Cyberstanc Vortex: A Futuristic Approach to Cybersecurity with Unmatched Accuracy and Reliability in Threat Detection and Mitigation

The rise of cyber attacks and supply-chain attacks has made it necessary for businesses to invest in advance protection to protect against malware and advance threat to enhance overall protection capabilities.
In this blog, we will delve deeper into what Cyberstanc Vortex is and how it offers better technology and detection prospects than other available platforms.
Cyberstanc Vortex is a cutting-edge threat detection platform that is set to revolutionize the way organizations protect themselves from cyber threats. It is a platform that combines state-of-the-art tools, services, and proprietary engines to extract Indicators of Compromise (IOCs) and threat information from files, documents, images, and unknown file types at scale and speed.
Inspired by the natural abilities of the peacock, this cutting-edge platform is designed to excel at catching all kinds of cyber threats - just like how the peacock excels at catching worms, rats, snakes, and other creatures. But that's not all. The peacock's iridescent feathers attract mates, just like the scrutiny engine detects unnoticed malware, and offers protection against predators.
The solution goes deeper than traditional static analysis tools and provides actionable intelligence in many more cases, reducing the number of artifacts that need to be sandboxed in an otherwise time-consuming and resource-intensive process.
**State-of-the-Art Threat Detection**
The Cyberstanc Vortex platform offers a technical demo showcasing its easy API integration and agent-based use cases for endpoint, network, email, and storage protection. Its state-of-the-art threat detection system covers most of the grey areas that attackers target or plan to exploit in the future.
Scrutiny integrated engine and custom co-build agent includes wide range of executables, documents, scripts, and common file-types.
Simulation Intelligence of highly obfuscated and real-word malware techniques including macro malware, VBA, VBS, PowerShell, DOCx, Calender files, One-Note, Jscript, MSHTA, XSL, and WSF.
Rapid and deep analysis at high scale, REST API for automated integration.
Simple and cost-effective on-premises standalone deployment or public-private cloud.
Designed, engineered, and maintained by experienced Cyberstanc experts.
Vortex integrates with other security infrastructure, including YARA and MITRE ATT&CK framework, to provide accurate threat detection. Users can add custom YARA rules, and the platform automates some of the analysis and mitigation tasks, reducing the workload of human analysts.
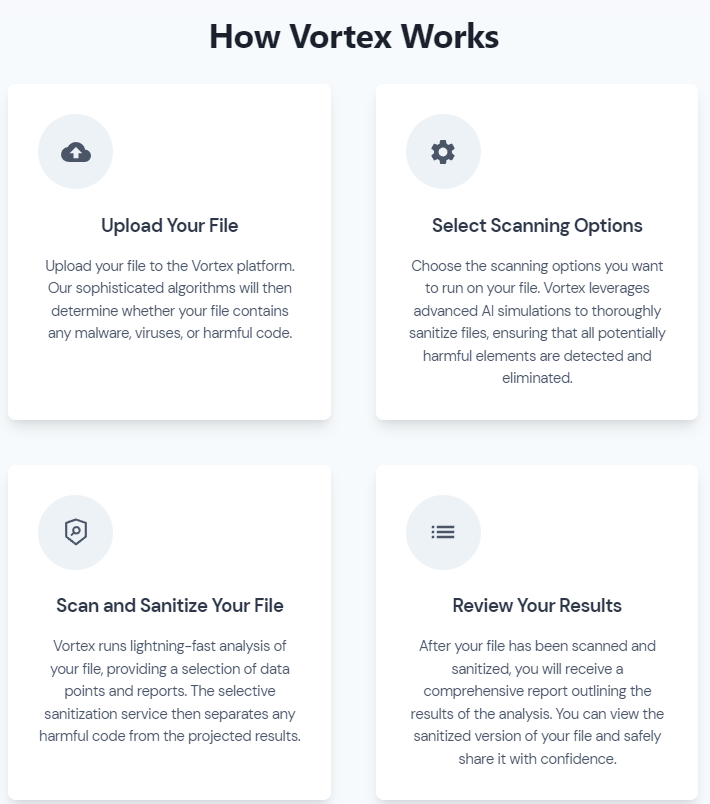
Vortex's Approach to Detection: Transparency, Interpretability, and Accuracy
Vortex places great emphasis on transparency and accountability in their detection engine, recognizing the importance of understanding how a detection system works in order to build trust in its accuracy.
