The Truth About Hash Signatures and Malware Detection
It is common for malware samples to remain undetectable for hours or days or even weeks.
This is because malware writers are continuously creating new techniques to evade detection. As a result, it is necessary for users to have a comprehensive and fast detection rate for malware.
To use VirusTotal or other multi-scanning platforms, users can submit a file on the website or use the email submission feature. Users can also search the existing database of scanned files based on a sha1, sha256, or md5 hash value. After the upload, the file is scanned with different products and their engines, and the results are available for everyone.
To bypass antivirus software, malware creators often use techniques like obfuscation, encryption, and polymorphism.
Obfuscation is the process of disguising the code to make it harder to detect. Encryption involves encrypting the malware code to make it unreadable to antivirus software. Polymorphism is the ability of malware to change its code every time it's executed, making it even more difficult to detect.
In case some products or engines are not detecting the sample as malware, the file was not rated malicious by using the signatures provided in that particular engine or product.
If a malicious file is not detected as malicious in such a multi online scanner, users cannot automatically conclude, out of this analysis, that some new malware is actually not detected or stopped by their AV product.
To combat malware bypassing, antivirus software vendors use a variety of techniques. One such technique is behavioral analysis, which involves analyzing the behavior of the malware rather than its code. Another technique is machine learning, which involves training a machine learning algorithm to recognize malware based on patterns in the code.
A huge difference users should know about while using the public services. The online multi scanner analyses can give users an initial idea of the file checked, but not more. Users need to know how to interpret and read the results properly.
Unfortunately, some script kiddies or wannabee malware writers are still using public online scanning services to test their newly created malware creations and to check whether they are detected or not.
