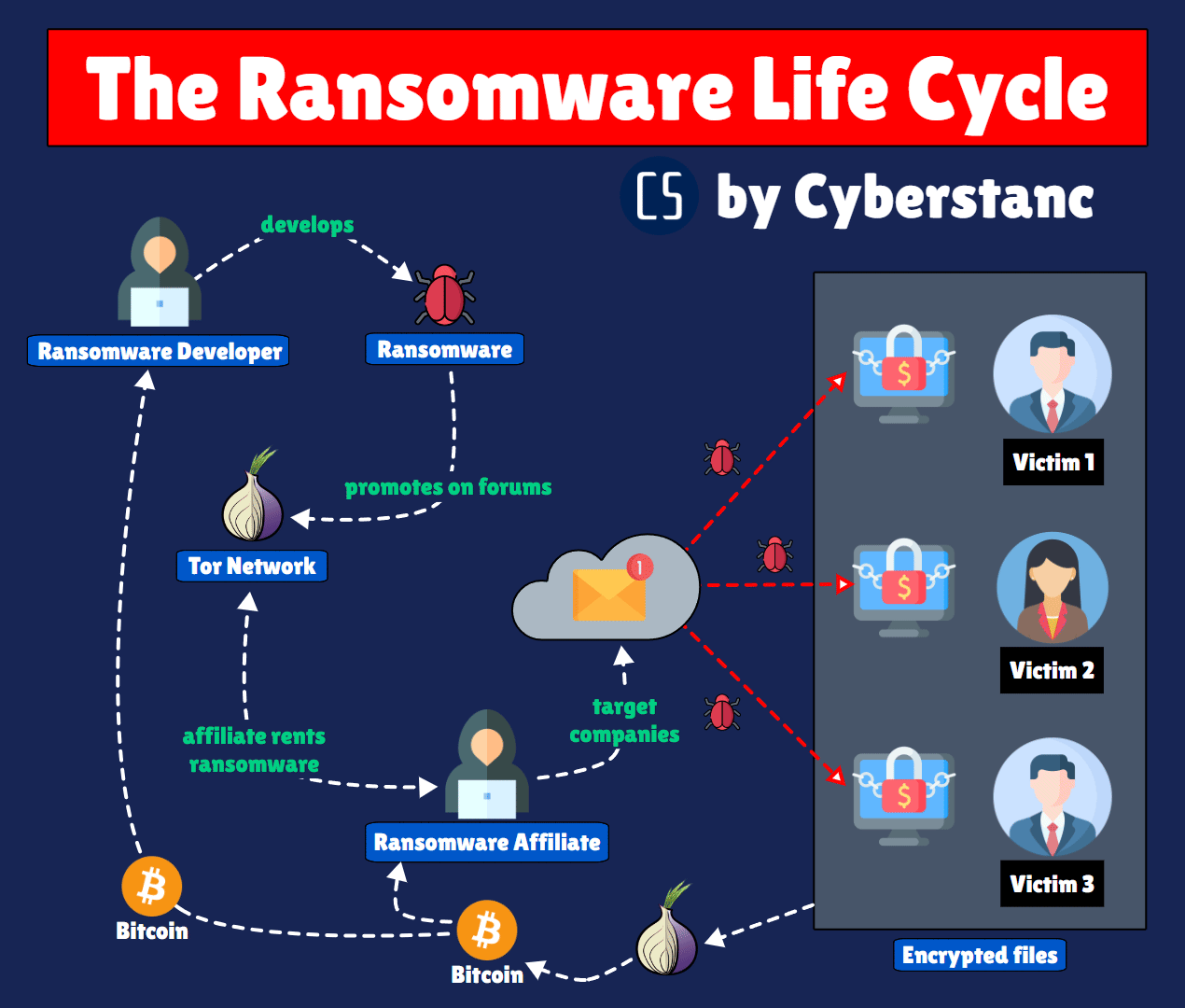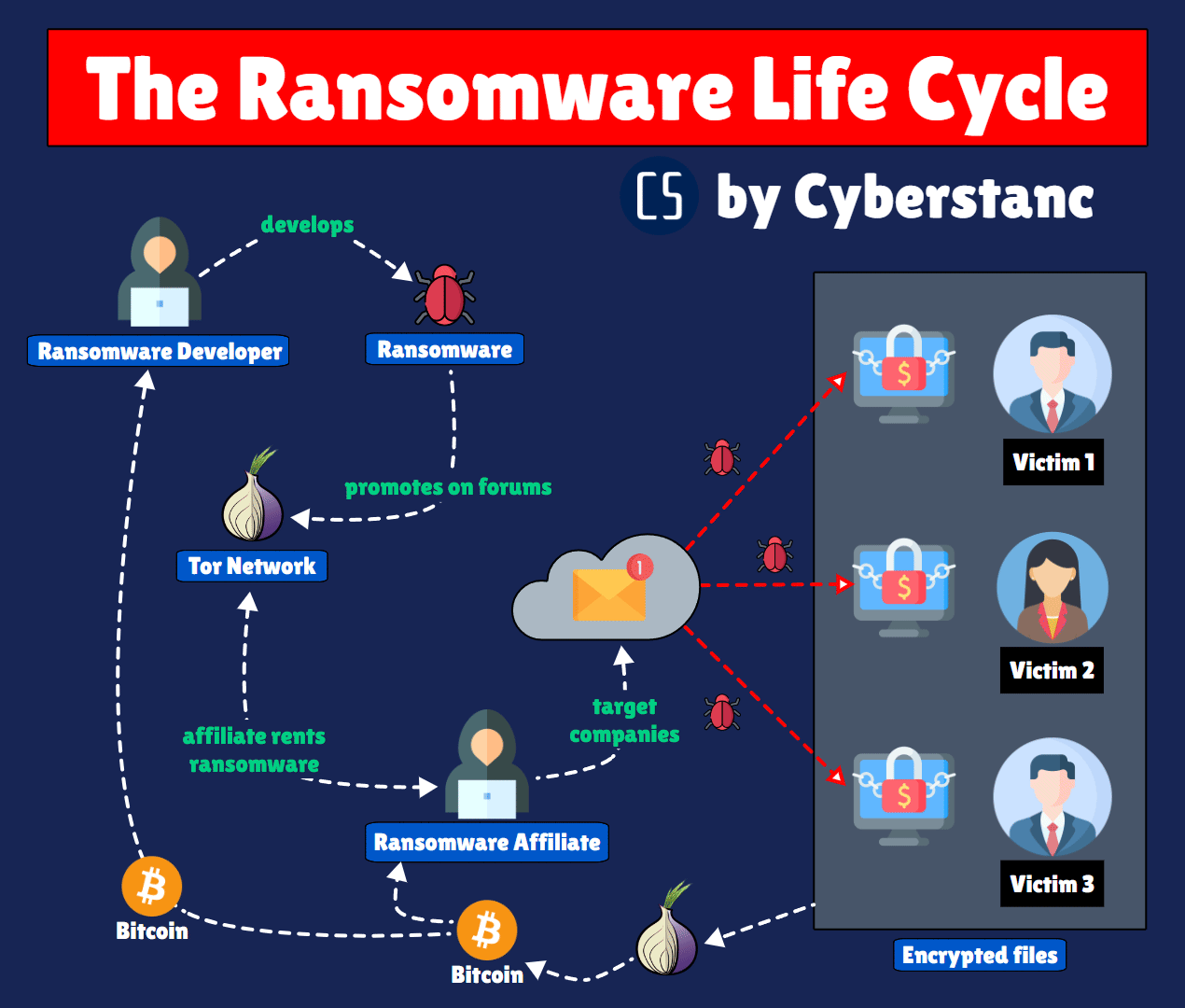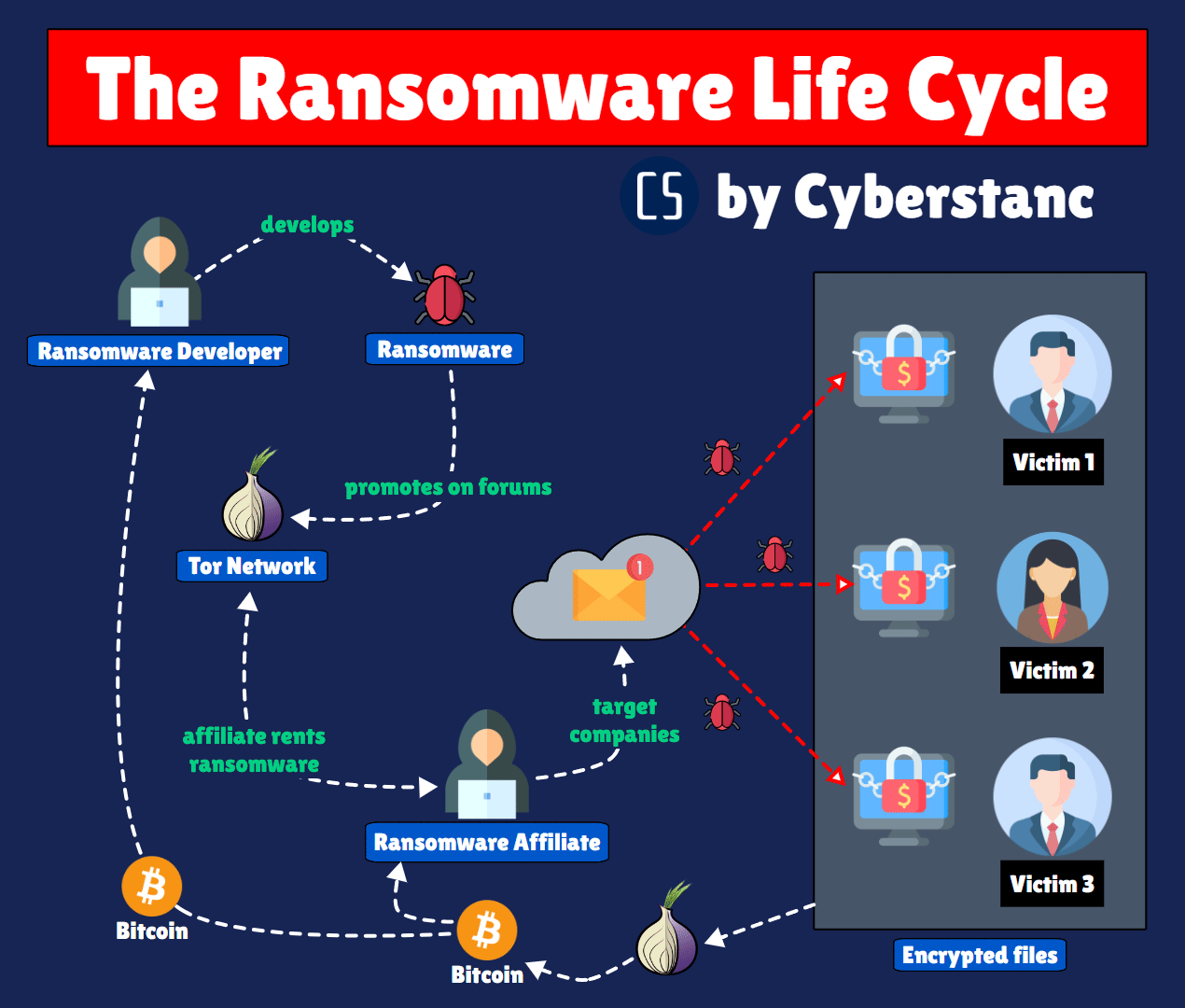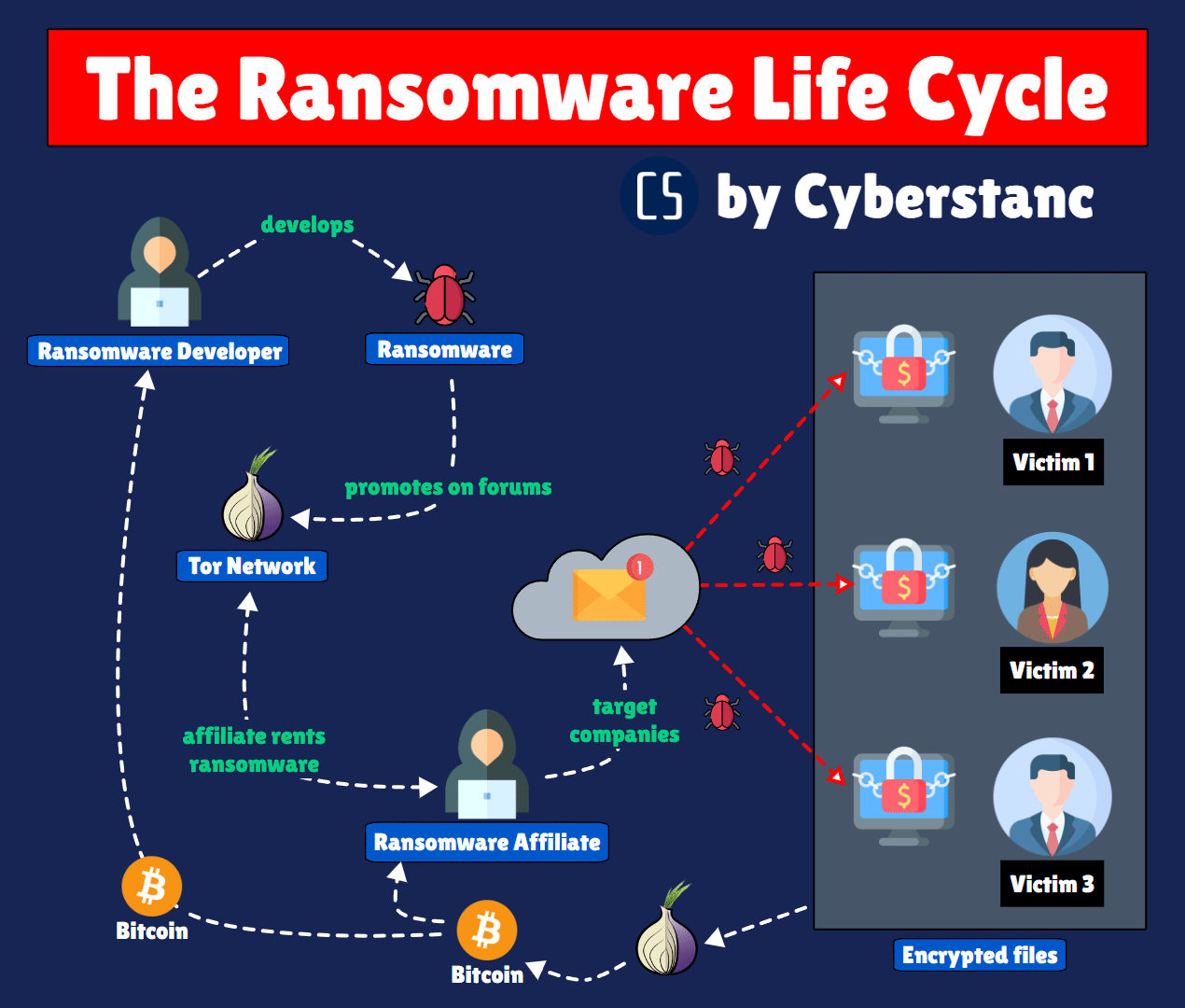
Ransomware is a type of malware that encrypts files or locks users out of their systems, demanding a ransom payment in exchange for restoring access. These attacks have targeted organizations across various sectors, from healthcare to finance, exploiting vulnerabilities in systems and networks.
The group uses double extortion – exfiltrating victim data and encrypting it, and threatening to publish the stolen data unless a ransom is paid.

As these malicious attacks continue to evolve and become more sophisticated, it's crucial to arm ourselves with effective defense mechanisms. Ransomware attacks have become a prevalent threat in the digital landscape, causing significant disruptions and financial losses to businesses and individuals alike.
