OPSWAT collaboration with Cyberstanc™
We officially joined OPSWAT as a partner in 2021, becoming one of the trusted MetaDefender Core Engine suppliers alongside Microsoft Defender, Crowdstrike, McAfee, and Sophos. OPSWAT a industry-leading cybersecurity solutions combat malware and zero-day attacks, trusted by 98% of U.S. nuclear power facilities for safeguarding against major threats. Our engine now plays a key role in this vital mission.
This journey began in 2020 when we rigorously tested our engine, ensuring it met all use case requirements, participated in testing groups, and adhered to OPSWATs high standards and compliance benchmarks for public and federals offerings.

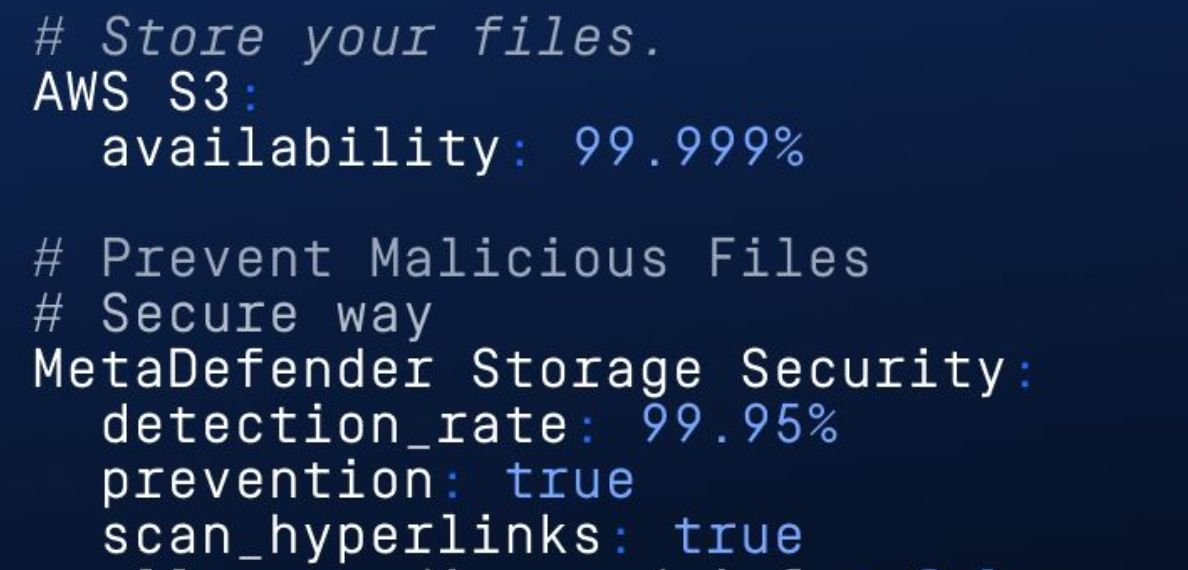
Through our strategic partnership with OPSWAT, multi-scanning technology that enhances outbreak detection by employing a diverse set of anti-malware engines sourced from various geographical locations. This robust approach combines heuristic and signature-based detection methods, with deep analysis proving particularly effective in identifying novel threats that often emerge at the onset of an outbreak.
By utilizing over 30 anti-malware engines for simultaneous file scanning, our advanced threat detection and prevention technology not only boosts detection rates but also significantly reduces outbreak response times by our scrutiny engine.
To quantitatively assess detection efficacy for various software packages, OPSWAT evaluates the anti-malware engine(s) that first detected an outbreak and cross-references that with the relevant package containing those engines.
Highlights
Scrutiny Engine: Our engine is one of the only five AI engines that utilize simulation intelligence for advanced ransomware detection.
Partnership with OPSWAT: Our collaboration includes the OEM Malware Sharing Program for API-based malware sharing and false-positive reporting. OPSWAT is a trusted vendor for agencies like the NSA, FBI, CISA, and DOD, serving 60% of U.S. manufacturing and critical infrastructure facilities with over 1,000 customers.