Underground members have set up their own services and sites where they can upload their own new malware. These sites are not forwarding the files to the security software vendors. If users stumble upon such an underground scanner website, they cannot rely upon the results presented.
Case Study:- Beware of Valyrian Malware: Named After Game of Thrones' Indestructible Steel, Now Targeting Your Computer

Valyrian Malware, named after the indestructible steel in Game of Thrones, is a particularly dangerous malware that poses a significant threat to computers and cybersecurity. The malware is distributed through fake Windows updates, malicious third-party applications, or weaponized attachments sent via email or social media.
Recently, a phishing attempt targeted an unsuspecting recipient with a password-protected ZIP file containing a malicious Word document. Once the malware infects a system, it remains concealed and executes its malicious activities every time the computer is turned on. This makes it particularly difficult to detect and prevent, as traditional anti-virus solutions may not be able to identify the malware.
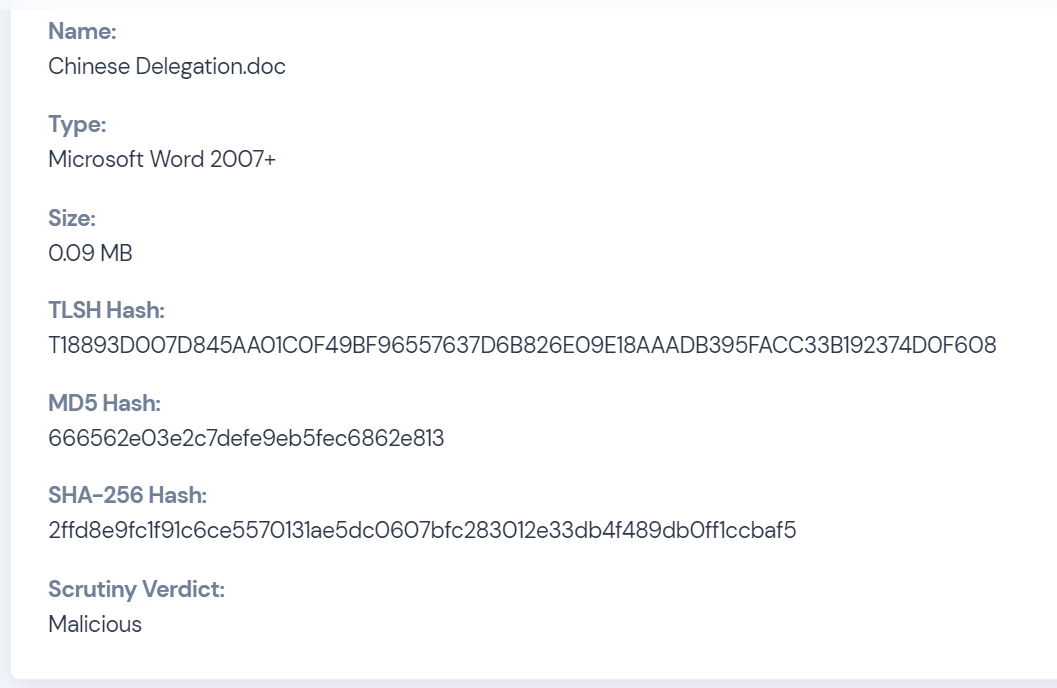
It is important to note that Valyrian Malware can be disguised in innocuous-looking files like 'Chinese Delegation.doc.' This highlights the need for computer users to exercise caution when downloading or opening attachments, especially from unknown or suspicious sources.
Valyrian Malware is an example of a zero-day exploit, which means it is a vulnerability that is unknown to software developers or security professionals. As a result, there may not be any available patches or fixes to prevent the malware from infecting a system.
Valyrian Malware is capable of performing a wide range of malicious activities, including stealing sensitive information, installing other malware, or even taking over control of the infected computer. The malware is designed to remain undetected for as long as possible, making it a dangerous and persistent threat.
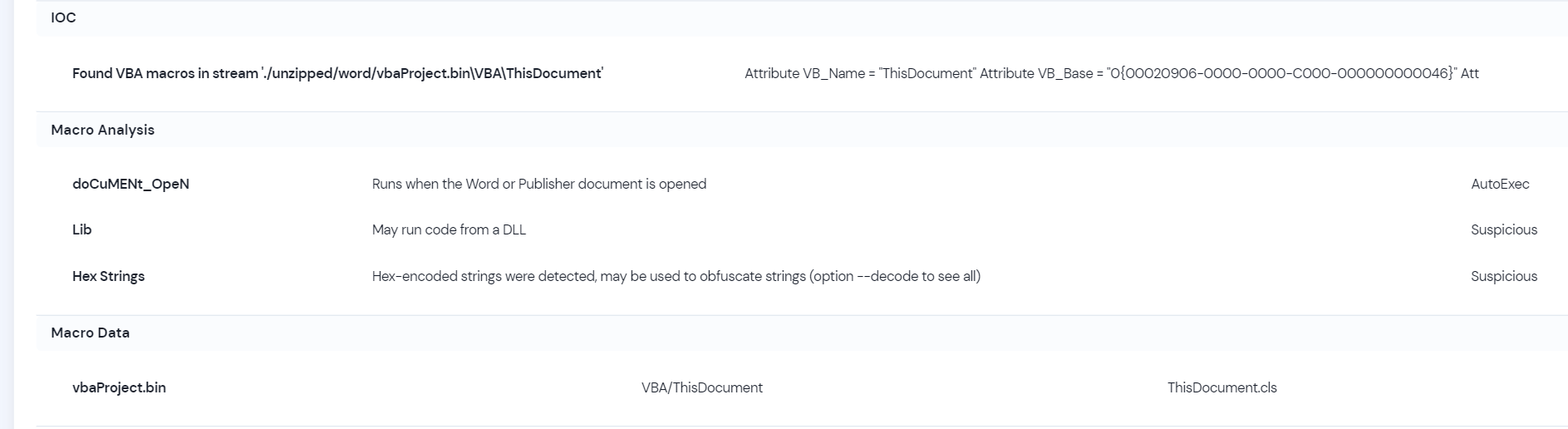
The recent phishing attempt used a password-protected ZIP file containing a malicious Word document that exhibited heuristics such as macro with DLL reference and macro with startup hook, common tactics for accessing APIs. This breakthrough in threat detection and prevention is a game-changer. However, there are still many anti-virus solutions that are unaware of the threat.
