A Cyber Espionage Campaign Targeting Japan, India and Taiwan with Deadly Malware!
Cybersecurity is an ever-evolving field, with new forms of malware and attack techniques emerging every day. In this fast-paced environment, it's essential to have a robust detection system in place that can identify and mitigate these threats quickly and efficiently. In this article, we'll explore how the use of simulated intelligence and CDR technology can help organizations build a detection system that can detect advanced malware and new forms of attacks.
One recent example of the need for such scrutiny can be found in the case of a banking malware campaign in Japan and Indo-Pacific region. This APT campaign involved the use of a sophisticated malware strain that was designed to steal sensitive financial information from unsuspecting victims. In order to detect and prevent such attacks, it is crucial to develop advanced detection methods and tag potential threats quickly and accurately.
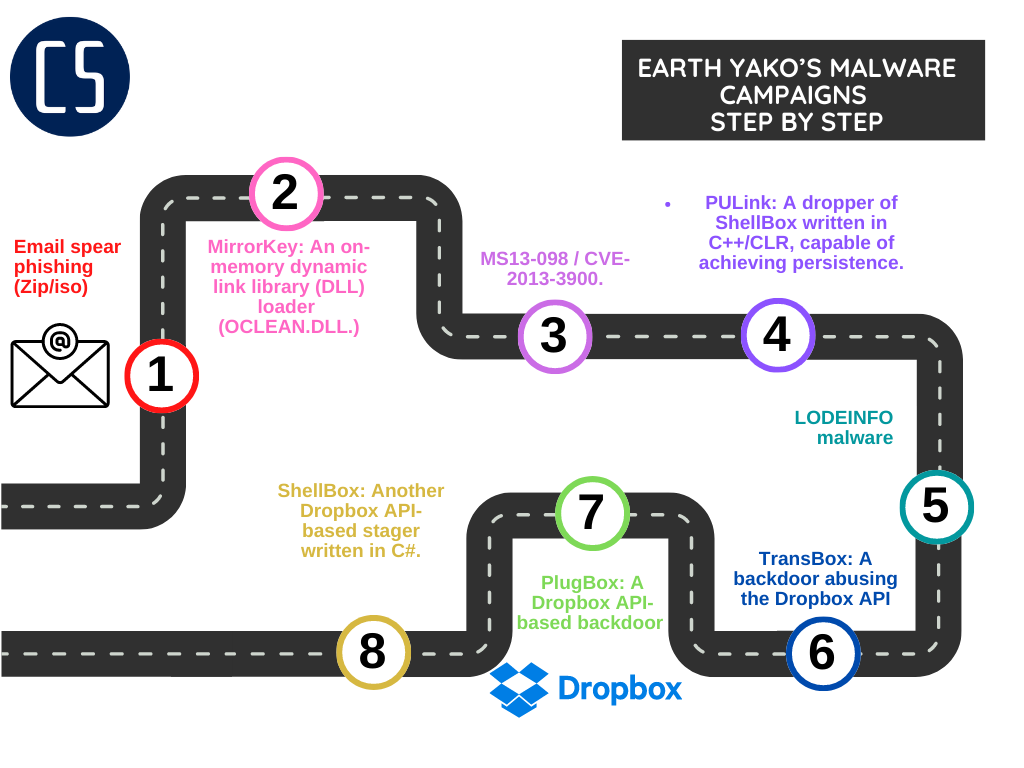
Earth Yako is a cyber espionage campaign that targets organizations in Japan, India and Taiwan. The campaign uses various malware, including PlugBox, TransBox, and ShellBox, which all abuse the Dropbox API.
ShellBox, in particular, uses a stager written in C++ that complicates the process of obtaining an access token, making it harder for security analysts to investigate. The malware downloads an encrypted .NET assembly from Dropbox, decrypts it, and executes it in memory.
The attackers used a hardcoded GitHub repository to host the URL for the Dropbox Access Token. Earth Yako shares technical similarities with APT10, and APT29, but there is no strong evidence to attribute the campaign to any of these groups.
The campaign's target sectors and the themes used in lures suggest a focus on economic security, energy sector, and international affairs. The timeline offers a detailed analysis of the various tactics and techniques used in the campaign, the GitHub account used by the attackers.
------------------------------------------------------------------------------------------
Cyberstanc's Scrutiny is the only malware detection engine to 🚨 detect Transbox malware at early stage with simulated intelligence🤖 !