With detailed information on how our detections are designed, built, and how decisions are made, security teams can be confident in their ability to detect and respond to threats. Additionally, Vortex strives to minimize false positives while maintaining interpretability and transparency, striking a balance between detection accuracy and threat visibility.
By offering a guarantee of performance for their managed or curated detections, Vortex further reinforces their commitment to transparency and accountability. This not only builds trust in their system but also helps to reduce the risk of false positives. Overall, Vortex's approach to detection emphasizes trust and transparency, which is increasingly important in an industry that is moving towards more sophisticated detection methods.
Streamline Your Threat Analysis with Next-Gen Tools and REST API Integration
The Vortex API provides a way for developers to interact with the Vortex detection engine programmatically. The API documentation includes endpoints for various functions such as user registration, login, file upload, and download.
Developers can use these endpoints to integrate Vortex's detection engine into their own security applications or workflows. For example, a security application could use the Vortex API to scan files for malware before allowing them to be uploaded to a server.
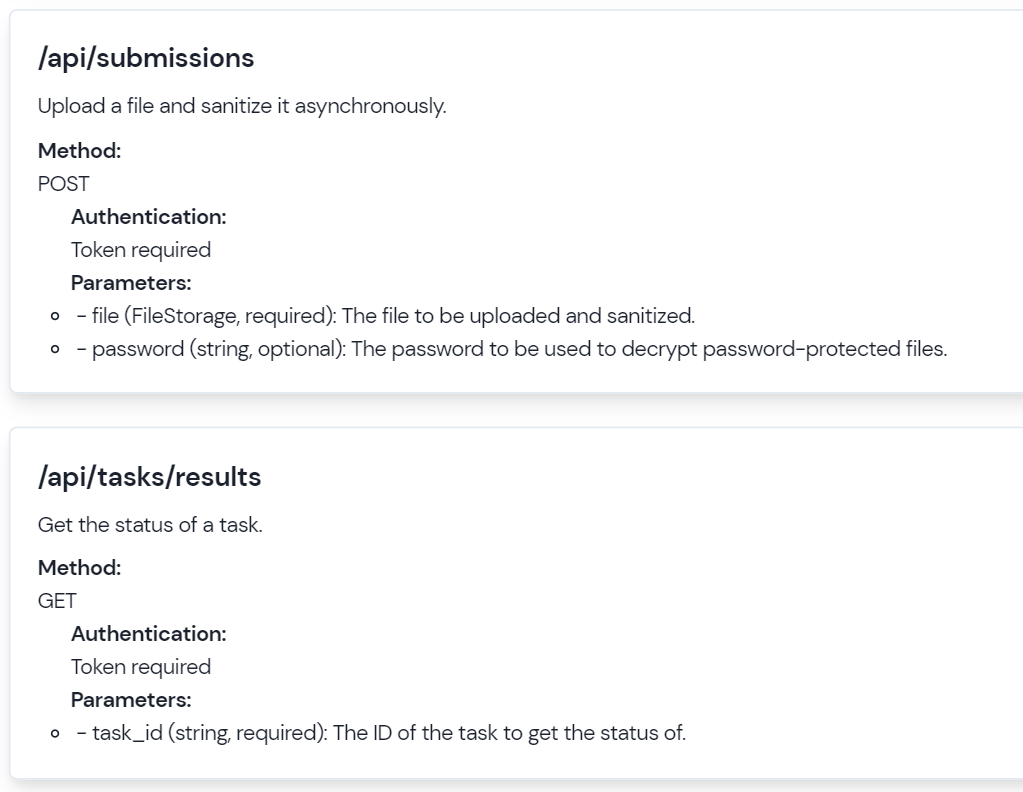
To ensure security, the Vortex API uses token-based authentication, which requires users to authenticate using an access token. This helps to prevent unauthorized access to the API and ensures that only authorized users are able to interact with the Vortex detection engine.