The Birth of RIPx : a revolutionary approach in combating ransomware.
Not knowing the inner workings of ransomware is crucial for thwarting its objectives. This lack of knowledge inhibits replication, secures vulnerabilities, and aids in developing effective countermeasures.
RIPx, short for Ransomware Intrusion Protection Xtreme, represents a proactive strategy against ransomware attacks.
RIPx's inception marks a transformative journey bridging intelligence and detection, revolutionizing intrusion identification. It starts by harnessing global threat intelligence to meticulously profile ransomware patterns.
Our "RIPx" program strategically combats ransomware's decentralized network. Given the intricate complexities within ransomware markets, tracing attackers poses challenges. Our responder focuses on disrupting this web, impeding developers, distributors, and Initial Access Brokers (IABs).
"Focusing on prevention, we employ surveillance and threat intelligence to foresee and deter ransomware assaults."
RIPx Strategies: From Ransomware Strike to Post-Attack Resilience
RIPx Strategies shift focus from responding to ransomware strikes to bolstering pre and post-attack resilience. Armed with advanced technologies, it proactively thwarts and neutralizes threats.
The imperative moment is here—opting for the right defense mechanisms and swift actions is crucial to safeguard against and eliminate ransomware intrusions.
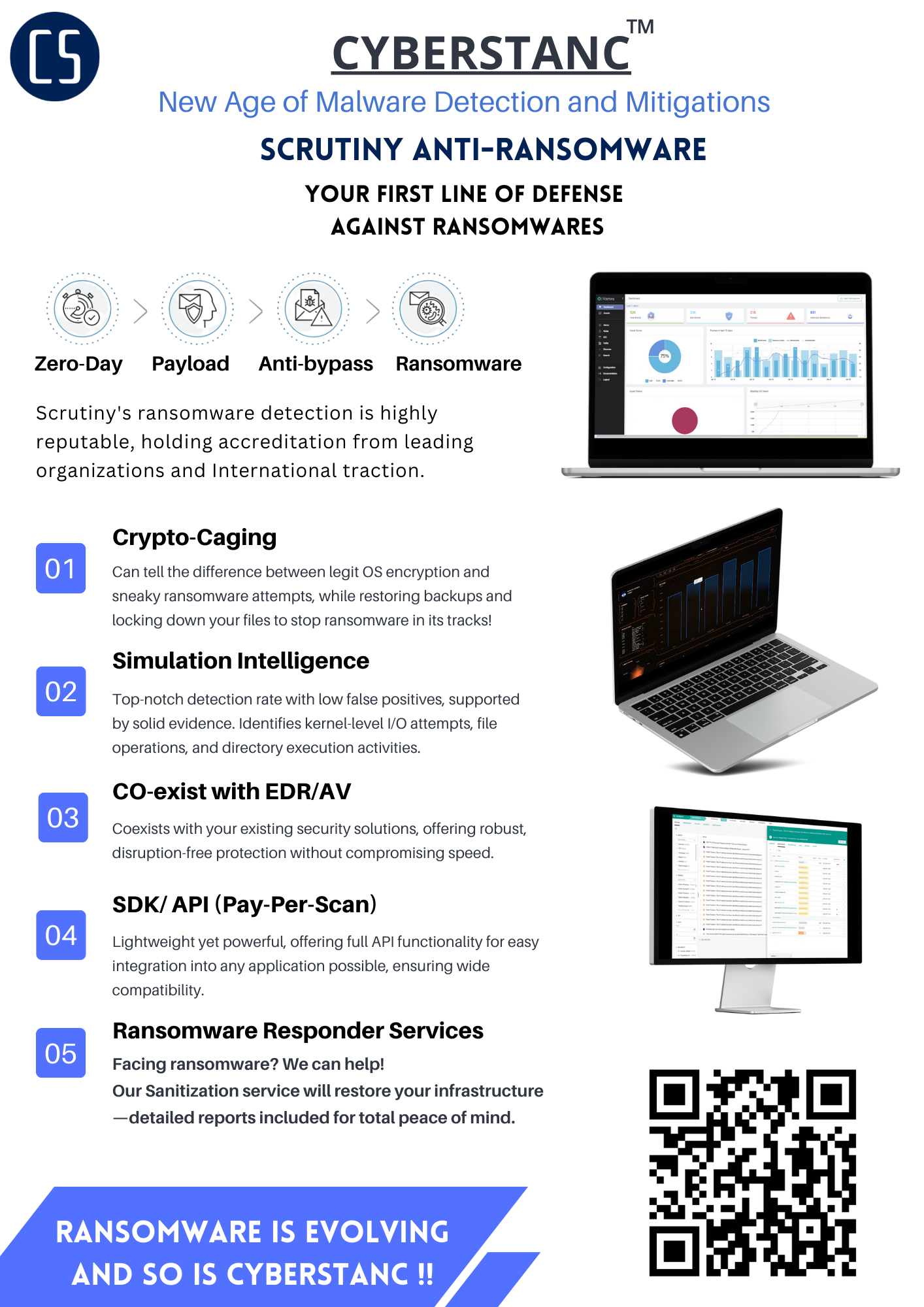
Scrutiny Anti-Ransomware Engine: RIPx employs advanced behavioral analysis engine to detect anomalies in system behavior. This proactive approach enables the system to identify potential ransomware activity before it can cause significant damage.