Cyberstanc Technology: Our self-learning engine powers an endpoint detection and protection platform, employing a unique crypto-caging methodology to defend against known and unknown ransomware.
Intelligence and Emulation: Cyber Threat Intelligence collaborates with our R&D center for continuous product upgrades, while our emulation of ransomware techniques enhances detection capabilities against evolving threats.
Organizations, especially large corporations with thousands of employees and contractors, encounter significant challenges in monitoring and securing data transmission channels that pose security risks.
Data transfer methods—including file uploads, portable media, and email attachments—serve as potential vectors for targeted attacks. However, enhanced results can be achieved locally with Scrutiny’s customized detection levels, providing tailored protection against these threats.
Partnering with OPSWAT, we elevate our cybersecurity offerings and receive global acclaim for our innovative approach.
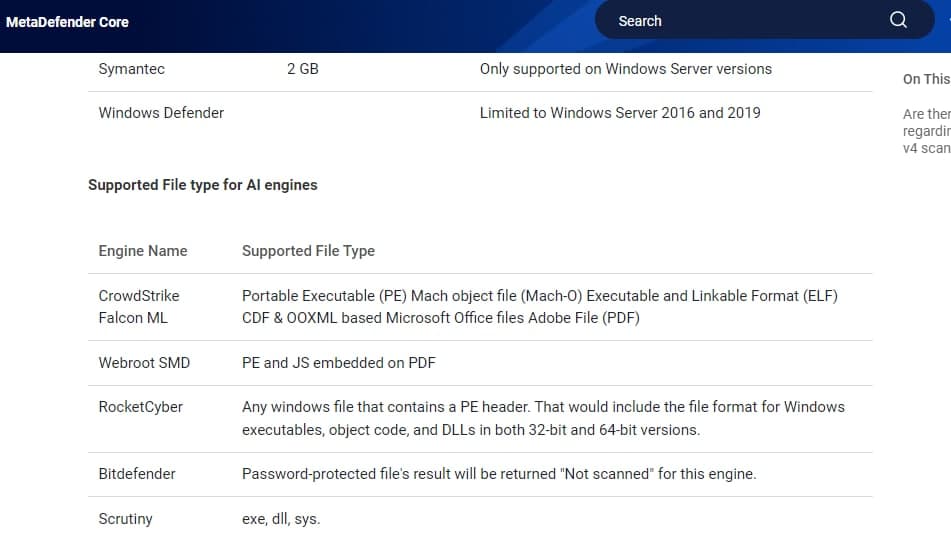
Two key advantages of multi-scanning with Scrutiny sensors include:
Enhanced Detection Rates: By leveraging our new age simulation engine alongside multiple scanning engines, we significantly improve the identification of malware across various attack vectors.
Accelerated Malware Outbreak Detection: Our simultaneous scanning capabilities drastically reduce detection and response times for emerging threats, ensuring timely remediation with high accuracy and reliability.
Simulation Intelligence Drives Our Most Noteworthy Threat Detections
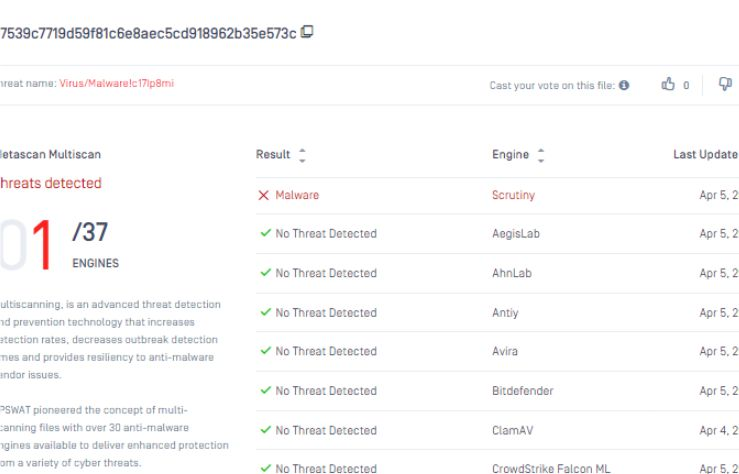
SCRUTINY DETECT FIRST - ZERO DAY MALWARE
After being among the first to detect the sophisticated Daxin malware targeting U.S. critical infrastructure, our research now continually enhances detection models to counter Chinese cyber-attack-oriented malware.