Understanding the Recognized Media Formats for Deep Archives
Note: When using a file upload feature, it's important to keep in mind that the maximum default file size is 99MB per upload. However, this can be configured to accommodate larger file sizes in on-premises deployments.
Additionally, it's worth noting that the MIME type of the uploaded file is automatically detected regardless of the provided file suffix. This can help ensure that the uploaded file is processed and handled correctly, regardless of any discrepancies between the file extension and its actual contents.
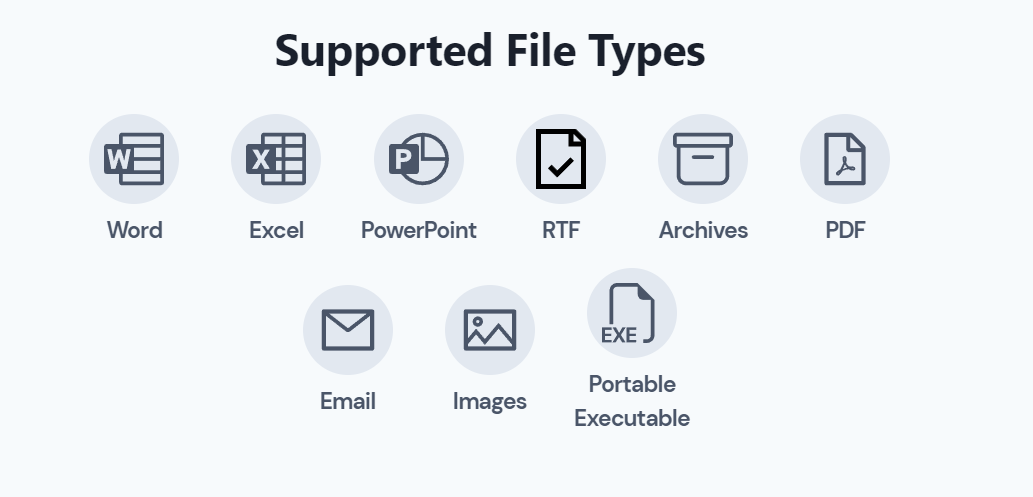
Common Archives: 7Z, ACE, GZIP, LZIP, ISO, RAR, TAR, ZIP
Microsoft Office Files: DOC, DOCM, DOCX, DOT, DOTM, DOTX, PPSX, PPT, PPTM, PPTX, XLS, XLSM, XLSX
Email Files: EML, MBOX
Web Files: HTA, HTML, SVG
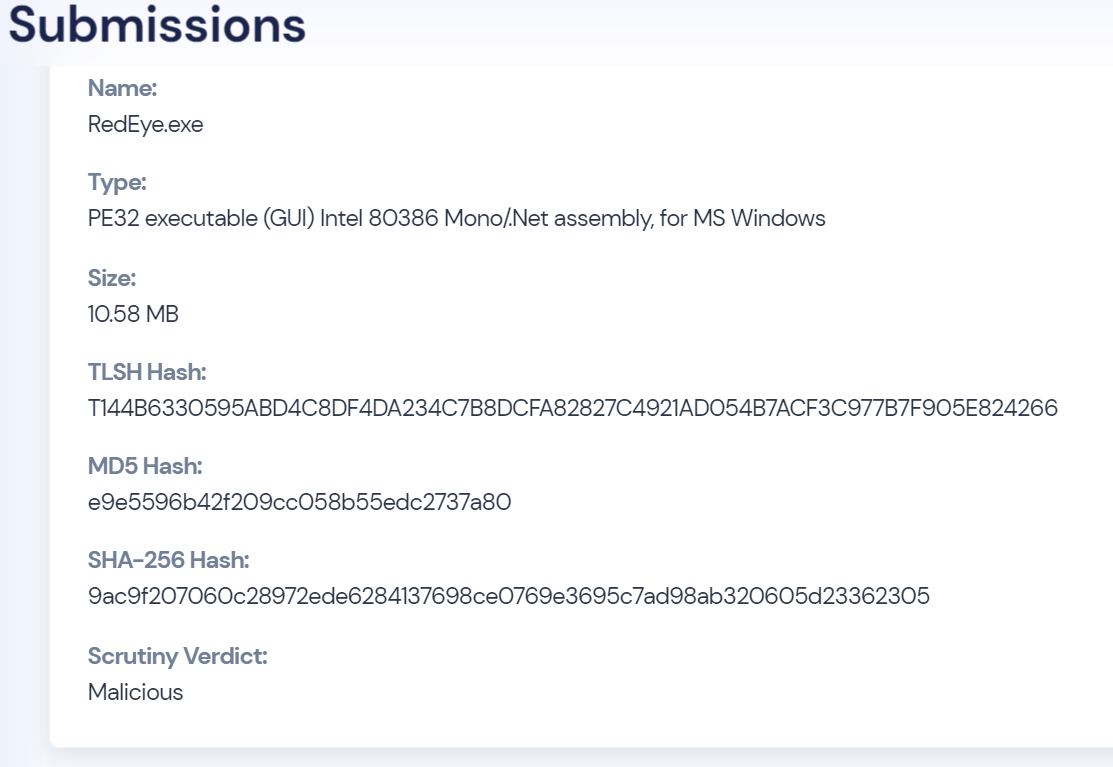
Scrutinized-Eyes on Malware Installation File Types: .exe, .dll, .bat, .cmd, .js, .vbs, .docm, .xlsm, .pptm, .jar, .py, .scr, .reg, .ps1, .hta, .chm, .lnk, .msi, .pif, .com.
Automating Analysis and Mitigation Tasks with Vortex Integration
Integration of the Vortex with existing security infrastructure could provide several benefits.
First, it could improve the accuracy of threat detection by incorporating machine learning algorithms into the analysis process, users can add custom YARA rules, and threat feeds integration with a TIP, SOAR, SIEM system, such as Microsoft, IBM or Splunk.
Second, it could improve the response time to cyber threats by automating the mitigation process. In addition, the Vortex's automated mitigation process can continuously learn and adapt to new threats, improving its effectiveness over time.
Third, it could reduce the workload of human analysts by automating some of the analysis and mitigation tasks. For example, the Vortex can be configured to prioritize high-risk threats and take immediate action to mitigate their impact, while lower-risk threats can be flagged for further analysis by human analysts.