Ransomware Responder Service: Leveraging Simulation intelligence models, RIPx continuously learns from patterns and trends in data, enabling it to adapt and evolve in the face of evolving ransomware threats.
CRYPTO-CAGING: RIPx offers real-time monitoring of system activities and immediate response mechanisms. This proactive approach helps in isolating and neutralizing potential ransomware threats before they can spread across the network.
RIPx Ripple Effect
Over the past four years, RIPx (Ripple Effect) Cybersecurity has pioneered cyber resilience through its cutting-edge Simulation Lab.
With international partnerships in Threat Intelligence, governmental agencies, and elite professionals from the USA, Russia, China, Korea, and Turkey, RIPx focuses on advancing malware and ransomware taskforces. Our Ransomware Responder Program collaborates with researchers to test diverse modes, ensuring robust cyber defense.
"https://cyberstanc.com/ripx/"
"https://www.mach37.com/blog/2021/1/19/cyberstanc-introduces-newest-addition-ripx"
How RIPx is new game changer !!
In the non-stop battle against ransomware, a game-changer has surfaced: the Core Feature Hunting (CFH) approach. It's not a tool—it's the secret weapon we've been longing for in this relentless fight.
Addressing issues of data scarcity and class imbalance, CFH employs a novel strategy by harnessing a range of classifiers—such as Support Vector Machines (SVM), Random Forest (RF), and Logistic Regression Classifier (LRC)—trained on derived deep features.
For instance, the SVM classifier excels in establishing complex decision boundaries within the feature space, while RF, with its ensemble of decision trees, proficiently captures intricate relationships among features. Conversely, LRC, being a linear model, emphasizes the importance of individual feature weights, offering interpretability alongside detection capabilities.
For instance, this extraction method identify key behavioral patterns within ransomware attacks, such as file encryption methods or specific system interactions.
Training on Different Feature Spaces: The Ensemble Strategy
Our approach to fortifying our scrutiny engine involves a meticulous sequence of steps, orchestrating a unified and powerful defense against ransomware at every turn.