------------------------------------------------------------------------------------------
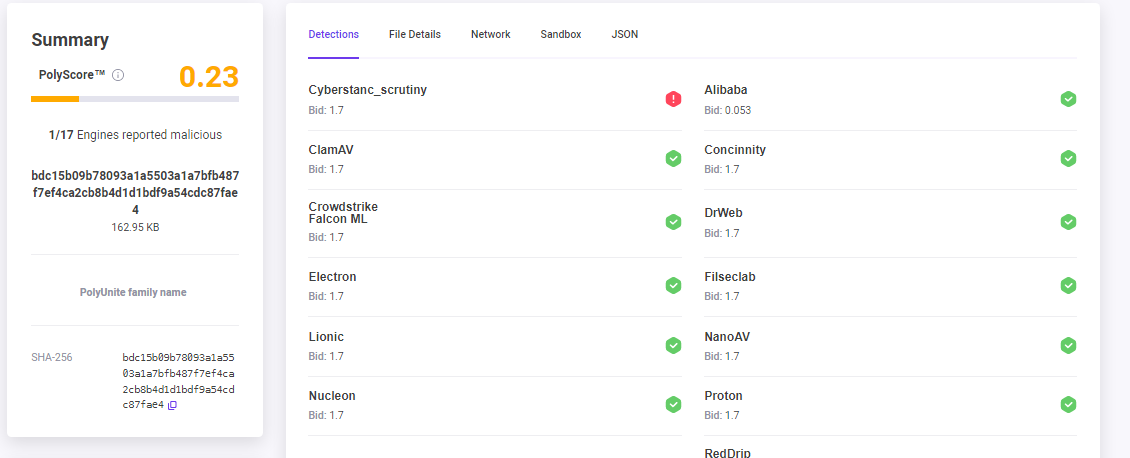
Polyswarm Link:- First Seen 2022-09-07 https://polyswarm.network/scan/results/file/bdc15b09b78093a1a5503a1a7bfb487f7ef4ca2cb8b4d1d1bdf9a54cdc87fae4
VT LINK:- First Seen 2023-02-28 (https://www.virustotal.com/gui/file/bdc15b09b78093a1a5503a1a7bfb487f7ef4ca2cb8b4d1d1bdf9a54cdc87fae4/detection)
REDLINE STEALER
Beware of Redline Stealer malware! This sneaky thief steals your sensitive information 💸🔑
Watch out for phishing emails, infected software downloads, or malicious websites delivering the malware. Stay vigilant! 🕵️♂️ 📈
Redline Stealer uses strong encryption to hide its payload and avoid detection. Don't let it slip through the cracks
Redline Stealer creates a persistent presence on your device. Don't let it in the door!
------------------------------------------------------------------------------------------

------------------------------------------------------------------------------------------
------------------------------------------------------------------------------------------
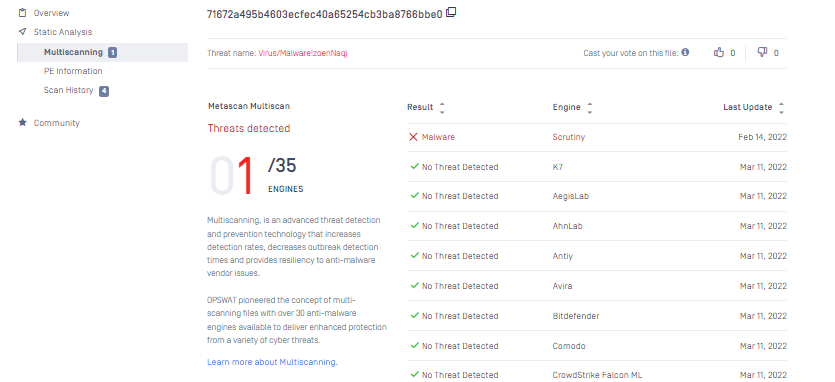
OPSWAT : First Seen Feb 14, 2022 https://metadefender.opswat.com/results/file/3e26723394ade92f8163b5643960189cb07358b0f96529a477d37176d68aa0a0/hash/overview
------------------------------------------------------------------------------------------
The Scrutiny of Detection Intelligence through Hybrid Analysis Lab, Joe Sandbox, and other Malware Classification Enrichment Platform.