Get the Best of Both Worlds with Vortex Cloud and On-Premises Deployment
To support both cloud and on-premises deployment of Vortex, the platform can be installed and configured to run on cloud infrastructure such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP). This allows customers to take advantage of the scalability and flexibility of cloud computing while still benefiting from Vortex's malware detection capabilities.
For on-premises deployment, customers can install Vortex on their own servers or hardware with minimum server configuration of Window/Ubuntu Server, 8 vCPUs, 16GB RAM, and 32GB SSD. Customers can scale up their hardware configuration based on their specific needs and the number of scans they require per day.
Scaling Vortex for High-Volume Scanning Needs
The peak performance for a single-server deployment of the Vortex is 50,000 scans per day or approximately 1,500-2500 scans per hour. The average processing time per scan is around 3-5 seconds, though it can vary based on the input mix.
If the customer requires more than 100,000 scans/day, a custom multi-server setup is necessary and needs to be scoped out with the engineering team.
Cyberstanc Vortex vs. Virus Total: A Technical Comparison
When it comes to malware detection and analysis, VirusTotal is a popular tool that is often used by security analysts and researchers. It allows users to upload files and URLs for scanning, and uses multiple antivirus engines to detect any potential threats.
Cyberstanc Vortex provides comprehensive analysis by examining metadata, file structure, and relationships between files to identify threats with simulation intelligence. Its ability to analyze third-party apps sets it apart such as plugins and extensions, to detect any hidden threats.