By curating a blend of classifiers chosen for their precision and recall metrics, we've constructed a ransomware-sensitive ensemble. This ensemble capitalizes on the unique strengths of each classifier, forging a collective defense mechanism that excels in detecting a wide array of ransomware variations.
Precision-Recall Driven Detection Sorting Framework
The selection of optimal base learners is a pivotal step in forming a ransomware-sensitive ensemble. CS Team employs a sorting process based on precision and recall. This meticulous evaluation ensures that the chosen classifiers demonstrate high precision and recall, crucial metrics in detecting and mitigating ransomware threats.
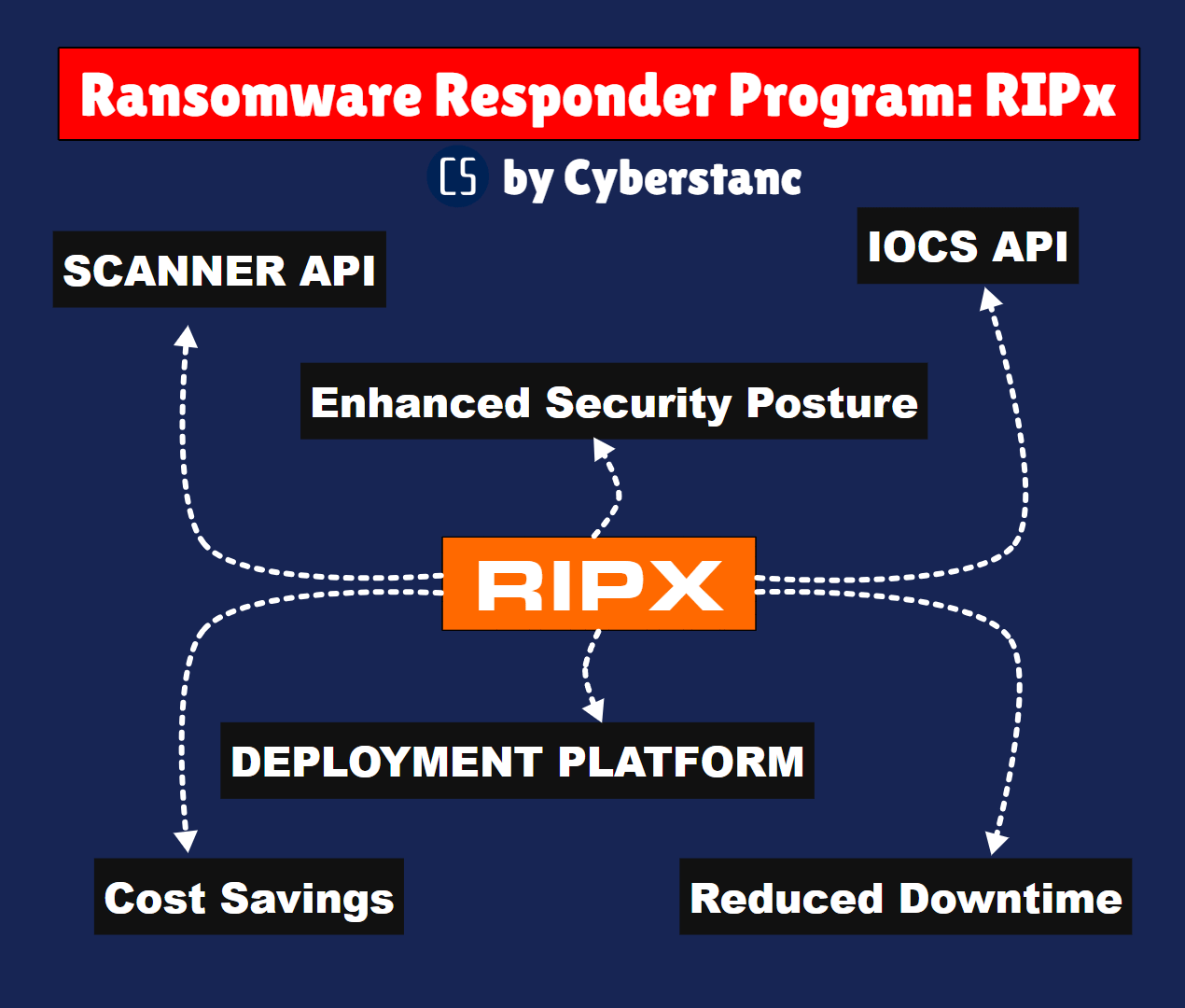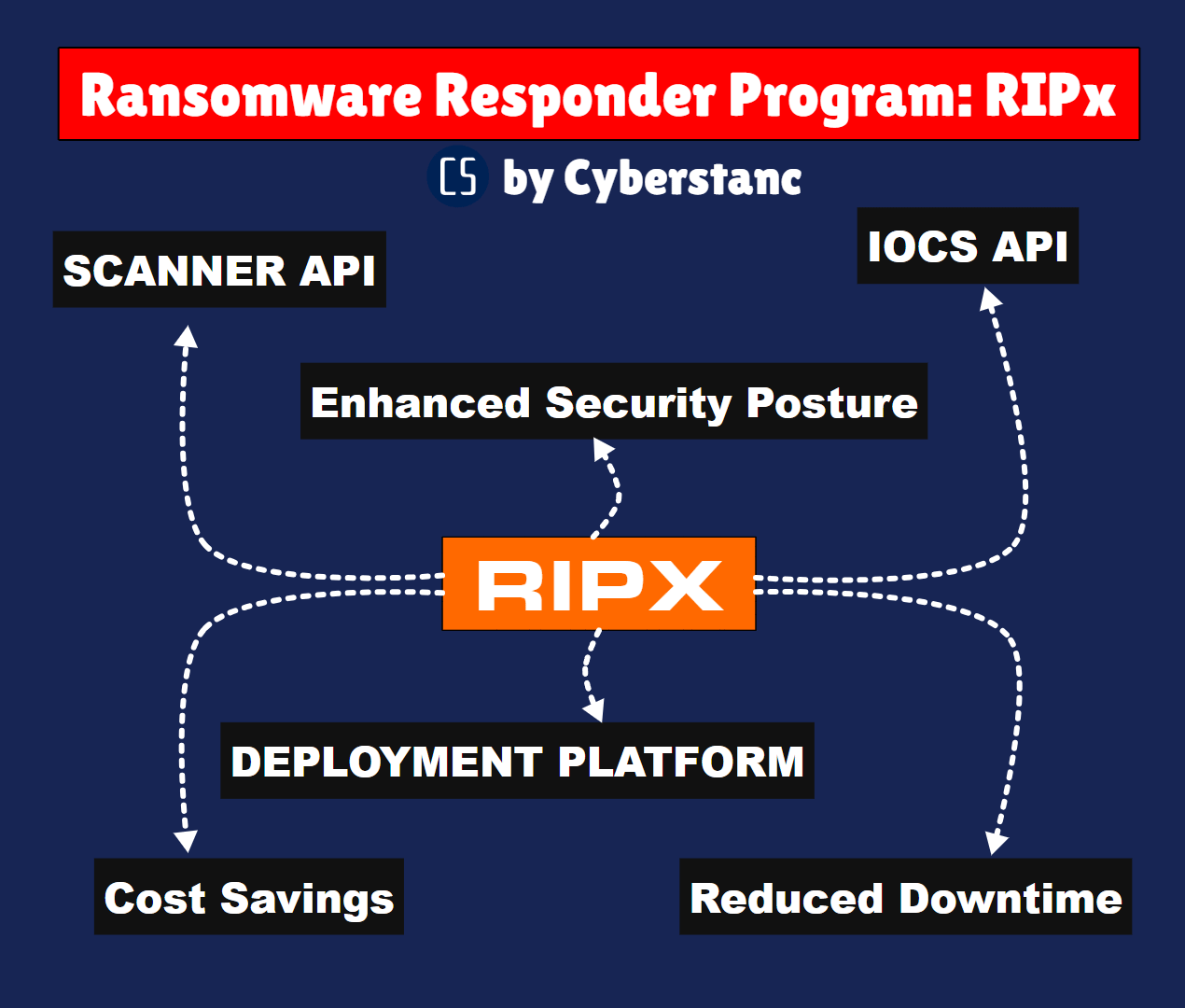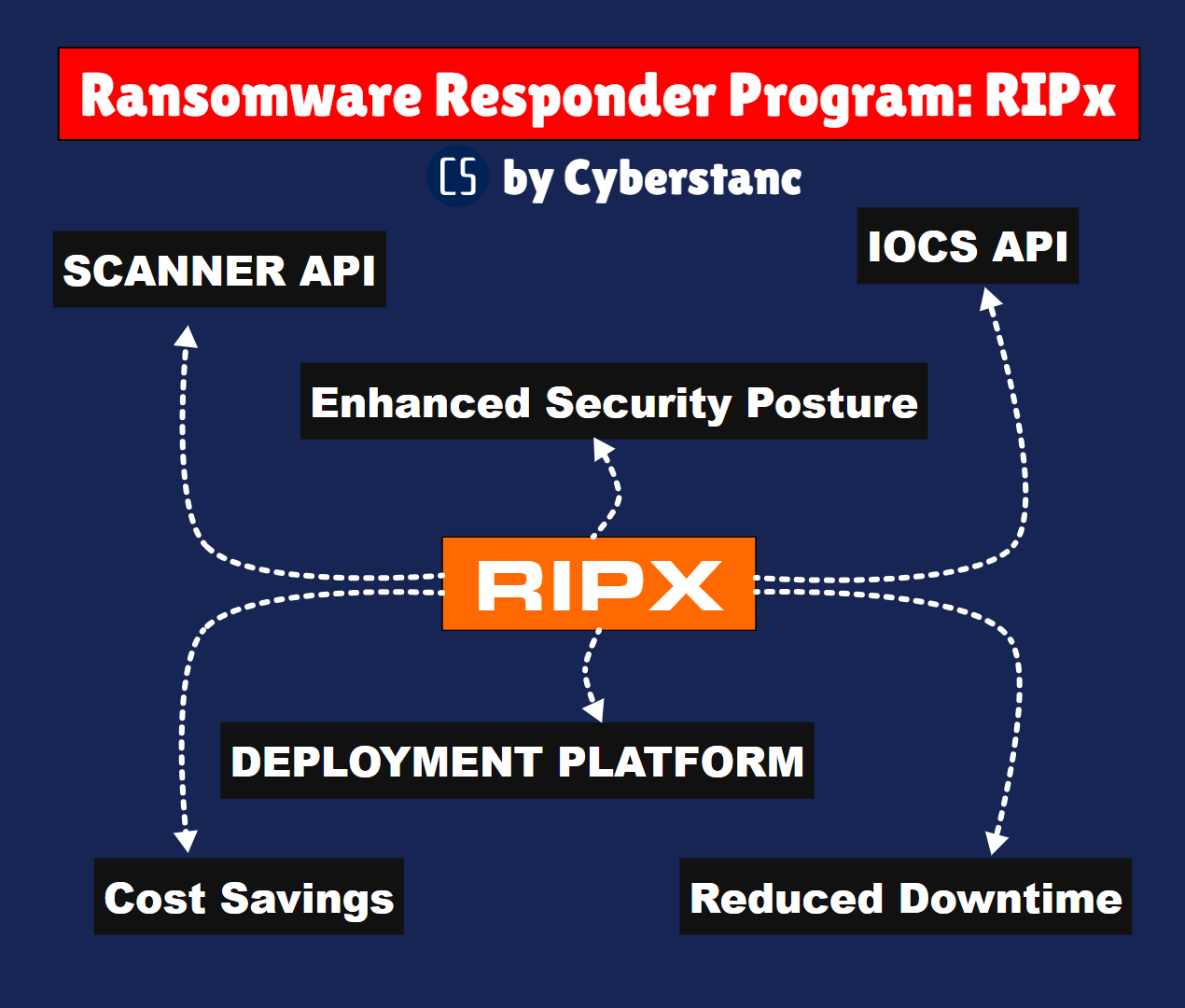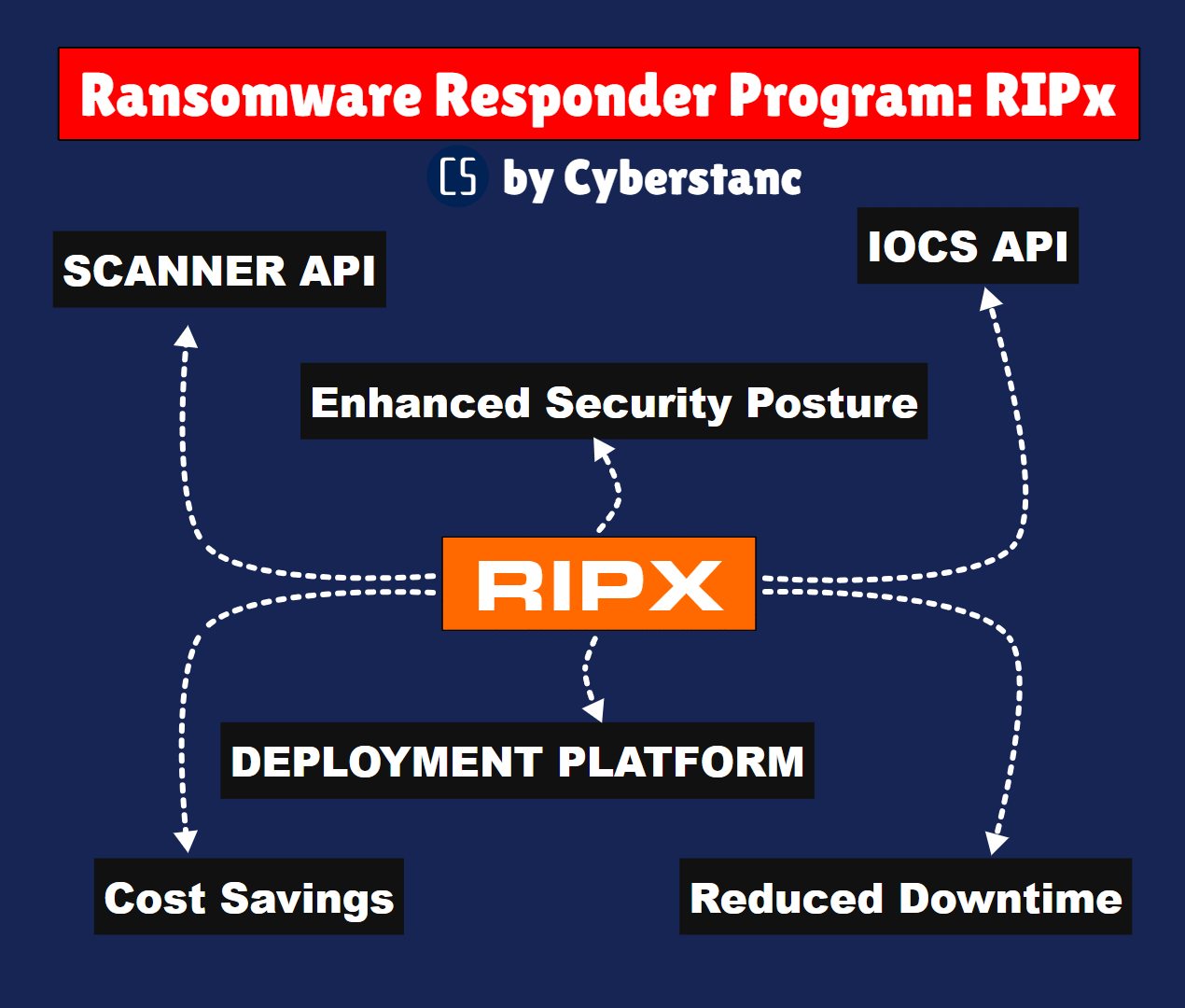
Benefits of Implementing RIPx
In a landscape where ransomware attacks continue to evolve, RIPx stands as a beacon of hope, providing a powerful defense against these digital extortion schemes.
