Exposed: The Shocking Truth About PureCrypter Attack Chain and Its Connections to Pakistan

PureCrypter has emerged as a prominent initial access broker (IAB) in the dark web, collaborating with various threat actors to distribute malware campaigns. Acting as the main tool for IABs, PureCrypter's downloader and Command and Control (C2) server have been identified as the key components in a recent campaign that delivers a range of malware including Redline Stealer, AgentTesla, Eternity, Blackmoon, and Philadelphia Ransomware.
In recent months, a new attack chain has been identified that starts with an email containing a Discord app URL pointing to a PureCrypter sample in a password-protected ZIP archive.
It has been sold since March 2021 on “hxxps[://]purecoder.sellix.io/”, It is written in .net and supports all versions of Windows operating system. It was first detected in June 2022.
Its creator, @PureCoder, offers it for $59 per month or a one-time payment of $245 for life. The developer recently expanded its features to include PureLogs logger and info stealer, which can steal data from crypto wallets, web browsers, and email clients, for just $99 a year or lifetime access for $499.
PureCrypter is a .NET assembly and can be identified by the Magic and TrID headers. The malware is packed using a .NET packer and has a file size of 9 KB.
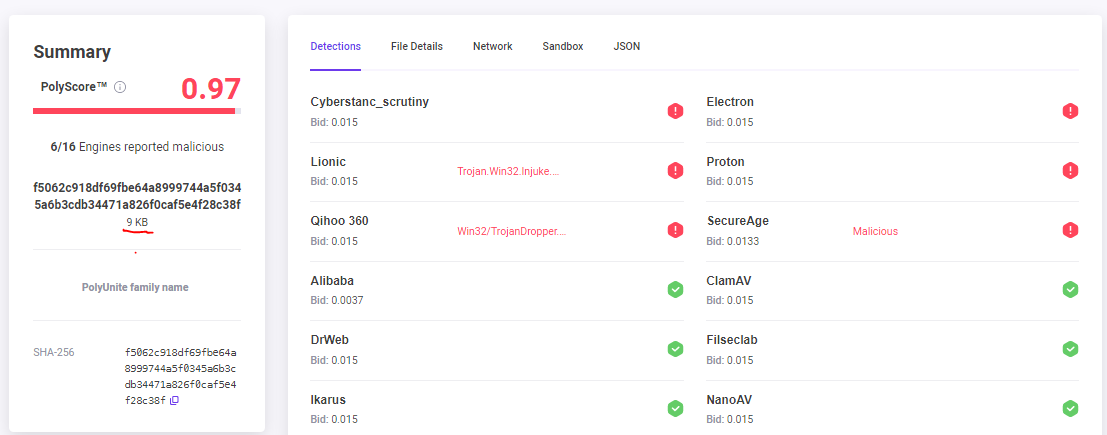
Polyswarm link :- https://polyswarm.network/scan/results/file/f5062c918df69fbe64a8999744a5f0345a6b3cdb34471a826f0caf5e4f28c38f
In this blog post, we will conduct a technical analysis of this sophisticated malware campaign and shed light on its stealth operations.
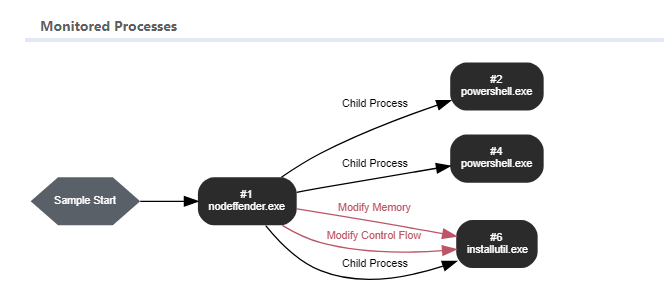
Infection Chain:
The malware campaign is distributed via Discord, and a link to the malware payload is sent via email. The payload is a password-protected ZIP file, and the password is 1234. The ZIP file contains a .NET loader called PureCrypter. The PureCrypter downloader then tries to download a secondary payload from the compromised site.
An email with a Discord app URL pointing to a malicious password-protected ZIP file is sent to the victim (https://cdn[.]discordapp.com/attachments/1006638283645784218/1048923462128914512/Private_file__dont_share.zip, pwd – 1234).
Investigation
AgentTesla/Red-line stealer establishes a connection to an FTP server where it stores the stolen victim's credentials. The FTP server appears to have been taken over, and the leaked credentials for the domain were found online, suggesting that the threat actors used these credentials to gain access to the server.
The PureCrypter campaign targeting government entities, uses process hollowing to inject the AgentTesla/Red-line stealer payload into a legitimate process to evade detection from antivirus tools.
Compromised FTP server showing collected victim information:
The FTP server was also used in a campaign using OneNote to deliver malware. The attackers sent phishing emails with links to malicious OneNote files that could download additional malware or steal information from the victim's device.
FTP server – ftp[://]ftp.mgcpakistan[.]com – as part of its infection process!

What makes this attack chain particularly noteworthy is its connection to a Pakistan-based FTP server used to receive stolen data. The threat actors take control of the particular FTP server, rather than setting up their own, to reduce identification risks and minimize their trace.
It is unclear if the Pakistan-based server was compromised specifically for this campaign or if it was a pre-existing compromised asset used by the threat actors.
Under that same email address, another malicious email titled “New Order” was also uncovered with an attached malware file.
Infection Tactics/Technical Details:
It was discovered that the threat actors used process hollowing to inject the AgentTesla payload into a legitimate process ("cvtres.exe") to evade detection from antivirus tools.
Furthermore, AgentTesla uses XOR encryption to protect its communications with the C2 server, like its configuration files and operations from network traffic monitoring tools.
TTPs Analysis:-
Connect with us:-
Our dedicated R&D center is constantly developing cutting-edge technologies to combat emerging threats such as malicious software and APTs. We take pride in offering our clients a strong partnership for gathering Scrutiny Engine Detection Intelligence, which allows us to provide the most effective tools and strategies to enhance their security posture.
With our free trial offer, you can experience the full potential of our security solutions for 31 days, including powerful threat intelligence, malware detection, and analytics at no cost. Additionally, our Secure-Tech service provides internal and third-party application scrutiny scans, using our convenient Pay-As-You-Go model.
At Cyberstanc, we are committed to ensuring a safer and more secure digital world for all. Contact us today at [email protected] to learn more about how our advanced cybersecurity solutions can protect your organization from cyber threats.
🚨 💻🔐 [email protected] 🚨 💻🔐