Another advantage of Cyberstanc Vortex is its ability to provide actionable intelligence. Major anti-virus solutions in Virus Total may flag a file as suspicious, but they may not provide any information on how to mitigate the threat.
Finally, Cyberstanc Vortex detections accuracy is much faster than traditional anti-virus solutions, who majorly rely on malware signature. It can analyze files and codes at scale and speed, allowing security teams to quickly identify and respond to threats. Additionally, it reduces the number of artifacts that need to be sandboxed, saving time and resources.
With Cyberstanc Vortex, however, users receive detailed information on the nature of the threat, including the type of malware and its behavior. This allows security teams to take immediate action to contain and remediate the threat.
** No-Data Acquisition Policy: A Game Changer in User Privacy
Cyberstanc Vortex is designed with user privacy in mind. The platform does not collect any data from the user or their system. No company information is uploaded to mass users or any third party without the user's consent. This ensures that the user's data is safe and protected.
Problem-solving Industry case studies
The Vortex is a powerful tool that can help organizations across different industries protect themselves from cyber threats.
Here are some examples of how the Vortex can be used in specific industries:
Financial institutions are no strangers to cyber threats, particularly when it comes to banking trojan, data-theft and ransomware attacks.
For example, the Vortex can be integrated into a financial institution's security infrastructure to analyze suspicious emails and attached documents. It can also monitor file activity to detect any unusual behavior that may signal a malware or ransomware attack.
Critical infrastructure is also vulnerable to cyber threats that could have catastrophic consequences. The Vortex can be used to create air-gap containers and train models to determine what data should be allowed to pass through the container.
For example, a critical nuclear or power plant could use the Vortex to analyze data from sensors and determine if any readings indicate a potential safety risk. If a safety risk is detected, the Vortex could take action to mitigate the risk.
In the supply chain, the Vortex can be used to analyze and validate new software before it is applied to a system.
For example, a software development company could use the Vortex to analyze a new release and determine if it contains any malicious code. If it does, the company could take action to remove the malicious code before releasing the software to customers.
The military could also use the Vortex to detect and mitigate cyber threats at the local level.
For example, if a military installation notices suspicious activity on their network or reverify a usb, the Vortex could analyze the activity to determine if it poses a threat. If it does, the Vortex could then take action to neutralize the threat.
Final thoughts
It offers a wide range of features that go beyond the capabilities of traditional static analysis tools, making it an ideal choice for organizations looking to enhance their security posture.
Unlike other threat intelligence platforms, Cyberstanc Vortex does not collect any data or upload any company information, making it a reliable and trustworthy choice for organizations concerned about data privacy and security.
The Vortex can be integrated with existing security infrastructure, allowing organizations to improve their threat detection and response capabilities, automate some analysis and mitigation tasks, and reduce the workload of human analysts. With its simple and cost-effective deployment options, Cyberstanc Vortex is an accessible solution for organizations of all sizes and industries.
At Cyberstanc, we are committed to ensuring a safer and more secure digital world for all.
Apart from our Vortex platform, we also provide the RIPx scanner and threat intelligence service. This powerful service is designed to provide real-time threat detection and analysis, using cutting-edge technology and threat intelligence. It has already been consumed by product-based companies, Auditors, Pen-testers and our threat intelligence partners and OEM clients providing them with comprehensive detection mechanism.
Is your organization ready to combat the evolving cyber threats? Contact us at [email protected] to explore our advanced cybersecurity solutions. Our cutting-edge Vortex platform, AV/EDR companion, and more can protect your business. Schedule a in-house demo or meeting at https://cyberstanc.com/request-a-demo/ and secure your future.
Additionally, join us in shaping the future of cybersecurity technology through the exciting co-build opportunity offered by Vortex, the ultimate platform designed specifically for SOC teams, Threat Hunters, and Researchers.
With Vortex, you'll have all the tools you need to combat cyber threats at your fingertips. Experience its power with a 30-day freemium access, allowing you to explore its full capabilities.
Visit https://vortex.cyberstanc.com/ and Sign-up today!
