Scrutiny vs. AV vs. EDR
The goal of any security control should be to block an attack at the earliest point instead of detecting it and investigating the incident and damage that has been done must not be a priority. So, Why aren’t vendors successfully defending against attacks in the first place?
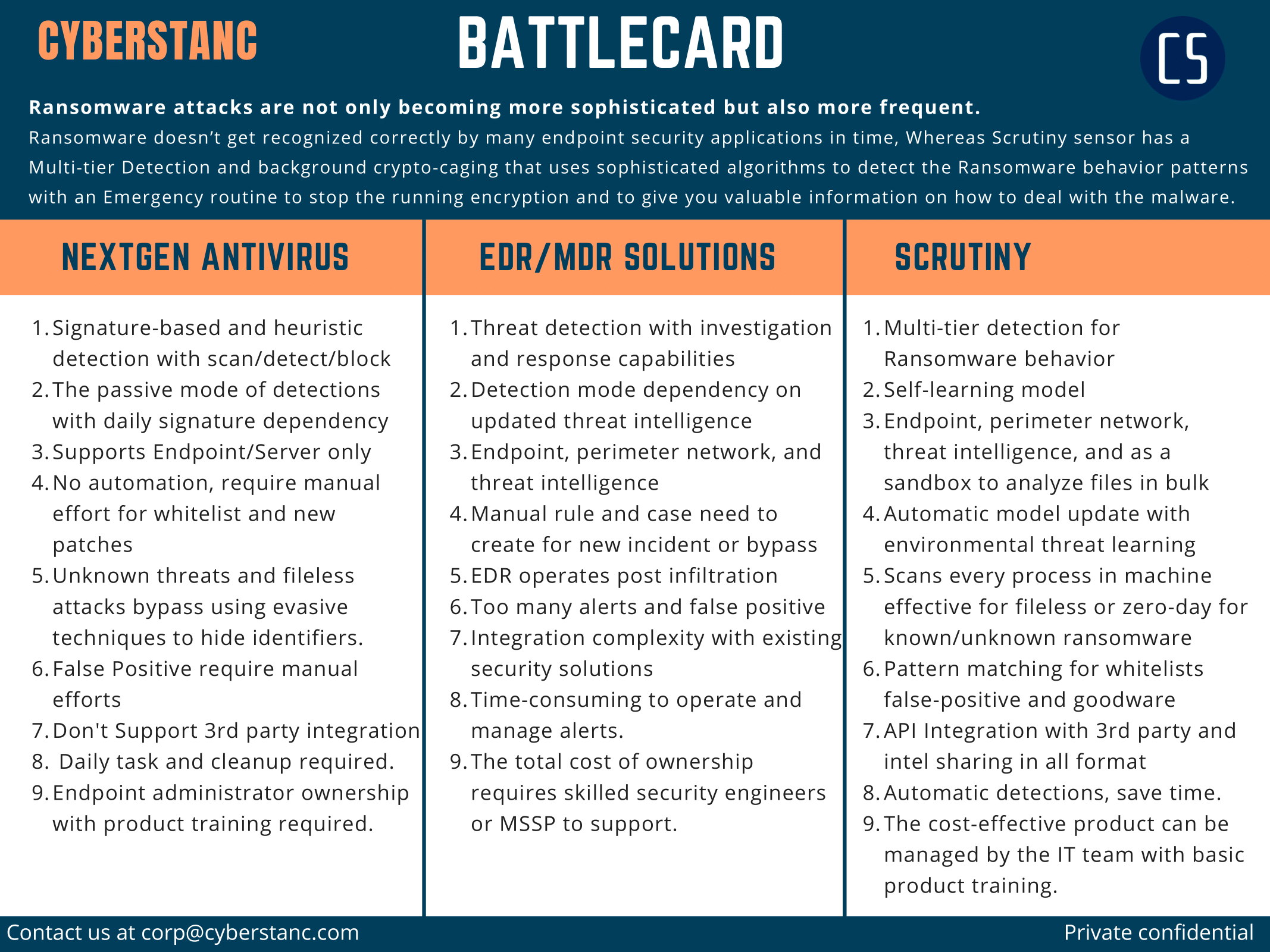
RANSOMWARE SIMULATIONS WITH EDR SOLUTIONS
Regardless of the AV/EDR claims, We have test EDR with the latest known and unknown Ransomware sample. Asterbox helps here to simulate ransomware to validate vendor effectiveness and helps to check cybersecurity readiness.
Windows 10 machine, ransomware samples were shared and collected via closed source and the outcome was evaluated by Asterbox ransomware simulation platform, tracking if the file was executed, for how long, and if it was stopped.
EDR Solution 1
· 20/50 stopped by EDR detection method or threat intelligence.
· 18/50 samples executed for more than 5 seconds and stopped by machine learning module.
· 12/50 samples executed successfully and encrypted files, 4 obfuscated known samples, and 6 unknown ransomware.
EDR solution 2
· 26/50 stopped by EDR detection or threat intelligence.
· 14/50 samples executed for more than 5 seconds and stopped by real-time protection.
· 10/50 samples executed successfully and encrypted files, 2 obfuscated known samples, and 6 unknown ransomware.
Scrutiny anti-ransomware sensor
· 32/50 stopped by scrutiny's dataset or threat intelligence.
· 18/50 samples executed for more than 5 seconds, ransomware detected by pattern matching and crypto caging with multi-tier layer protection.
None sample able to encrypts a file, As routine to check any such anomalies.
Why Threat landscape need to automate?
Increased visibility means an increased amount of data, and consequently an increased amount of analysis. Because of this, most EDR solutions available today are not scalable. They require too many resources that are in short supply, namely time, money, bandwidth, and a skilled workforce.
In many cases, vendors requires cloud connectivity, and as such will be late with protecting endpoints and whole network. Waiting for a response from the cloud or for an analyst to take action in a timely manner is simply not feasible in the modern threat scape. A successful attack can compromise a machine, exfiltrate and encrypt data, and remove traces of itself in fractions of a second.
Contact us at corp@cyberstanc for ransomware assessment and scrutiny sensor demo!!
