Indian Ministry of Defense-Themed Trojan: A SideCopy Signature
Recently, a cyber espionage campaign was discovered which targeted Indian defence contractors, aerospace, and research organizations. This campaign used various tactics to compromise its victims and extract sensitive information.
In this blog, we will analyze the two tools used in this campaign - Action RAT and AllaKore RAT, examining their associated command and control (C2) infrastructure. We will also explore the threat telemetry data that surrounds these C2 servers and discuss how the attackers manage their infrastructure.
Overview of the Attack
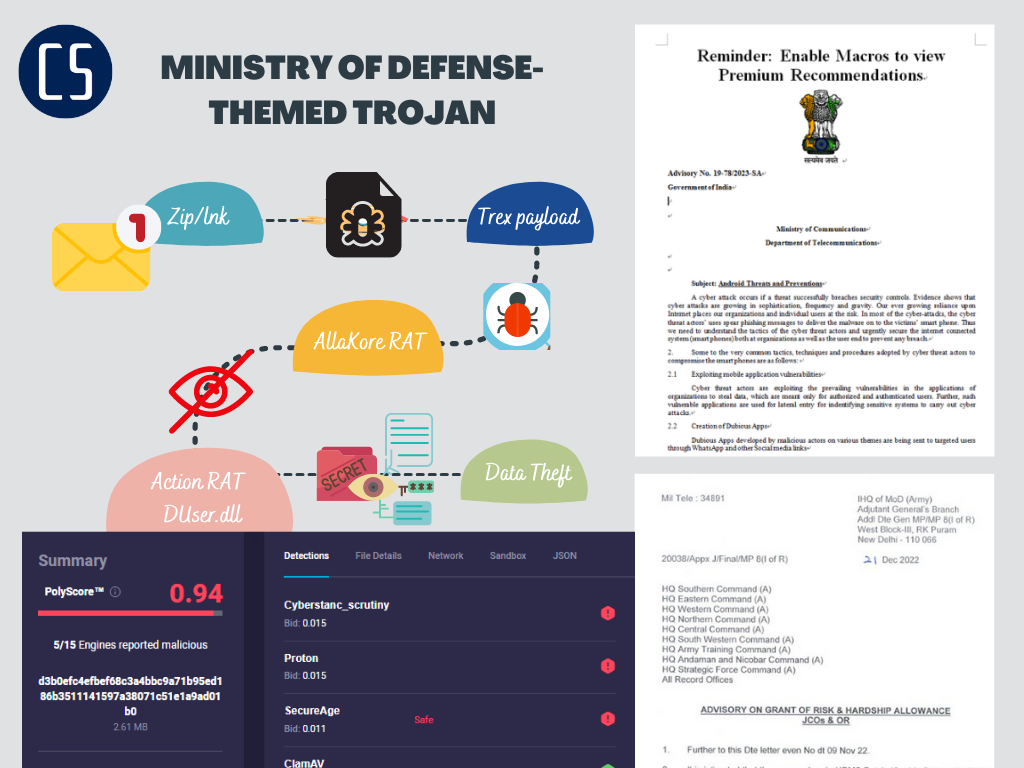
In this attack, the SideCopy group used spear-phishing emails with LNK files in compressed packages as the attack entry point. The LNK file is a malicious file that accesses the command and control (C2) server using mshta.exe in the system to download and execute subsequent payloads. The final payload is an improved open-source Trojan horse written in Delphi or a new Trojan horse written in C++, with the bait content related to the Indian Ministry of Defense.
Spear-phishing and Compressed Packages: The old Tactics of SideCopy Group
The attack process is as follows:
Spear-phishing emails, with LNK files in compressed packages as the attack entry point.
Loading and executing subsequent payloads in memory without files.
The final payload is an improved open-source Trojan horse written in Delphi or a new Trojan horse written in C++.
The bait content is related to the Indian Ministry of Defense.
Outbound Activity Analysis of sidecopy's C2 Server
Phase One : SideCopy Group's Spear-Phishing Emails and Malicious Payloads
The SideCopy group has been using spear-phishing emails as the primary method to deliver their malicious payloads. In this attack activity, they used a compressed multiple package multiple-type "XYZ.zip," which contained a bait LNK file. The LNK file, when clicked, accessed the C2 using mshta.exe to download and execute subsequent payloads.
The link in the LNK file redirected to malicious site which downloaded a piece of JS code to execute. The main function of this JS code was to load DLL in memory, decrypt the embedded data in the JS code through the functions in the DLL, and drop the PDF bait. The function "openthefile" decrypted and released the PDF bait. The displayed PDF bait was related to the Indian Ministry of Defense.