This myth is probably because people equate signatures with pattern-based detection.
AI-based malware detection is not a replacement for traditional antivirus software but a new complement to it.
The undecidability of virus/malware detection does not mean it is impractical, but constant work and improvements are necessary to stay useful.
New methods go far beyond pattern signatures and hashes, including emulation, deep scanning, in-memory scanning, algorithm-based signatures, behavior blockers, network scanning, and artificial intelligence (AI).
EDR/Antivirus products cannot afford false positives and are unfairly compared to applications that can avoid disrupting legitimate user activity.
VirusTotal testing strategy is flawed because scanning engines on VirusTotal only support a fraction of the capabilities that the real products have.
Malware developers are actively trying to create malware that antivirus products cannot detect.
AI technologies serve many purposes, including malware clustering, malware detection on client systems, and automatic signature creation.
The Role of Emulation and Depth Scanning in Malware Detection
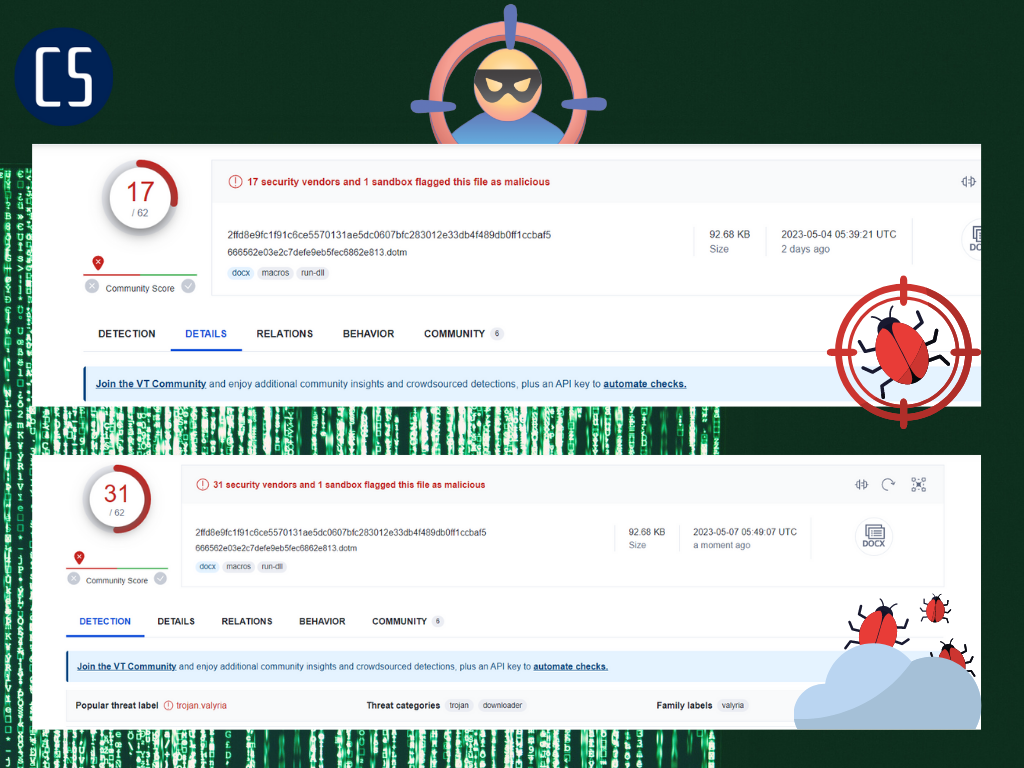
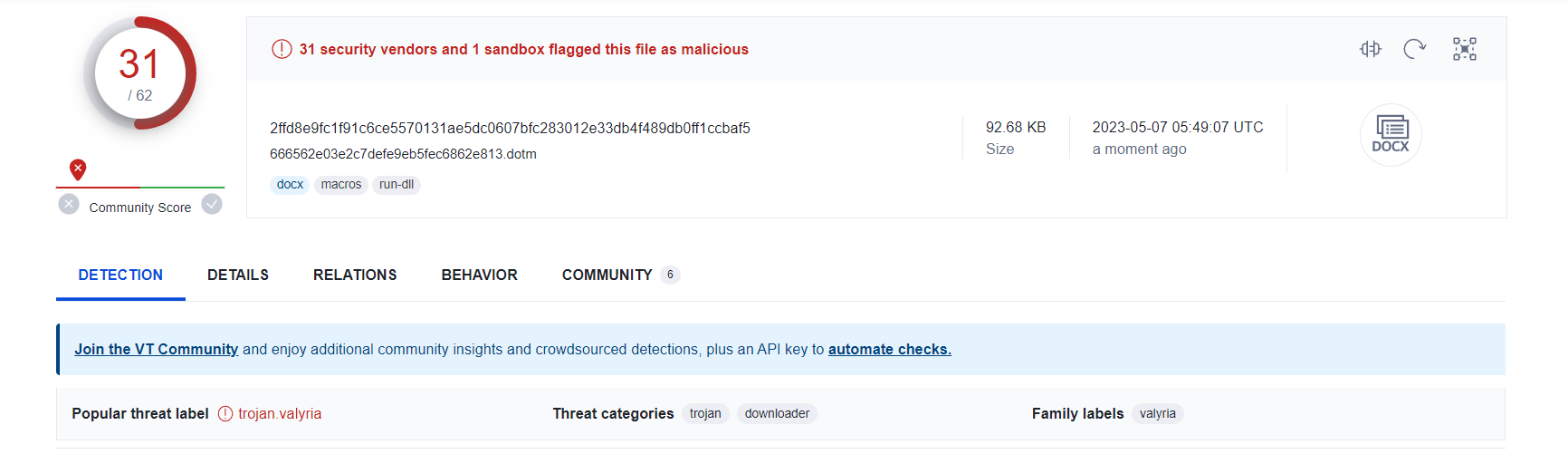
Recently, an innocuous looking file named 'Chinese Delegation.doc' 2ffd8e9fc1f91c6ce5570131ae5dc0607bfc283012e33db4f489db0ff1ccbaf5 was used in a phishing attempt that could have caused significant damage. The file was actually a password-protected ZIP file containing a malicious Word document, which exhibited heuristics such as macro with DLL reference and macro with startup hook. These are common tactics for accessing APIs, which can be used to carry out cyber attacks. .
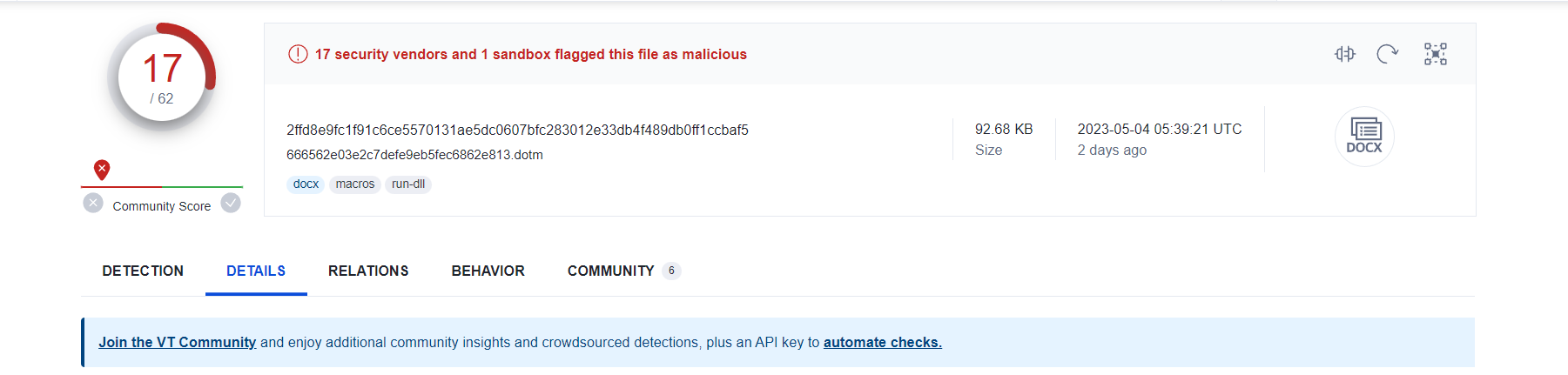
Traditional antivirus solutions were unable to detect the malware until 1-2 weeks after the initial attack. In fact, many antivirus solutions still lack the ability to detect such threats. The hash "2ffd8e9fc1f91c6ce5570131ae5dc0607bfc283012e33db4f489db0ff1ccbaf5" is a virus dropper that was uploaded with few detections, and later adopted by AV vendors.