Enhanced Security Posture: RIPx significantly bolsters an organization's security posture by proactively identifying and neutralizing ransomware threats.
Reduced Downtime: Swift detection and response minimize downtime, ensuring business continuity even in the face of potential ransomware attacks.
Cost Savings: By preventing ransomware attacks, organizations can avoid the costly ransom payments and potential loss of data, saving significant financial resources.
Case Studies
Case 1 : A finance conglomerate (UK)
Incident Overview:
A finance conglomerate was targeted by BlackCat/ALPHV ransomware, exploiting the CVE-2023-4966, aka Citrix Bleed. Initial compromise affected 12 machines, escalating to 150 due to an HR system breach.
Attack Vector:
The attacker exploited a Citrix vulnerability (CVE-2023-4966) for initial infiltration, compromising 12 machines. Subsequently, a HR system breach enabled the attacker to proliferate to a total of 150 machines.

Data Compromise:
BlackCat/ALPHV ransomware executed the encryption process on compromised systems. Sensitive data was at risk, prompting urgent action.
Response Strategy:
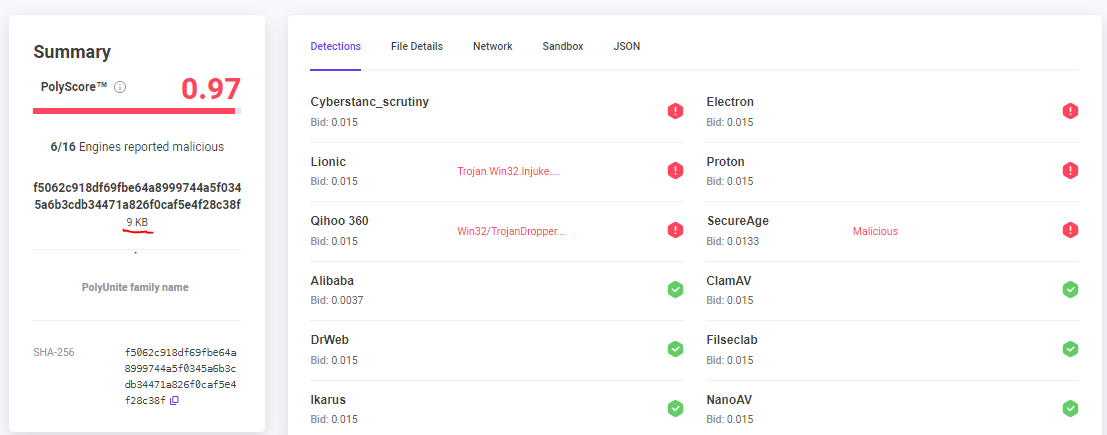
Utilizing our Scrutiny BlackCat /ALPHV module, our researchers thwarted ongoing encryption across all 150 machines. Swift response prevented data loss and potential financial impact.
Lessons Learned:
- Timely patching of known vulnerabilities is crucial.
- Scrutiny BlackCat/ALPHV module demonstrated its efficacy in halting ransomware process and detecting malware at initial stage, showcasing its vital role in cyber defense.
Case 2 : Industrial manufacturing giant (India)
Previous Reference: https://cyberstanc.com/blog/exposed-the-shocking-truth-about-purecrypter-attack-chain-and-its-connections-to-pakistan/
Introduction:
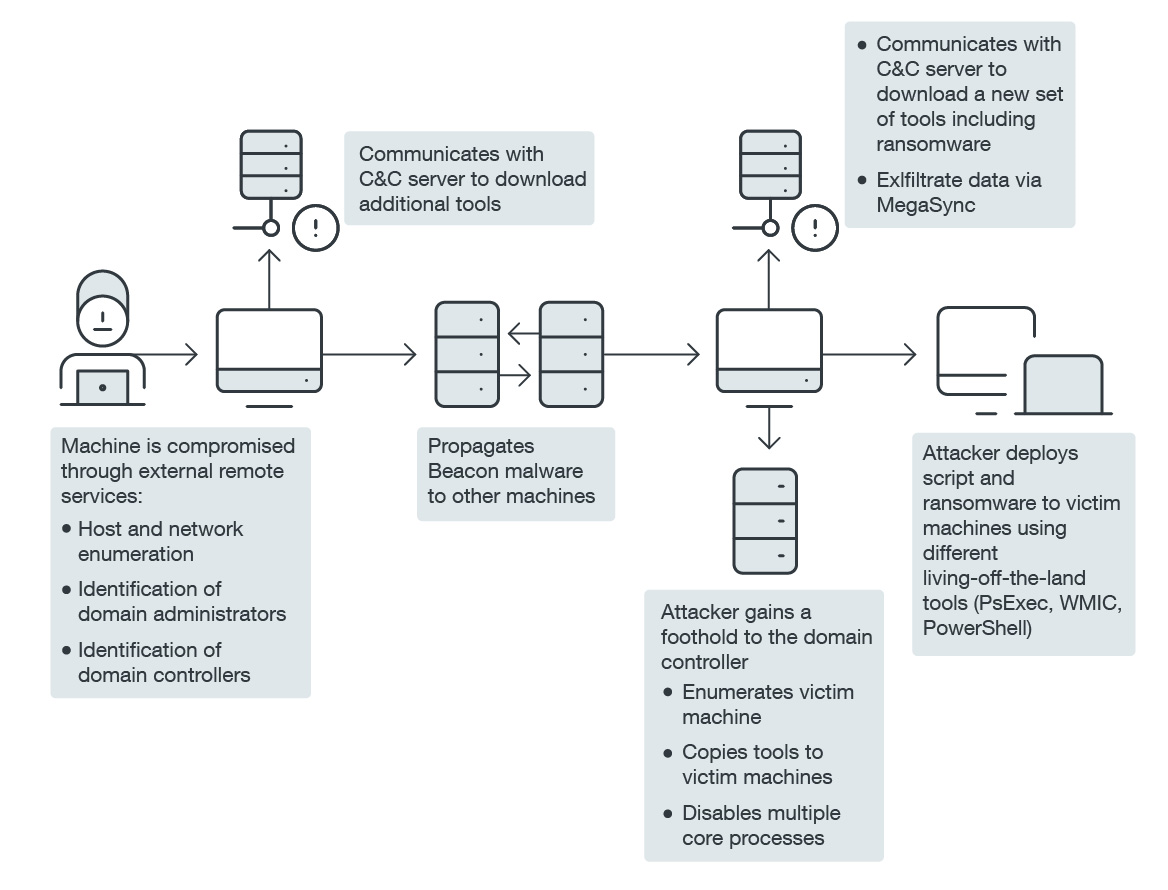
A prominent manufacturing corporation's server recently fell prey to an advanced cyber-attack. The attacker employed Mallox ransomware, a type of malicious software designed to encrypt data and demand a ransom for its release.