file: ffa2e6f6a7a8001f56c352df43af3fe5 Cyber Advisory 2023.docm
dl-url: http[:]//luckyoilpk[.]com/vlan.html payload
#ReverseRAT (aka #CetaRAT): 0baa1d0cc20d80fa47eeb764292b9e98 CnC: http[:]//185.174.102[.]54:443
The JS code also obtained the information of installed antivirus software, concatenated it with the string "anvaro =," and uploaded it to C2 server using the POST method.
It then created the directory "C:\ProgramData\ABC," accessed the C2 to download data, and saved it in "C:\ProgramData\ABC\jquery.hta" and "C:\ProgramData\ABC\jscy.hta" files, and then executed them.
Phase Two : The Aftermath of the Attack on Quick Heal and Other AV Software
The SearchProducts function compares the antivirus software to decide how to start the subsequent payloads. When the Indian antivirus software "Quick Heal" is present, the first step is to copy Credwiz.exe file in the system to the directory “C:\Users\Public\smitpr” and rename it as “crezly.exe”.
The code checks if the antivirus software is "Quick Heal." If it is, the function performs the following steps:
Copies the Credwiz.exe file to the directory "C:\Users\Public\smitpr" and renames it as "crezly.exe."
Decrypts the DLL data and renames it as "DUser.dll" in the "C:\Users\Public\smitpr" directory.
Decrypts the EXE data and drops the program "simsre.exe" in the "smitpr" directory.
Sleeps for 30 seconds.
Calls the released "crezly.exe" program to side-load the malicious "DUser.dll."
Generates a bat file to add a startup item for the crezly.exe program through the registry.
During the execution, a bat file was generated, which added a startup item for the crezly.exe program through the registry. When the antivirus software was Kaspersky, Avast, Bitdefender, WindowsDefender, or others, the way of releasing the malicious component was basically the same as that of the Indian antivirus software "Quick Heal," except that it slept for one minute and then started the released simsre.exe program directly, and the program added to the startup item through the registry was also simsre.exe.
If the antivirus software is not "Quick Heal," the function performs the following steps:
Sleeps for 1 minute.
Starts the released "simsre.exe" program directly.
Generates a bat file to add a startup item for the "simsre.exe" program through the registry.
Phase Three : AllaKore RAT's File Upload/Download: Accessing Sensitive Information Made Easy
AllaKore RAT, also known as Cyrus, is a remote access trojan that is commonly used by cybercriminals to gain unauthorized access to victim's computers. This RAT has been modified by the SideCopy group and is a variant of the open-source RAT that can bypass most antivirus and endpoint detection and response (EDR) tools. In this technical analysis, we will discuss the capabilities and techniques used by AllaKore RAT to evade detection.
Action RAT is a tool that is used to receive commands from the C2 server, retrieve information from the victim machine, execute further payloads, and upload information back to the C2.
It is dropped onto the victim machine alongside a benign executable which is used to sideload it, in order to avoid detection.
Capabilities of AllaKore RAT
AllaKore RAT has various capabilities that allow attackers to gain complete control over the victim's system.
Some of the main functions of AllaKore RAT are:
Keylogger: AllaKore RAT has a built-in keylogger that can log all the keystrokes made by the victim, including usernames, passwords, and other sensitive information.
Screenshots: AllaKore RAT can capture screenshots of the victim's desktop and send them back to the attacker's C&C server.
List folders and files: AllaKore RAT can list all the files and folders on the victim's computer, giving the attacker a clear idea of the victim's file structure.
Upload/download files: AllaKore RAT can upload and download files from the victim's computer, giving the attacker access to sensitive information.
Steal clipboard data: AllaKore RAT can steal data from the victim's clipboard, including passwords and other sensitive information.
Change wallpaper: AllaKore RAT can change the victim's desktop wallpaper to display a message from the attacker.
Remote control: AllaKore RAT allows the attacker to remotely control the victim's computer, giving them complete access to the system.
Techniques used by AllaKore RAT to evade detection
Code obfuscation: AllaKore RAT uses code obfuscation techniques to hide its malicious code from antivirus and EDR tools.
Fileless execution: AllaKore RAT can execute its code in memory, without creating any files on the victim's system.
Process injection: AllaKore RAT uses process injection techniques to inject its code into legitimate processes running on the victim's system.
C&C communication encryption: AllaKore RAT encrypts its communication with the C&C server using various encryption algorithms, making it difficult to detect its network traffic.
SideCopy Uncovers Transparent Tribe's Latest Cyber Espionage Plot with Indian MoD Theme
Two samples of Action RAT (loaded as DUser.dll).