To bypass solutions, attackers use several techniques.
For example, they might encrypt the payload using various encryption techniques. They also obfuscate the code, so that it becomes difficult to reverse engineer.
Another technique is to create a dropper that downloads the payload from a remote server, making it difficult for the antivirus to detect.
One of the most common techniques used by attackers is "fileless malware." This type of malware operates entirely in memory and leaves no footprint on the system's disk. It runs as part of a legitimate process and is almost impossible to detect using traditional antivirus solutions.
Some EDR/Antivirus solutions have been using other malware detection technologies for at least a decade. These technologies include emulation, depth scanning, in-memory scanning, algorithm-based signatures, behavior blockers, network scanning, and more. While other antivirus solutions still use pattern signatures and hashes.
The Risks of Relying Solely on Signature Hash Pass in Malware Defense
The process of re-scanning entails the submission of a previously analyzed file to VirusTotal and performing a fresh analysis utilizing the latest versions of antivirus (AV) engines.
This enables researchers to ascertain if new detection techniques have been implemented and if the AV engines have updated their databases with new signatures for known malware or new nomenclature based on scanning.
The practice of re-scanning a previously analyzed file can potentially result in the detection of previously unnoticed threats, which can then be flagged and added to the AV databases.
This approach enhances the detection and prevention capabilities of all users. However, it should be noted that this method relies on the collection of signature database hashes against new variants or existing malware families.
In conclusion, malware detection is an ongoing battle between attackers and defenders.
If these solutions are not regularly updated or evolved, they are doing nothing to participate in the cyberwar between anti-malware software and malware authors.
As many advance APT and ransomware groups use various techniques to hide the internals of malware, making it difficult to detect and analyze. Packer compresses the original malware file, making it unreadable until it decompresses itself at runtime.
Crypters encrypt, obfuscate, and manipulate malware to make it difficult for security programs to detect. Protectors are software that keeps an application encrypted and protected against reverse engineering, with some added features that build several protective layers around the payload that researchers have to face.
Although these techniques make it challenging to detect and analyze malware, tools and programs are available to identify commercial packers and advise on how to unpack them.
Don't wait until it's too late to secure your organization's digital assets. Cyber threats are constantly evolving, but so are our cybersecurity solutions. Our team at Cyberstanc is committed to staying ahead of the curve and providing the latest in threat intelligence, malware detection, and analytics.
Interested in learning more? Shoot us an email at [email protected] and let's start a conversation about how we can help you protect your organization. With Vortex, our powerful cybersecurity platform, you'll have access to cutting-edge technology that can help you stay one step ahead of cybercriminals.
Our R&D center is always developing new technologies to fight against malicious software and APT groups. And with our Pay-As-You-Go model, you can be sure that you're only paying for what you need.