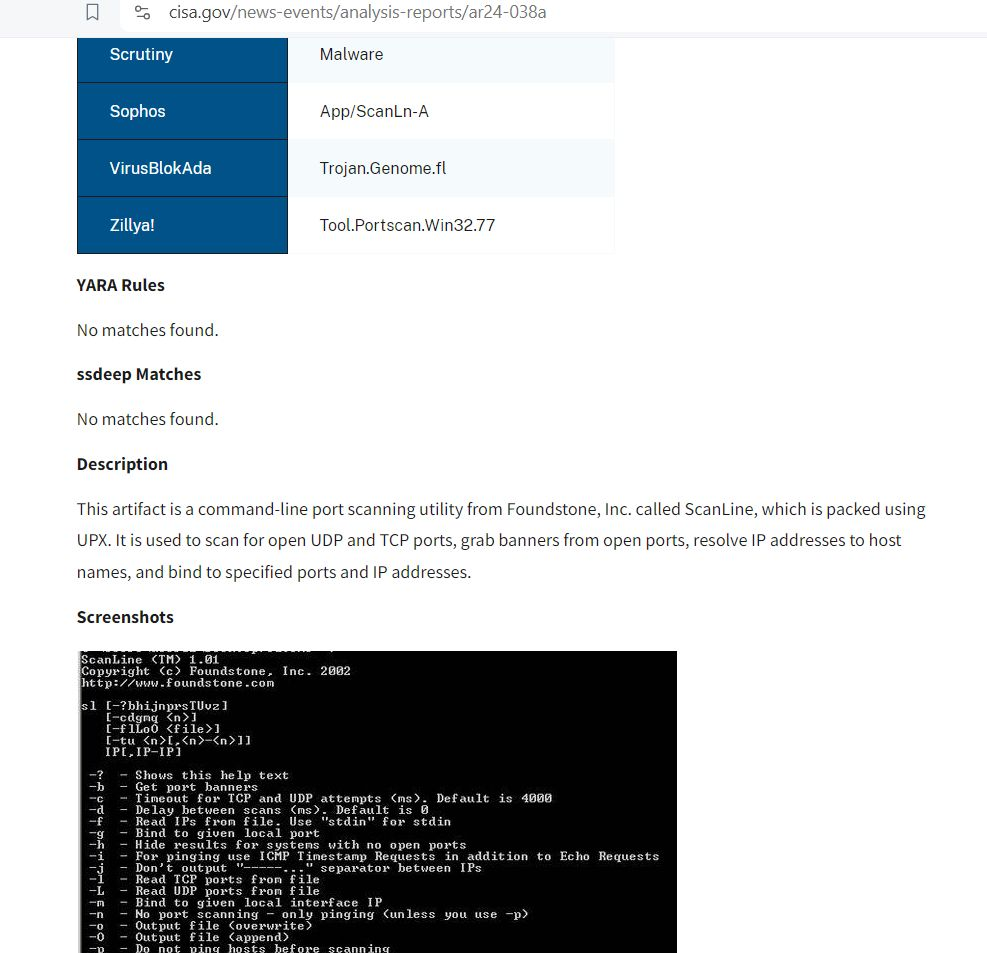
Scrutiny Engine Neutralizes Volt Typhoon Threat to National Security
Ref:
https://www.cisa.gov/sites/default/files/2024-05/MAR-10448362.c1.v2.CLEAR_.pdf