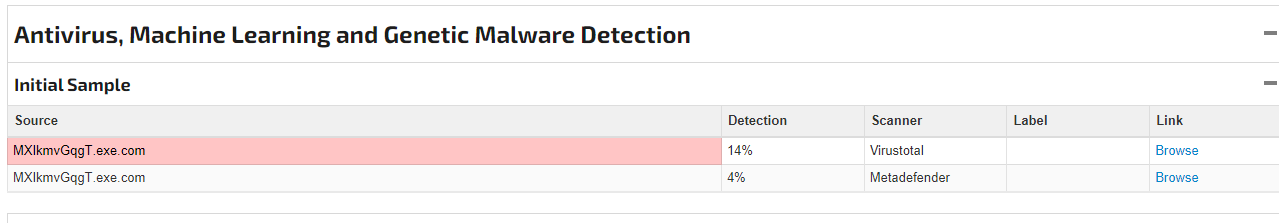
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
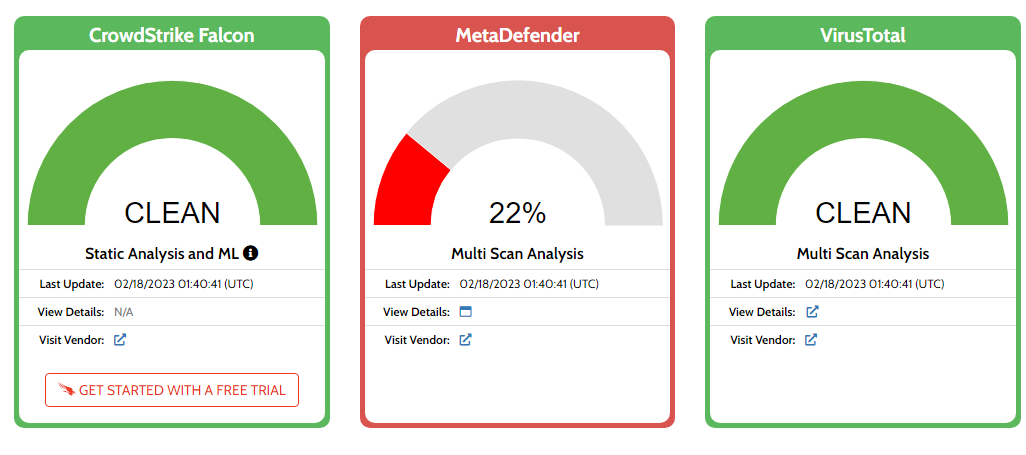

------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
This is precisely the kind of work being done by the CyberStanc R&D center, which has created a continuous war room to focus on developing cutting-edge detection technologies.
TTPs (Tactics, Techniques, and Procedures) are the methods and strategies used by cyber attackers to compromise a system. By understanding these TTPs, security analysts can develop detection mechanisms that can identify and block malicious activities. However, the challenge is to keep up with the rapidly evolving TTPs, which is why self-curation is essential.
This list can then be used to develop detection mechanisms that can identify new attacks that use these TTPs. By continuously monitoring and updating the list, security analysts can stay ahead of new threats and build a more robust detection system.
Simulated intelligence is a technique that involves creating a simulated environment to train a detection system. This technique is particularly useful in detecting new forms of attacks that traditional detection methods may not be able to identify. By using simulated environments to train the detection system, security analysts can expose it to a wide range of attack scenarios and fine-tune its response to different types of threats.
One of the advantages of using simulated intelligence is that it can help reduce false positives. False positives occur when a detection system identifies a legitimate activity as malicious, leading to unnecessary alerts and wasted resources. By using simulated intelligence to train the detection system, security analysts can reduce the number of false positives, making it more efficient and reliable.
CDR (Content Disarm and Reconstruction) technology is designed to provide comprehensive protection against a wide range of cyber threats, including zero-day attacks, advanced persistent threats (APTs), and other sophisticated malware. Military-grade CDR technology takes this protection to the next level by incorporating advanced features like AI-powered analysis, behavior monitoring, and real-time threat intelligence.
WHY CHOOSE CYBERSTANC
As cyber threats continue to evolve, it is important for organizations to invest in advanced cybersecurity solutions that can keep pace with these changes. By adopting a proactive approach to cybersecurity, organizations can reduce their risk of a costly data breach and maintain the trust of their customers and stakeholders.
Our R&D center is constantly developing cutting-edge technologies ⚙ to fight against malicious software and APTs.
A Strong Partnership for Gathering Scrutiny Engine Detection Intelligence With the right tools 🛠 and strategies , they are staying ahead of the curve to ensure a safer and more secure digital world.
Unlock the full potential of your security with Scrutiny's free trial - 31 days of powerful threat intelligence, malware detection, and analytics at no cost. Try it now and see the difference for yourself. Connect us for Secure-Tech to check for internal and 3rd party applications scrutiny scan, Detections Pay-As-You-Go model !!
🚨 💻🔐 [email protected] 🚨 💻🔐
------------------------------------------------------------------------------------------