Attack Methodology:
The attacker breached the infrastructure, targeting a single Microsoft SQL (MSSQL) server. The initial attack vector was the deployment of PureCrypter loader, a malicious software used to drop other malware into the system.
Data Exfiltration & Lumma Stealer Execution:
The PureCrypter loader decrypted Lumma Stealer in the memory, which is designed to collect sensitive data such as cookies, usernames and passwords, credit card numbers, connection history, and cryptocurrency wallet data.
Additionally, the loader decrypted a custom stealer that traversed directories recursively, seeking out file formats like documents, images, and Excel sheets. This implied that the attacker's goal was rapid exfiltration of potentially valuable data.
Victim Management & Mallox Ransomware Encryption:
The attacker maintained control over the victim's compromised endpoints through a Cobalt Strike beacon, a commercial, full-featured, remote access tool.
This facilitated activities such as infrastructure reconnaissance, privilege escalation, and lateral movement. Finally, the Mallox ransomware binary was dropped, encrypting all machines under control.

Threat Mitigation:
Scrutiny endpoint sensor was able to identify and neutralize all active infections, including the initial access point of Pure Crypter and Mallox ransomware strain. The restoration of the encrypted machines was achieved through the Scrutiny Mallox module, a product of our dedicated R&D team.
Conclusion:
This case underscores the necessity of strong cybersecurity measures, especially for large organizations handling sensitive data. The attack serves as a reminder of potential system vulnerabilities and the importance of proactive defense mechanisms.
The Comparative Advantage: Cyberstanc Affiliates vs. Ransomware Group Affiliates
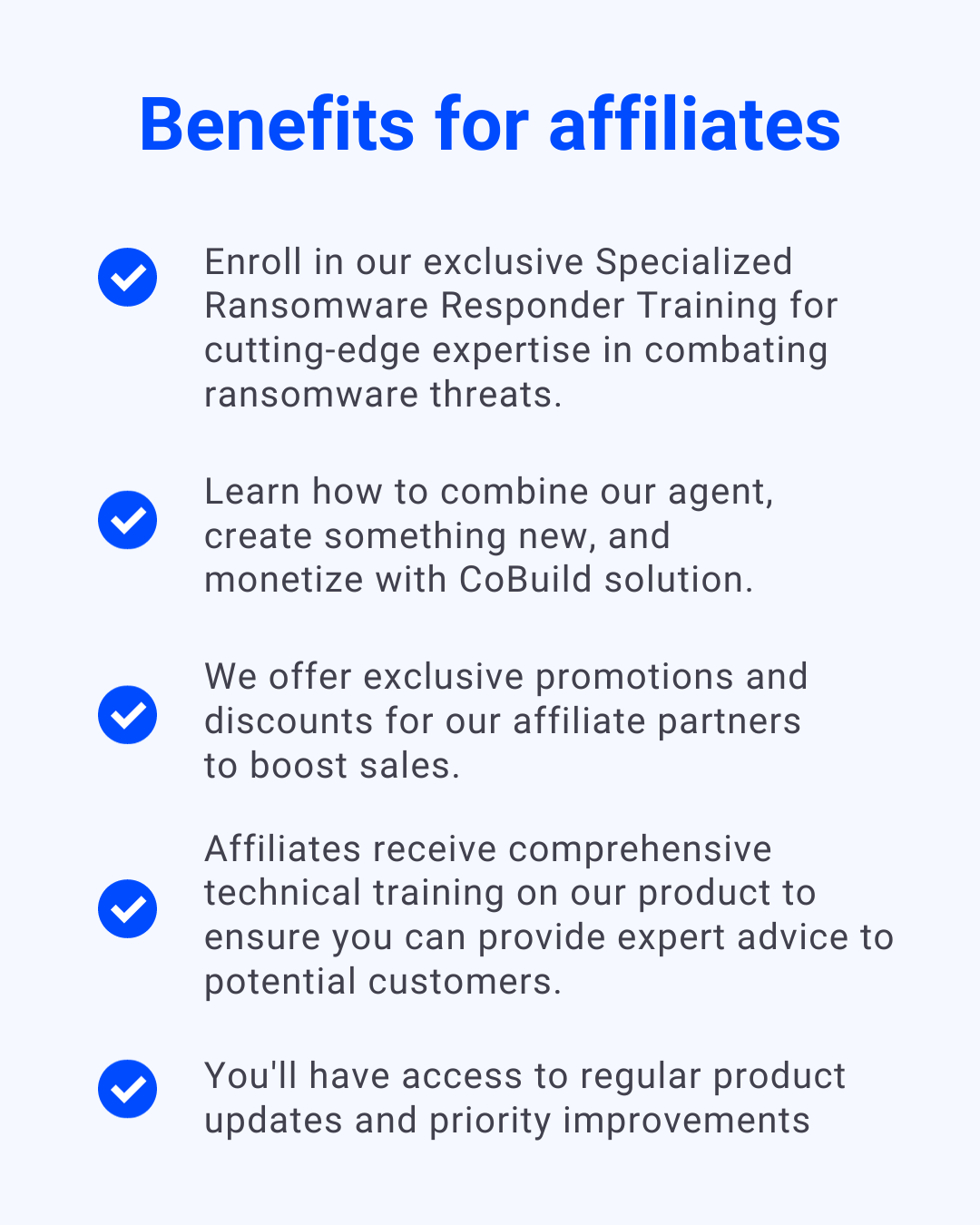
Conclusion
To explore opportunities with the RIPx program, feel free to contact us directly or tap into our extensive network of partners, including MSSPs and resellers, to begin your journey toward collaboration and innovation. For further details, email us at [email protected].
We'll promptly provide comprehensive information and support regarding the RIPx program and its implementation.
RIPx represents a paradigm shift in ransomware defense strategies, offering a proactive and robust approach to combatting these malicious threats.
By leveraging advanced technologies and proactive monitoring, RIPx empowers organizations to thwart ransomware attacks before they cause irreparable harm.
Stay protected. Stay proactive.
RIPx - kick ransomware to the curb!!