Stage 1: feeadc91373732d65883c8351a6454a77a063ff5 (DRDO - K4 Missile Clean room.pptx.lnk)
Tags: mshta,lnk,html
www.cornerstonebeverly[.]org, ilovepdf[.]com
Action RAT: 3c4c8cbab1983c775e6a76166f7b3c84dde8c8c5 (DUser.dll)
C2: 144.91.72.17:8080 (Contabo GmbH)


The other sample had the following details:
Stage 1: 0d68a135b1f4be18481cf44ed02bcbf82aeb542e (Cyber Advisory - Profiles (Pic and Mob No) of PIOs.docx.lnk)
C2: www.kwalityproducts[.]com
Action RAT: cb031561fd76643885671922db7d5b840060334d (DUser.dll)
C2: 84.46.250.78:8080 (Contabo GmbH)

Phase 4: Analysis of Outbound Activity from C2 Servers in Action RAT and AllaKore RAT Campaign
In early 2023, a targeted campaign using the Action RAT and AllaKore RAT malware was observed, with all 18 victims located in India. Initial victim connections to the command and control (C2) servers associated with Action RAT were observed on February 6 and March 15, respectively.
Further analysis of outbound activity from the C2 servers revealed connections to IMMEDION, a US provider, via 84.46.250.78. However, WHOIS data indicated that IMMEDION was located in Pakistan, suggesting that actors located in Pakistan were managing the infrastructure. Communication sourced from 17 distinct IPs assigned to Pakistani mobile providers and Proton VPN nodes were observed during the period of interest, indicating the threat actors accessed their infrastructure within a typical working week cadence.
The SideCopy malware campaign has been actively spreading in the wild, targeting victims in India and potentially other regions. The campaign utilizes a DLL-based malware loader and Indian Ministry of Defense-themed Trojan to compromise victims' systems and steal sensitive data.
Our closing remarks on SideCopy's cyber threats
In conclusion, the SideCopy group continues to pose a significant threat to organizations, particularly in India and other countries. Their use of sophisticated tactics such as spear-phishing emails and DLL-based malware loaders highlights their determination to evade detection and compromise their targets.
At Cyberstanc, we remain dedicated to researching and analyzing APT groups such as SideCopy, and providing our clients with advanced cybersecurity solutions to protect against emerging threats. Our Secure-Tech service offers comprehensive internal and third-party application scrutiny scans, using a convenient Pay-As-You-Go model.
SideCopy Trojan Dropper : fa6c832e22f978b8210c0630db69e6a2

We invite you to visit our blog for detailed analysis of APT36 Transparent Tribe and other threat actors, and to contact us at [email protected] to learn more about how we can help protect your organization from cyber threats. Our cutting-edge technologies and commitment to cybersecurity make us a trusted partner in ensuring a safer and more secure digital world for all.
"https://cyberstanc.com/blog/a-look-into-apt36-transparent-tribe/"
IOC Information:
URLs:
https://kcps.edu[.]in/css/fonts/files/docs/graentsodocumentso/ganeshostwoso/snbtoolswires.hta
https://kcps.edu[.]in/css/fonts/files/avena/
https://kcps.edu[.]in/css/fonts/files/ntsfonts/
https://kcps.edu[.]in/css/fonts/files/jquery/
https://www[.]cornerstonebeverly.org/js/files/docufentososo/doecumentosoneso/pantomime.hta
https://cornerstonebeverly[.]org/js/files/ntfonts/avena/
https://cornerstonebeverly[.]org/js/files/ntfonts/
https://hpuniversity[.]in/uploadsssss/files/file2/file2.zip
https://hpuniversity[.]in/uploadsssss/files/file3/file3.zip
https://hpuniversity[.]in/uploadsssss/files/women/Women.zip
https://hpuniversity[.]in/uploadsssss/files/survey/Survry.zip
http://hpuniversity[.]in/filessss/software/SoftWare.zip
https://hpuniversity[.]in/filessss/principles/Principles.zip
https://hpuniversity[.]in/documents/survey/start/2.hta
https://hpuniversity[.]in/documents/women/Women.zip
IPs:
89.117.63.146:9921
185.229.119.60:9134
144.91.72.17:8080
13.107.21.200
40.113.103.199
104.123.111.225
162.159.36.2
184.50.166.121
193.138.218.74
To better protect against this threat, it is important to stay informed about the latest developments and take proactive measures to defend against potential attacks. Researchers should monitor the IOC information provided and report any suspicious activity to relevant authorities.
